Hackers Use cnPilot Flaw for DDoS Attacks
A new variation of the AISURU botnet, called AIRASHI, has been discovered by cybersecurity firm QiAnXin XLab. The botnet is exploiting a previously unknown vulnerability in Cambium Networks’ cnPilot routers to carry out massive distributed denial-of-service (DDoS) attacks. This vulnerability was first noticed in June 2024, but the specific details about the flaw have been kept secret to prevent further exploitation.
You might be interested in: Cybercriminals Use Python Backdoor to Deploy RansomHub Ransomware
Other Affected Devices and Vulnerabilities
In addition to the Cambium Networks’ routers, the AIRASHI botnet is using several well-known security flaws in other devices. These include vulnerabilities in AVTECH IP cameras, LILIN DVRs, and Shenzhen TVT devices. Some of the CVE numbers affected are CVE-2013-3307, CVE-2016-20016, CVE-2017-5259, CVE-2018-14558, CVE-2020-25499, CVE-2020-8515, CVE-2022-3573, CVE-2022-40005, CVE-2022-44149, and CVE-2023-28771.
Attack Power and Target Locations
The AIRASHI botnet has shown a stable DDoS attack capacity ranging between 1-3 terabits per second (Tbps). The main targets of these attacks include countries like China, the United States, Poland, and Russia, while the majority of compromised devices are located in Brazil, Russia, Vietnam, and Indonesia.
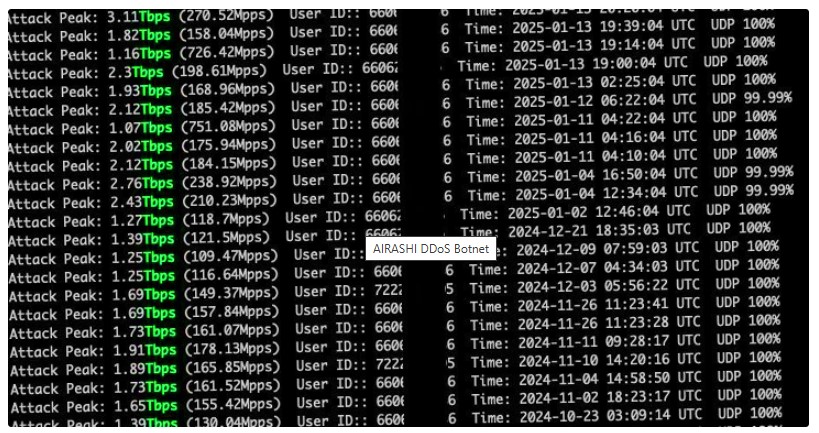
Discovery and Development of AIRASHI
AIRASHI was first noticed in August 2024 after a DDoS attempt against Steam, which occurred around the same time as the release of the game Black Myth: Wukong. This botnet, which is a variant of the AISURU (also called NAKOTNE) botnet, has been updated multiple times, adding new features and capabilities. In September 2024, AISURU briefly stopped its operations but returned in October with new features called “Kitty.” By the end of November 2024, it evolved into AIRASHI.
Different Versions of AIRASHI
AIRASHI comes in two main versions:
- AIRASHI-DDoS: This version focuses on carrying out DDoS attacks, but it also allows for arbitrary command execution and reverse shell access.
- AIRASHI-Proxy: A modified version of AIRASHI-DDoS, this variant includes proxy capabilities, which were first discovered in early December 2024.
Both versions use a new network protocol based on HMAC-SHA256 and CHACHA20 encryption for communication. The botnet also frequently adapts its methods to retrieve control server information using DNS searches. While AIRASHI-Proxy only supports five types of messages, AIRASHI-DDoS supports thirteen.
Proxyware Capabilities and Growing DDoS Threats
AIRASHI has also added proxyware features, signaling that the attackers may offer additional services beyond DDoS attacks. This suggests that AIRASHI may be used for a variety of malicious activities, including illicit proxy services.
Rising Threat from Other Botnets
This discovery comes shortly after QiAnXin reported another botnet called alphatronBot. This cross-platform backdoor has been used to turn compromised Windows and Linux systems into a botnet, mainly targeting Chinese government agencies and businesses. AlphatronBot operates with a decentralized structure, making it harder for authorities to shut it down. Infected devices include MikroTik routers, Hikvision cameras, D-Link routers, and more, spread across 80 countries.
Additional Malware and Payload Systems
Last year, XLab uncovered a sophisticated malware delivery system called DarkCracks. This system uses compromised WordPress and GLPI websites to serve as downloaders and command-and-control (C2) servers. The malware’s goal is to steal sensitive data and maintain long-term access to infected devices, which may include critical infrastructure such as school websites, public transport systems, and prison visitor systems.
Conclusion
These developments show that attackers are continuing to exploit weaknesses in IoT devices to build botnets that support powerful DDoS attacks. The evolving nature of AIRASHI and the discovery of other malicious botnets like alphatronBot and DarkCracks highlight the growing complexity and threat posed by cybercriminals.
