Free Bitdefender Solution for ShrinkLocker Ransomware
Free Tool from Bitdefender Helps ShrinkLocker Ransomware Victims Recover Encrypted Files
Bitdefender’s Free Decryptor Tool
Romanian cybersecurity company Bitdefender has introduced a free tool to assist victims of the ShrinkLocker ransomware in recovering encrypted data. After closely examining the ransomware’s inner workings, Bitdefender’s researchers found a specific moment in the decryption process that allows for data recovery, particularly after removing protections on BitLocker-encrypted drives.
You might be interested in: AndroxGh0st Expands Reach by Exploiting Security Flaws
How ShrinkLocker Targets Devices
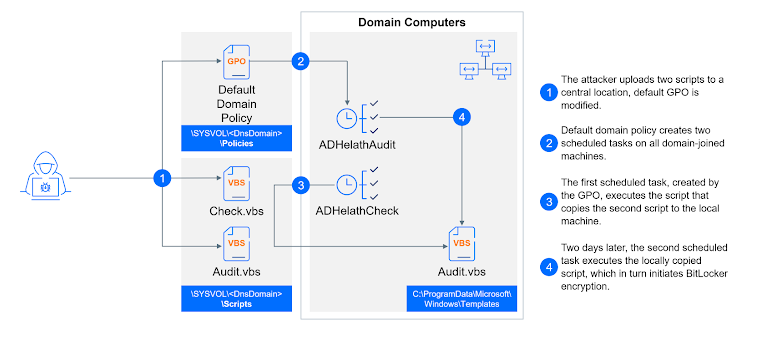
ShrinkLocker uses Microsoft’s BitLocker feature, typically meant for securing files, to lock victims’ files as part of a ransomware scheme. First observed by Kaspersky in May 2024, ShrinkLocker has primarily targeted individuals and organizations in Mexico, Indonesia, and Jordan. Bitdefender became involved after a ShrinkLocker attack against an unnamed healthcare company in the Middle East, discovering that the ransomware likely entered through a contractor’s compromised device. This aligns with a growing trend of attackers breaching supply chains by misusing trusted business relationships.
Once inside, attackers created two scheduled tasks to activate the ransomware across the system. The first task, “Check.vbs,” spread the ransomware to every connected device in the domain, while the second, “Audit.vbs,” was set to run two days later to trigger the ransomware itself. Bitdefender confirmed that ShrinkLocker encrypted devices running on Windows 10, Windows 11, Windows Server 2016, and Windows Server 2019, using a modified version of the original malware.
A Simple but Effective Ransomware Method
ShrinkLocker operates using Visual Basic Script (VBScript), a basic scripting language. Although Microsoft plans to phase out VBScript in late 2024, the ransomware uses it effectively to exploit BitLocker instead of employing its own encryption method. After collecting data on the system, it determines if BitLocker is present. If not, it installs BitLocker using a PowerShell command and then forces the device to reboot.
However, Bitdefender uncovered a flaw in the malware: the script can get stuck in an endless loop due to a failed reboot attempt, displaying a “Privilege Not Held” error. According to Martin Zugec, Bitdefender’s technical solutions director, this glitch can stop the attack if the script fails to restart after the reboot, potentially halting the infection if an administrator restarts the device manually.
How ShrinkLocker Encrypts Drives
ShrinkLocker generates a unique password for each infected system, using details such as network traffic, memory, and disk activity. This password is sent to a server controlled by the attackers. After rebooting, victims are asked to enter this password to unlock their encrypted data. The ransomware displays an email address on the BitLocker screen, prompting victims to contact the attackers for ransom payment instructions.
Additionally, ShrinkLocker makes several changes to restrict system access, including disabling local password-based logins and blocking RDP (Remote Desktop Protocol) access. It also disables Windows Firewall rules and deletes system audit files to cover its tracks.
Misleading Name and Rapid Attack Capabilities
Bitdefender noted that the name “ShrinkLocker” is misleading, as the ransomware does not actually shrink system partitions on modern Windows systems, though it may do so on older versions. Using Group Policy Objects (GPOs) and scheduled tasks, ShrinkLocker can encrypt devices across a network in around 10 minutes each, allowing attackers to compromise an entire domain quickly and with minimal effort.
Tips for ShrinkLocker Protection
Organizations can protect themselves by proactively monitoring Windows event logs for signs of BitLocker activity. Detecting such activities early can alert teams to a potential ransomware attack. Additionally, by configuring BitLocker to save recovery data in Active Directory Domain Services (AD DS), organizations can reduce the risk of attacks. Setting BitLocker to delay activation until this recovery information is saved in AD DS is also recommended for extra security.
