Interlock Hackers Turn to FileFix and a PHP-Based RAT in Their Latest Campaign
Booby-Trapped Websites Funnel Unsuspecting Visitors Into FileFix’s Trap
Researchers from The DFIR Report and Proofpoint say the crew behind the Interlock ransomware operation has shifted tactics once again, swapping its Node.js remote-access trojan for a new PHP rewrite and delivering it through a social-engineering trick known as FileFix. The change was first spotted in attacks that began showing up in May 2025 and reached full stride this month, July 2025, when the technical write-up was released.
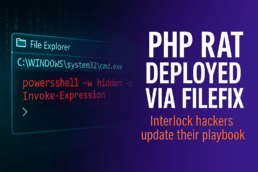
In the current wave, the attackers compromise legitimate websites and drop a single, invisible line of JavaScript into the page’s source code. That tiny implant acts as a traffic broker: it checks each visitor’s IP address, geography and other clues before silently kicking suitable targets over to a fake CAPTCHA page. What looks like a routine “prove-you’re-human” test is anything but routine. After the victim completes the bogus challenge, the site instructs them to copy a string that resembles a file path and paste it into the Windows File Explorer address bar. The string is actually a PowerShell command; pasting it launches a script that quietly reaches out to attacker-controlled infrastructure and pulls down the malware.
FileFix: A Slick Spin-Off of ClickFix
FileFix is an evolution of the better-known ClickFix technique that security researcher mrd0x debuted earlier this year. ClickFix coaxed users into pasting malicious text into the Windows “Run” dialog; FileFix upgrades the ruse by exploiting the File Explorer address bar, a place most office workers trust and use every day. Because the command hides inside what looks like a normal folder path, no antivirus pop-ups appear, and Windows’ built-in protections stay silent. Once the PowerShell snippet executes, it places the PHP payload—now being called the Interlock RAT (PHP edition)—into the user’s roaming profile and fires it up.
Inside the New PHP RAT
Although it is written in PHP rather than Node.js, the new trojan keeps the same job description as its predecessor. Right after launch it inventories the host, collecting system information, running processes, installed services, mounted drives and basic network details. All of that data is bundled into tidy JSON files and shipped back to the attackers’ command server. The code also checks what level of access it has—standard user, administrator or full SYSTEM—so the operator knows immediately how much power the foothold provides.
The malware then opens a control channel that can accept several instructions. It can fetch and run extra executables or libraries, turn itself into a startup item by altering registry keys, execute arbitrary shell commands, or simply shut itself down if told to cover its tracks. Persistence is typically achieved by adding a “Run” key that points back to the PHP binary and its configuration file, guaranteeing that the RAT comes back after every reboot. Operators have also been observed pivoting within a victim’s network via Remote Desktop Protocol once the implant is stable.
Cloudflare Tunnels Mask the Command Servers
To stay hidden, the Interlock group routes much of its command-and-control traffic through Cloudflare Tunnel sub-domains. By abusing Cloudflare’s legitimate tunneling service, the attackers camouflage the real internet addresses of their servers. Even if defenders block the tunnel or Cloudflare takes it down, the RAT carries a short list of hard-coded IP addresses as a fallback, ensuring it can phone home.
Opportunistic Targeting and Ongoing Evolution
So far, the campaign does not appear laser-focused on any one sector. Security analysts call it “broad and opportunistic,” with victims turning up in education, local government, healthcare and beyond. Earlier in the year, the same group was caught dropping a Node.js build of its RAT—dubbed NodeSnake—on British universities and councils. Swapping in a PHP version, and a fresh delivery tactic, highlights how quickly Interlock re-tools when defenders start to catch on
Investigators warn that the FileFix approach is likely to spread: it is simple, requires no vulnerabilities, and relies purely on social engineering. Anyone who can persuade a user to paste a string into an Explorer window can sidestep many layers of corporate security. With Interlock already demonstrating how effective the trick can be, it would not be surprising to see other threat actors adopt the method in the months ahead.
For organisations, the lesson is straightforward but urgent: user awareness training must now cover seemingly harmless actions such as pasting paths into Explorer; endpoint monitoring should flag unusual instances of PowerShell spawning PHP; and outbound traffic to Cloudflare Tunnel domains deserves extra scrutiny. Interlock’s latest pivot underscores a hard truth of modern cyber defence—attackers will keep rewriting their playbooks, and defenders have to keep re-reading them just as fast.