New Phishing Scam Poses as Booking.com to Steal info
Microsoft has uncovered an ongoing Phishing Attack that targets the hospitality industry by posing as the online travel platform Booking.com. The attack, tracked under the name Storm-1865, began in December 2024 and aims to commit financial fraud and data theft.
You might be interested in: Malicious Go Modules: Trojan Threats Targeting Linux and macOS Computers
The hackers send deceptive emails to employees of hotels and other businesses in North America, Oceania, Asia, and Europe. These emails pretend to be from Booking.com and attempt to lure recipients into a trap using a method known as ClickFix, a social engineering trick designed to install malicious software.
How the Attack Works
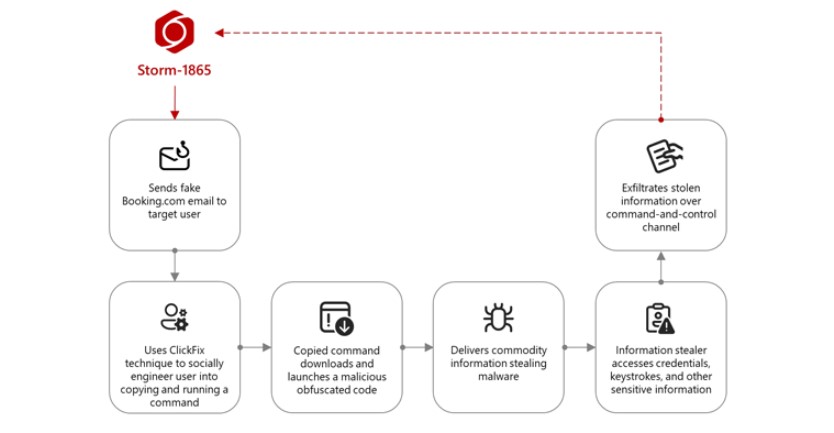
The phishing scam begins when an unsuspecting employee receives an email claiming that a guest left a negative review on Booking.com. The email urges the recipient to check the review and provide feedback.
The message contains either a direct link or a PDF attachment with a link that appears to take users to the legitimate Booking.com website. However, clicking the link instead redirects them to a fake CAPTCHA page designed to look trustworthy.
According to Microsoft, this fake CAPTCHA is a cover for the ClickFix technique, which tricks users into following harmful instructions. The page instructs them to copy a provided command and paste it into the Windows Run tool, which unknowingly executes malware on their system.
The Dangerous Malware Behind ClickFix
Once the malicious command is executed, a Windows tool called mshta.exe downloads and runs the next stage of the attack. The payload may include a variety of malware, such as:
- XWorm
- Lumma Stealer
- VenomRAT
- AsyncRAT
- Danabot
- NetSupport RAT
These malware programs can steal sensitive information, grant remote access to hackers, or perform unauthorized financial transactions.
Storm-1865’s Changing Tactics
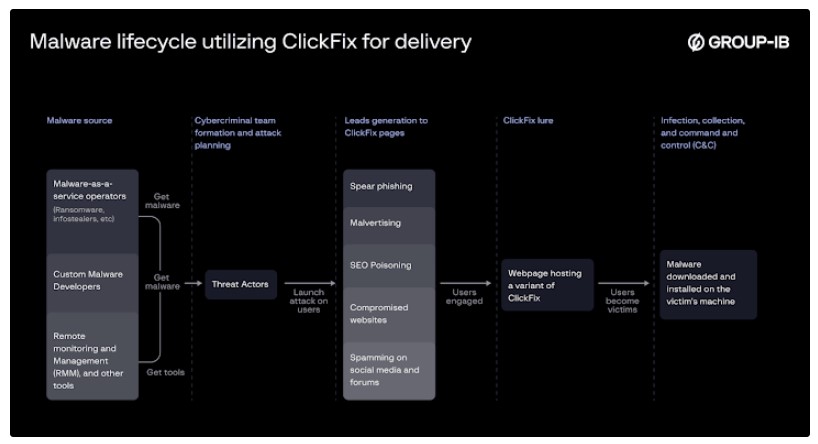
Microsoft has observed Storm-1865 using phishing emails to target online shoppers in the past. These earlier campaigns tricked victims into entering payment details on fraudulent web pages. However, by incorporating ClickFix, the group has found a way to bypass traditional security filters and increase their chances of infecting systems.
