This PolarEdge Trojan Turns Devices Into Remote Attack Tools
Overview of the Attack
A new botnet, named “PolarEdge,” has been identified as targeting devices from brands like Cisco, ASUS, QNAP, and Synology since late 2023. French cybersecurity company Sekoia recently uncovered the threat, which is exploiting a critical vulnerability (CVE-2023-20118) affecting certain Cisco routers. These routers have reached their end-of-life (EoL) and no longer receive security updates, leaving them vulnerable to exploitation.
You might be interested in: Understanding the Security Operations Center
The vulnerability, with a CVSS score of 6.5, affects several Cisco Small Business router models (RV016, RV042, RV042G, RV082, RV320, and RV325). Exploiting this flaw allows attackers to execute commands on these devices remotely. Cisco suggested disabling remote management and blocking ports 443 and 60443 as a temporary mitigation measure. However, due to the routers being EoL, many users may not have applied these recommendations.
Sekoia’s research shows that after exploiting the flaw, attackers were able to drop a new and previously unknown backdoor implant on the affected devices. This backdoor, built on TLS (Transport Layer Security), can listen for incoming connections and execute commands.
Botnet Functionality
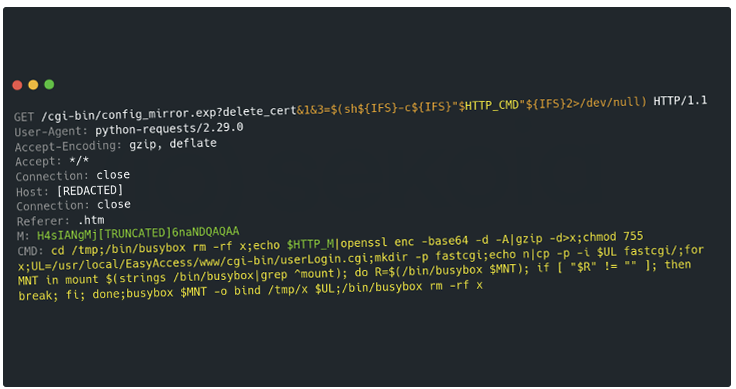
The attackers deploy the backdoor via a shell script called “q,” which is downloaded using FTP. Once executed, the script performs several tasks, including:
- Clearing log files
- Killing suspicious processes
- Downloading a malicious payload named “t.tar” from an IP address (119.8.186[.]227)
- Extracting and executing a binary named “cipher_log”
- Creating persistence by modifying a script to repeatedly run the “cipher_log” binary
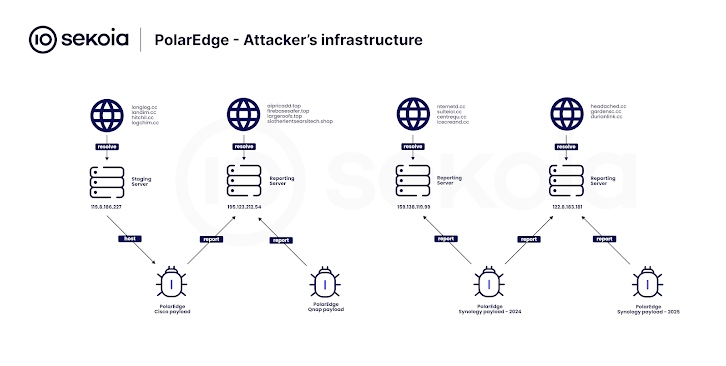
The backdoor, now called PolarEdge, sets up a continuous TLS connection with the command-and-control (C2) server, sending information about the compromised device. It also spawns a child process to handle client requests and execute commands.
The malware appears to use these compromised devices to create a large botnet that can be controlled remotely. This botnet was linked to 2,017 unique IP addresses worldwide, with infections detected in regions like the United States, Taiwan, Russia, India, Brazil, Australia, and Argentina.
Impact on Other Devices
Further investigations show that similar PolarEdge payloads have been used to target devices from ASUS, QNAP, and Synology as well. The malware is distributed through FTP, and the payloads are hosted on an IP address associated with Huawei Cloud. The exact purpose of the botnet is unclear, but it could be used for launching attacks from the infected edge devices.
The complexity of the malware, combined with the number of devices it targets, indicates that the threat actors behind PolarEdge are skilled and organized. The ongoing use of this botnet highlights the growing risk to internet-connected devices, particularly those that are not regularly updated or maintained.
Large-Scale Attacks and Password-Spraying Campaigns
In a related development, another large botnet—containing over 130,000 compromised devices—has been used for password-spraying attacks against Microsoft 365 (M365) accounts. These attacks target non-interactive sign-ins, which are typically used for service-to-service authentication. Since these sign-ins do not require multi-factor authentication (MFA), attackers can use stolen credentials to bypass security protections.
This attack, thought to be linked to a Chinese-backed group, targets M365 accounts by leveraging stolen credentials from infostealer logs. The attackers aim to gain unauthorized access to sensitive data while avoiding detection. These attacks are often recorded in non-interactive sign-in logs, which are frequently overlooked by security teams. As a result, the botnet is able to carry out large-scale password-spraying attempts without triggering modern security defenses.
Conclusion
Both PolarEdge and the password-spraying botnet show the growing sophistication of cyber threats and the importance of securing vulnerable devices. Organizations need to be vigilant about updating and patching their systems, as well as monitoring their networks for unusual activity. The scale of these attacks demonstrates that cybercriminals are increasingly targeting a wide range of devices, from home routers to corporate cloud accounts.