RansomHub Leads Ransomware Attacks in 2024
RansomHub’s Increasing Global Impact
In recent reports, experts have highlighted the rise of the RansomHub ransomware-as-a-service (RaaS) group, which has been utilizing flaws in the Netlogon protocol and Microsoft Active Directory to escalate privileges and gain unauthorized access to victim networks. This group has already targeted more than 600 organizations globally across various sectors, including healthcare, finance, government, and critical infrastructure, making it one of the most active ransomware threats in 2024.
You might be interested in: Understanding the Security Operations Center
The RansomHub group took advantage of a source code linked to the now-defunct Knight (previously Cyclops) RaaS gang, which surfaced in early 2024. By mid-year, the gang released an updated version of its locker that could encrypt data remotely using the SFTP protocol. This new version is capable of encrypting files on various systems, including SFTP servers, Windows, and VMware ESXi. Additionally, RansomHub has been seen forming alliances with other groups, such as LockBit and BlackCat, to enhance its reach and impact.
Attack Techniques and Exploitation of Vulnerabilities
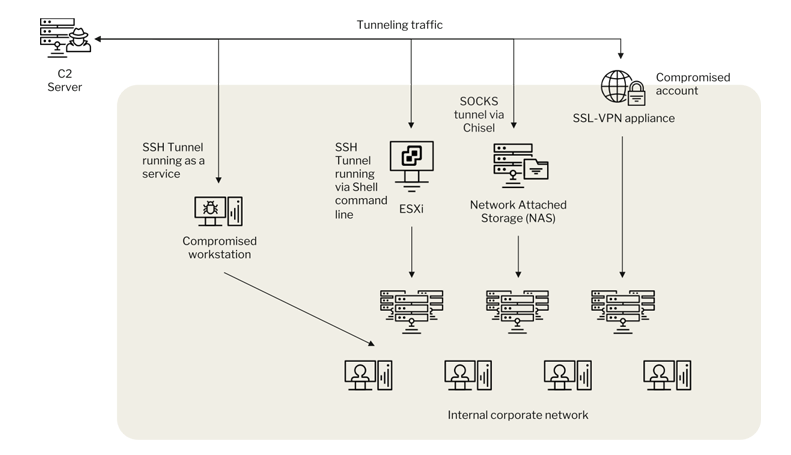
The group’s approach often begins by attempting to exploit known security flaws, such as the CVE-2024-3400 vulnerability in Palo Alto Networks PAN-OS devices. In one particular incident, the attackers tried using a public proof-of-concept (PoC) for the vulnerability but ended up using brute-force techniques against the victim’s VPN service. After several failed attempts, the attackers managed to gain access through a default account used for data backups.
Once inside, RansomHub utilized vulnerabilities in Active Directory (CVE-2021-42278, known as noPac) and Netlogon (CVE-2020-1472, known as ZeroLogon) to escalate their privileges and take control of the victim’s domain controller. This allowed them to freely move across the network, exfiltrating and encrypting sensitive data.