Threat groups from Russia and Iran, such as APT28 and MuddyWater, have also adopted ClickFix for their cyberattacks. The method works so well because it exploits human psychology, making people believe they are fixing a problem when in reality, they are launching malware.
Other Ways ClickFix is Being Used
Besides fake Booking.com emails, ClickFix has been seen in multiple cyberattacks, including:
- Use of fake CAPTCHA verifications to initiate a multi-stage PowerShell execution process, ultimately delivering infostealers such as Lumma and Vidar
- Use of fake Google reCAPTCHA challenges by a threat actor dubbed Blind Eagle to deploy malware
- Use of fake booking confirmation links to redirect users to CAPTCHA verification pages that lead to Lumma Stealer
- Use of fake Windows-themed sites to redirect users to CAPTCHA verification pages that lead to Lumma Stealer
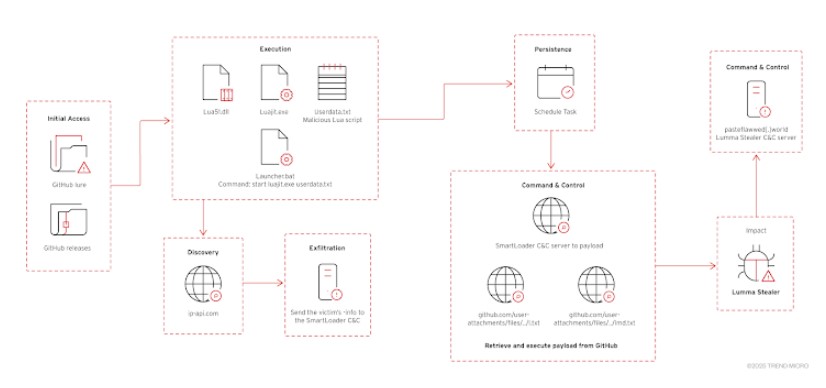
Another campaign uncovered by cybersecurity firm Trend Micro reveals that attackers are hiding malware in fake GitHub repositories. These repositories disguise harmful software as game cheats, cracked applications, and cryptocurrency tools. When victims download these files, they unknowingly install a malware loader called SmartLoader, which then drops Lumma Stealer onto their system.
Cybercriminals Exploit Trusted Platforms
The rise of ClickFix-based attacks highlights how hackers manipulate trusted online services like Booking.com, GitHub, and e-commerce sites to spread malware. Attackers rely on users’ trust in these platforms to lower their defenses, making social engineering tactics even more effective.
Meanwhile, another phishing campaign detailed by security firm Trustwave involves fake invoice emails distributing an updated version of StrelaStealer malware. Researchers suspect that the attacker, known as Hive0145, has developed a special tool called “Stellar Loader” to hide the malware and make it harder to detect.
Protecting Against ClickFix Attacks
As phishing techniques continue to evolve, it’s crucial for businesses and individuals to stay alert. Here are some steps to protect against ClickFix and similar cyber threats:
- Be cautious of unexpected emails, especially those requesting urgent action.
- Avoid clicking on suspicious links or attachments, even if they appear to come from trusted sources.
- Never copy and paste commands from unknown sources into your computer.
- Use advanced security tools to detect and block phishing attempts.
- Verify information directly by contacting the supposed sender through official channels.
With cybercriminals refining their methods, staying informed and vigilant is the best defense against threats like Storm-1865 and ClickFix-based malware.