GoIssue Targets GitHub Users with Mass Phishing Attacks
Overview of the GoIssue Threat
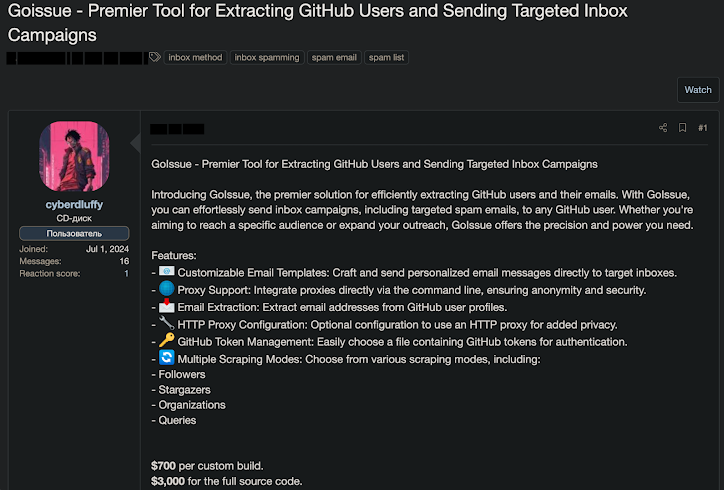
Recently, cybersecurity experts identified a new tool called GoIssue, an application that enables cybercriminals to send phishing messages on a massive scale, specifically targeting GitHub users. GoIssue initially appeared on the dark web forum Runion, promoted by a threat actor known as “cyberdluffy” or “Cyber D’ Luffy.” This tool claims to harvest email addresses from public GitHub profiles and send bulk phishing emails directly to user inboxes.
You might be interested in: AndroxGh0st Expands Reach by Exploiting Security Flaws
According to the creator, GoIssue offers “precision and power” for delivering phishing emails, allowing attackers to either target a specific audience or reach a broad range of recipients. The tool’s mass emailing capability raises concerns about widespread phishing attacks aimed at developer communities.
Potential Security Risks of GoIssue
SlashNext has highlighted GoIssue as a “dangerous advancement in targeted phishing” that could lead to severe security incidents, including supply chain breaches, source code theft, and unauthorized access to corporate networks. Using GoIssue, attackers can customize their phishing emails to evade spam filters and directly target developers, who are often the gatekeepers to sensitive systems and data.
Pricing and Availability: The tool is currently being offered for $700, with the option to buy the entire source code for $3,000. For a limited time, the creator is offering custom builds and full source code at a discount—$1,000 and $150, respectively, for the first five customers.
GoIssue’s Method of Attack
GoIssue’s phishing strategy involves several sophisticated tactics:
- Tagging Developers: Compromised GitHub accounts are used to tag developers in spam comments on various issues and pull requests. This tactic triggers email notifications from GitHub containing malicious URLs.
- Phishing Through OAuth: Developers are lured into logging into fake GitHub pages where they unknowingly authorize a rogue OAuth app. Once granted permission, the app gains access to the developer’s sensitive data and repositories.
- Ransom Tactics: If a user unknowingly authorizes the app, attackers can delete the repository contents and replace them with a ransom demand, asking for payment via Telegram.
Who Is Cyber D’ Luffy?
The individual behind GoIssue, cyberdluffy, claims on their Telegram profile to be affiliated with the “Gitloker Team.” This group was previously linked to extortion schemes targeting GitHub users, where attackers pretended to be security or recruitment staff to trick users into visiting malicious websites.
Recent Developments: Two-Stage Phishing Technique
In addition to GoIssue, researchers at Perception Point have uncovered a new two-step phishing technique. This method uses Microsoft SharePoint and Visio (.vsdx) files to capture login credentials. In these attacks, phishing emails are sent from compromised accounts, with the email appearing as a legitimate business offer. Upon clicking a link in the email or within an attached file, the victim is redirected to a phony Microsoft 365 login page embedded within a Visio document, where they are prompted to enter their credentials.
Conclusion
Phishing attacks using tools like GoIssue, combined with multi-stage tactics that exploit trusted platforms, mark a rising threat in the cybersecurity landscape. Users are encouraged to stay vigilant, especially when interacting with unfamiliar links or files from platforms like GitHub and SharePoint.


