New Malware Campaign Targets GodLoader
Godot Engine Exploited in GodLoader Malware Attack
A new malware campaign known as GodLoader is making waves, infecting more than 17,000 computers since June 2024. The attack takes advantage of the popular Godot Engine, an open-source game development platform. Cybercriminals are using the engine’s scripting language, GDScript, to run malicious code that deploys malware on affected systems. According to a report from Check Point, this attack is evading detection by almost all antivirus tools.
What Makes Godot Engine Vulnerable?
Godot Engine is widely used to create games for different platforms, including Windows, macOS, Linux, Android, iOS, and even consoles like PlayStation and Xbox. Its versatility makes it an attractive target for cybercriminals, as malware developed using Godot can spread across multiple systems without raising alarms.
The engine’s open-source nature has contributed to its popularity, but also makes it a prime target for malicious activity. Eli Smadja, a security expert at Check Point, pointed out that the platform’s flexibility is now being used against its users, allowing malware like GodLoader to infect a wide variety of devices.
The GodLoader Campaign: How It Works
The attackers are using Godot Engine to create custom executable files, known as .PCK files, which are often used in Godot-based games. These files are then crafted to load GodLoader, a malware tool that downloads further malicious payloads. Among the payloads are RedLine Stealer, a tool for stealing personal data, and XMRig, a cryptocurrency miner.
What makes this attack even more dangerous is that GodLoader is specifically designed to avoid detection. It has built-in capabilities to bypass security analysis, even in virtual environments or sandboxes. Additionally, it adds the entire *C:* drive to the exclusions list of Microsoft Defender Antivirus, making it much harder for the malware to be detected.
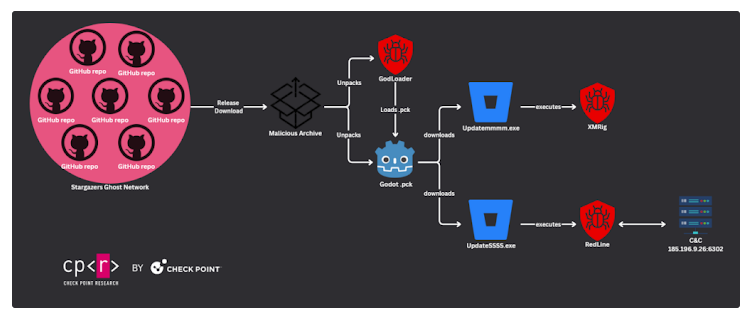
Using GitHub to Distribute GodLoader
The attackers are using a unique distribution method called the Stargazers Ghost Network, which operates through fake GitHub accounts. These accounts have been used to “star” malicious repositories, making them appear legitimate and trustworthy. The malware was released in four separate waves between September and October 2024, targeting developers, gamers, and general users alike.
Once a victim downloads a malicious .PCK file from one of these repositories, the GodLoader malware is executed. It then downloads the final-stage payloads from Bitbucket, which include the RedLine Stealer and XMRig.
Cross-Platform Threat
While the primary target of this campaign is Windows devices, Check Point also notes that the malware could easily be adapted to target other operating systems like macOS and Linux. This flexibility makes the malware even more dangerous, as it can affect a wider range of devices.
In some cases, the attackers have taken it a step further by tampering with legitimate Godot-built games. By obtaining the encryption key used to secure the game’s data, they can extract and modify the .PCK files, further increasing the attack’s reach.
How to Defend Against GodLoader
One way to protect against this type of attack is to use asymmetric encryption, also known as public-key cryptography, instead of symmetric encryption. This would make it much harder for attackers to tamper with game files without the proper decryption key.
In addition, users should always download software from trusted sources. The rise of malware campaigns like GodLoader highlights the importance of being cautious about the software you install, even if it comes from an open-source platform like Godot Engine.
Conclusion: A Wake-Up Call for the Gaming Industry
This attack serves as a reminder of the dangers posed by legitimate platforms being exploited for malicious purposes. As the gaming industry continues to grow, so do the risks of cyberattacks targeting both developers and players. Companies and users must adopt proactive, cross-platform security measures to stay one step ahead of increasingly sophisticated cybercriminals.