The Attack’s Execution and Final Stage
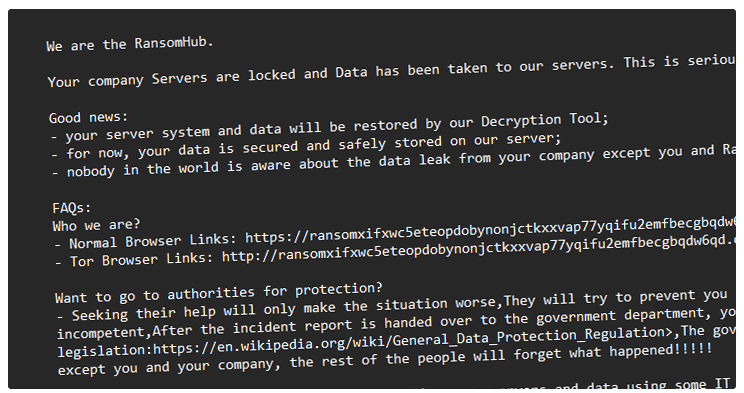
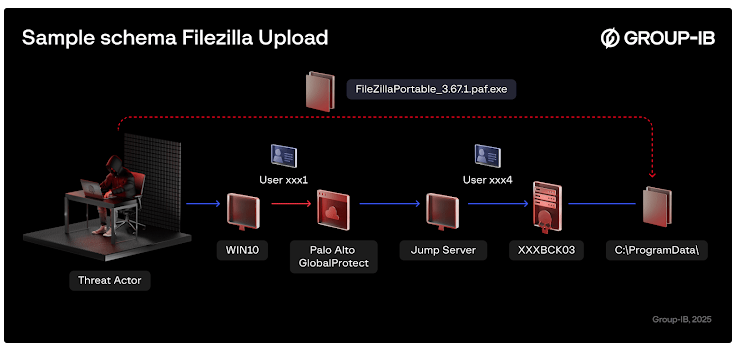
After the initial breach, the attackers carried out both data encryption and exfiltration within 24 hours. They further escalated the attack by rendering all firm data on network-attached storage (NAS) devices inaccessible, making it nearly impossible for the victim to recover the data without paying the ransom. Filezilla was used for data exfiltration, while PCHunter was deployed to bypass endpoint security tools.
The Evolution of the Cybercrime Ecosystem
RansomHub’s operations illustrate the complex ecosystem of cybercrime, where various groups share tools and resources to enhance their capabilities. The RaaS market thrives on this collaboration, with actors constantly exchanging and rebranding malicious code to improve their chances of success. Cybersecurity experts emphasize that the underground market is highly profitable, with high-profile victims and large sums of money playing a central role.
New Trends in Ransomware Attacks
Recently, the Lynx group, another key player in the ransomware world, has gained attention for its cross-platform ransomware capable of targeting Windows, Linux, and ESXi systems. The group offers affiliates up to an 80% cut of the ransom proceeds, providing an attractive incentive for those willing to join the operation. Lynx also offers encryption modes that allow affiliates to balance the speed and depth of encryption depending on the target system.
Another trend is the growing use of botnets, such as the Phorpiex botnet, to distribute ransomware. Unlike previous attacks where human operators manually deployed ransomware, Phorpiex automates this process, increasing the speed and scale of attacks.
Other Tactics and Infection Vectors
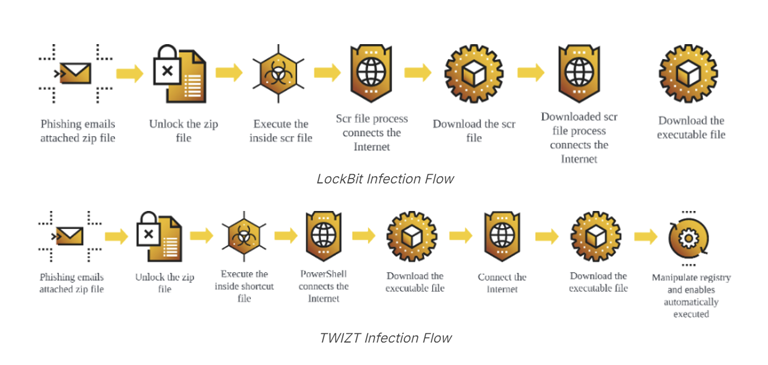
In addition to exploiting VPN vulnerabilities (such as CVE-2021-20038), ransomware actors have increasingly relied on techniques like Bring Your Own Vulnerable Driver (BYOVD) to disable endpoint protection mechanisms. This strategy ensures that attackers can maintain persistent access to critical network devices, including ESXi hosts, Windows machines, and NAS systems, allowing them to orchestrate their operations more effectively.
The Future of Ransomware
As more victims refuse to pay ransom demands, cybercriminals are adjusting their strategies. Data theft and extortion are becoming increasingly common, with ransomware groups offering larger rewards for stolen data. This shift in tactics is expected to continue, leading to a decrease in ransom payments but a rise in the overall impact of these attacks. Groups like RansomHub and Akira are leading this charge, making stolen data a key component of their operations.