Massive ‘Ghost Network’ Caught Using 3,000 YouTube Videos to Spread Malware
A massive, highly organized cybercrime operation is turning YouTube into a dangerous minefield for malware. Security researchers have uncovered what they call the “YouTube Ghost Network,” a sprawling web of accounts dedicated to tricking users into downloading vicious, data-stealing software. This network has been quietly operating since 2021, but its activity has exploded recently, with the volume of malicious videos tripling since the beginning of this year alone.
The operation, detailed by security firm Check Point, has already published more than 3,000 videos designed to act as bait. While Google has been working to remove the dangerous content, the network’s sophisticated structure allows it to adapt and survive takedowns, posing an ongoing threat to millions of users.
How Your Hunt for Cheats Could Cost You Everything
The attackers prey on users searching for very specific, popular topics: pirated software and video game cheats. The network floods YouTube with videos that appear to be helpful tutorials, offering things like free downloads for expensive programs or cheats for popular games like Roblox.
These aren’t just poorly made videos; many are polished and convincing. Some have managed to fool hundreds of thousands of people, racking up view counts ranging from 147,000 to a staggering 293,000. Unsuspecting users, believing they are about to get a free tool, are instead led directly into a trap designed to infect their computers with powerful malware.
The primary weapons used in this campaign are “stealers.” This type of malware is designed to steal everything: saved passwords from your browser, cryptocurrency wallets, credit card details, and other sensitive personal files.
A Sophisticated Scam Using Familiar Tools
What makes this network so effective is its ability to fake trustworthiness. The cybercriminals aren’t just creating brand-new accounts with zero followers. Instead, they actively hijack legitimate, established YouTube channels, some with thousands or even hundreds of thousands of subscribers. Once they have control, they wipe the original content and begin uploading their malicious videos, instantly inheriting the channel’s established audience and credibility.
This tactic exploits the natural trust signals YouTube provides. As Eli Smadja, a security research manager at Check Point, explained, the operation uses views, likes, and comments to make the dangerous content seem perfectly safe. A user searching for a tutorial might see a video with 100,000 views and a comment section full of positive feedback, leading them to believe the link is legitimate.
“What looks like a helpful tutorial can actually be a polished cyber trap,” Smadja warned. He described the network’s scale and advanced design as a “blueprint” for how criminals are now “weaponizing” the platform’s own engagement tools to spread their viruses.
Inside the “Ghost Network”: A Factory for Fraud
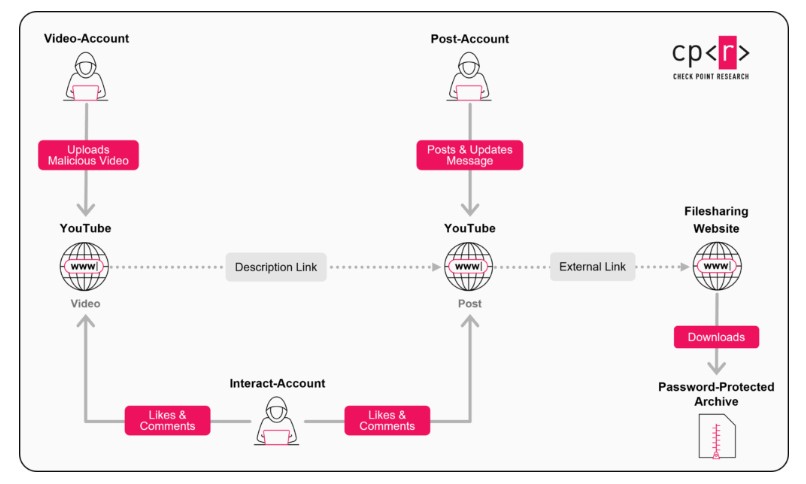
This isn’t the work of a single hacker. The “Ghost Network” operates like a sophisticated business with a clear, role-based structure. This division of labor not only makes the operation more efficient but also makes it incredibly resilient.
Researchers identified three distinct types of accounts working together. First are the “Video-accounts,” which are the workhorses of the operation. These accounts, often the hijacked ones, are responsible for uploading the bait videos. They place the malicious download links in the video description, as a pinned comment, or sometimes even show them directly in the video itself.
Second are the “Post-accounts.” These accounts use YouTube’s lesser-known “community posts” feature—which functions like a status update on Facebook or X—to share malicious links and messages, further promoting the malware.
Finally, and perhaps most deceptively, are the “Interact-accounts.” This is a swarm of accounts whose only job is to give the videos a fake veneer of trust. They flood the malicious videos with likes and post streams of encouraging comments, saying things like “This worked great!” or “Thanks, I got the software!” This social proof is often enough to convince a hesitant user to click the download link.
This structure means that even if Google identifies and bans some of the accounts, the network as a whole remains intact. The operators can simply swap in new, stolen accounts to replace the ones that were removed, allowing the campaign to continue without missing a beat.
The Path from a Click to a Compromise
The infection process is a multi-step funnel. The links in the videos or posts, often masked using URL shorteners, don’t usually lead directly to the malware. Instead, they send victims to a wide range of intermediary sites, including popular file-hosting services like MediaFire, Dropbox, and Google Drive. In other cases, they use free website builders like Google Sites, Blogger, or Telegraph to create convincing phishing pages.
These landing pages instruct the user to download the promised software. The file they receive is, of course, the malware. The campaign has been caught distributing some of the most dangerous information stealers currently active, including Lumma Stealer, Rhadamanthys Stealer, StealC, and the infamous RedLine Stealer.
In one documented case, a channel named @Afonesio1, with 129,000 subscribers, was compromised. The hackers uploaded a video for a cracked version of Adobe Photoshop. Users who downloaded the file actually received an installer that deployed Hijack Loader, which in turn infected the computer with the Rhadamanthys stealer. Another channel, @Sound_Writer, was used for over a year to push fake cryptocurrency software that also delivered the same malware.
Check Point researchers emphasized that this campaign highlights a major shift in how cybercriminals operate. They are moving away from traditional methods and are now leveraging the built-in trust of legitimate platforms like YouTube to run large-scale, persistent, and highly effective malware campaigns.
