New Social Engineering Attack Uses Microsoft Teams to Spread DarkGate Malware
Overview of the Attack
A recent social engineering attack has been spotted, using Microsoft Teams to help spread the DarkGate malware. According to cybersecurity experts Catherine Loveria, Jovit Samaniego, and Gabriel Nicoleta from Trend Micro, the attackers impersonated a trusted user’s client during a Microsoft Teams call, tricking the victim into downloading malicious software.
You might be interested in: Apple Updates iOS and macOS to Patch Flaw
The Attack Process
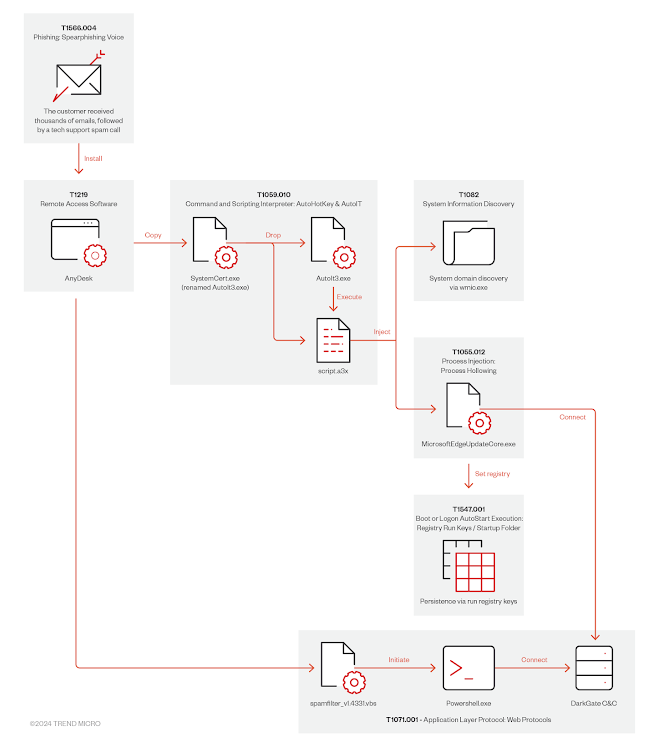
The attackers initially flooded the victim’s email inbox with thousands of messages. Following this, they reached out through Microsoft Teams, pretending to be a representative of an external supplier. They asked the victim to download AnyDesk, a remote access tool, rather than a legitimate Microsoft Remote Support app. Once AnyDesk was installed, the attacker gained remote access to the system and deployed several harmful payloads, including DarkGate.
DarkGate: What Is It?
DarkGate is a powerful remote access Trojan (RAT) that has been in use since 2018. Over time, it has evolved into a malware-as-a-service (MaaS) offering with a limited number of customers. This malware allows attackers to steal credentials, log keystrokes, capture screens, record audio, and even access the victim’s desktop remotely.
Technical Details of the Attack
The campaign that Trend Micro investigated used an AutoIt script to spread DarkGate. Researchers found that this attack is part of a broader trend, where hackers are using different methods to gain access to systems. While the attack was stopped before any data could be stolen, it shows how varied and sophisticated these campaigns can be.
Preventing Future Attacks
To protect against this type of attack, experts recommend that businesses use multi-factor authentication (MFA), only allow trusted remote access tools, block unverified programs, and carefully vet third-party support providers. These steps can help prevent attackers from gaining access to sensitive systems.
Increasing Phishing Campaigns
This attack is part of a larger wave of phishing campaigns that are becoming more common. Cybercriminals use various tactics to trick people into giving away personal information. Some of the most popular methods include:
- Sending fake emails from trusted brands to lure victims into clicking links that lead to malware downloads.
- Using QR codes in phishing emails to direct users to fake login pages.
- Creating fake websites that look like legitimate login pages for Microsoft 365 or other services to steal credentials.
- Sending phishing emails disguised as invoices or other official documents with malicious links.
Other Common Phishing Strategies
Phishers are also using well-known platforms like DocuSign and Google AMP to trick users into clicking malicious links. In some cases, fake emails claim to be from companies like Okta, attempting to steal login details. There have even been phishing attempts through WhatsApp, targeting users in India by offering fraudulent banking apps to download.
Cybercriminals Exploit Global Events
Cybercriminals often exploit global events, such as sports tournaments or product launches, to increase the effectiveness of their phishing campaigns. By registering domains that mimic official websites, they can deceive victims into buying fake merchandise or services. Experts from Palo Alto Networks have warned that businesses should monitor domain registrations and other online activity to identify and stop these scams early.
Conclusion
As phishing and social engineering attacks become more advanced, organizations need to be extra vigilant. Using a combination of strong security protocols, employee training, and awareness of current threats can help reduce the risk of falling victim to these types of attacks.


