Fake Browser Extensions That Steal Login Info
Fake Browser Extensions
Cybersecurity experts have revealed a new way hackers can use Fake Browser Extensions to impersonate legitimate ones, tricking users into giving away their login details.
You might be interested in: This PolarEdge Trojan Turns Devices Into Remote Attack Tools
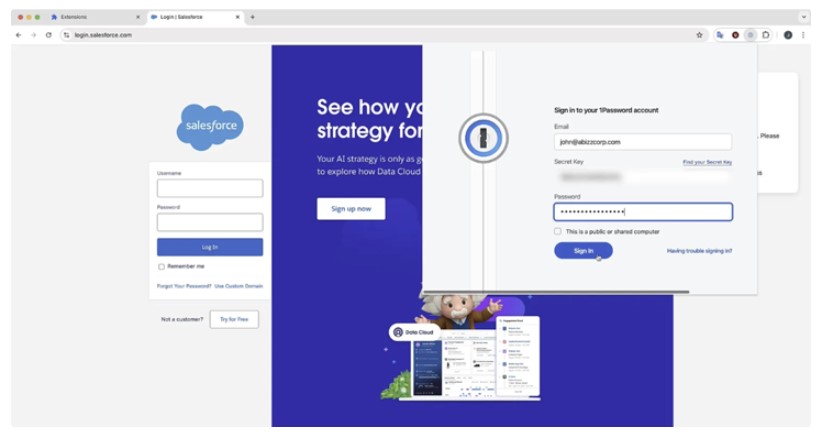
According to a recent report from SquareX, these deceptive extensions can perfectly mimic real add-ons by copying their icons, pop-up menus, and workflows. Even worse, they can temporarily disable the original extension, making it almost impossible for users to notice the difference.
How the Fake Browser Extensions Attack Works
This attack method targets all Chromium-based browsers, including Google Chrome, Microsoft Edge, Brave, and Opera. It relies on a simple fact: many users pin their extensions to the browser toolbar for easy access.
Hackers can upload a seemingly harmless extension to the Chrome Web Store, advertising it as a useful tool. Once installed, the extension functions normally to avoid suspicion. However, in the background, it scans for web resources linked to popular extensions using a technique called web resource hitting.
Once it finds a target extension, the malicious add-on changes its icon to match the real one and disables the legitimate extension using the chrome.management API. Since the original extension disappears from the toolbar, users unknowingly interact with the fake version instead.
Why This Attack is Dangerous
This technique is highly effective because most people rely on visual cues—like extension icons—to identify the tools they use. By replacing the real extension with an identical-looking fake, hackers can trick users into entering their credentials, which are then stolen and used for unauthorized access to sensitive accounts.
SquareX warns that this type of attack is a major security risk, as it could lead to stolen financial information, hijacked online accounts, and more.
A Growing Concern
This discovery follows another recent security warning from SquareX about Browser Syncjacking—a method where hackers take control of a victim’s device through an innocent-looking extension.
To stay safe, users should be cautious when installing browser extensions, regularly check their active add-ons, and only download them from trusted developers.