Cut Your Cybersecurity Risk by 90% with Penetration Testing Services
If your company is growing and you’re not running regular penetration testing services, you’re betting your future on luck.
The organizations that don’t risk their growth to hackers all have one thing in common:
They use a repeatable system for internal and external penetration testing — not a one-off scan, not a fake “compliance only” check, but a clear, structured workflow they run every year or every quarter as part of their cybersecurity risk management strategy.
Most “pen tests” on the market are either:
-
an automated scan that results in a long PDF, or
-
a once-a-year checkbox for auditors looking for basic vulnerability assessment.
In this guide, I’m going to break down a 5-step penetration testing workflow that serious, security-minded companies use to:
-
see how an attacker would gain external network access,
-
see what happens if someone is already inside your internal network, and
-
get a prioritized list of fixes that actually reduce your cybersecurity exposure.
If you’re new here, my name is Dan Duran. I’m the CTO of Rhyno Cybersecurity, a top penetration testing company that helps organizations who don’t want to gamble their growth on a single cyberattack.
Day to day, that means:
-
running comprehensive internal and external penetration tests for clients,
-
simulating real attack paths,
-
and helping companies turn “we hope we’re secure” into “we know our exposure and we’re fixing it.”
Let me show you the system.

Step 0 – The Overall Penetration Testing Workflow
Before we split internal vs. external, we need the full picture.
A serious Vulnerability and Penetration Testing (VAPT) program follows this 5-step workflow:
-
Discovery & Scoping
-
External Penetration Testing
-
Internal Penetration Testing
-
Reporting & Communication
-
Remediation & Retesting
Most companies:
-
jump straight to step 2,
-
buy a test,
-
then realize half their critical systems weren’t even in the scope of the penetration test.
We’ll go through each step and I’ll show you:
-
what most teams do wrong, and
-
what secured, growth-focused companies do instead.
Step 1 – Discovery & Scoping
Most organizations start testing with a vague idea like “let’s test security this year.”
Non-Systematized Version:
-
Vendor sends a generic proposal.
-
You test “the website and VPN.”
-
Internal apps, cloud services, and critical data paths are ignored.
-
You get a report, but it doesn’t reflect your real cybersecurity risk.
Systematized Version (The Rhyno Approach): You always start with a short scoping workshop:
-
Asset Inventory: Internet-facing systems (domains, subdomains, IPs, VPNs), internal networks, key applications, and cloud security accounts (AWS, Azure, GCP, SaaS).
-
Critical Data: Customer info, payments, health data, IP—the real high-value targets.
-
Clear Objectives: Objectives tied to business risk, such as: “Can an outsider reach sensitive customer data?” or “Which systems present the biggest risk to revenue and operations?”
-
Rules of Engagement: What’s in scope, what’s out, and escalation paths.
Output of Step 1 = a 2–3 page scope document. This alone puts you ahead of most companies looking for basic vulnerability assessment services.
Step 2 – External Penetration Testing (Internet-Facing View)
Now we move to the external network penetration test: simulating how an attacker on the internet would target your organization.
What Most Companies Do:
-
Run a basic vulnerability scan from outside.
-
Get 100+ findings labeled High/Medium/Low.
-
Maybe validate a couple, then stop.
Systematized External Testing:
-
Attack Surface Mapping: Enumerate all public web apps, APIs, VPN gateways, and exposed cloud-exposed services.
-
Scan + Manual Verification: Use scanners but manually validate and exploit critical vulnerabilities. We focus on proving real access, not just listing scanner findings.
-
Focus on Entry Paths: Weak authentication, known exploits on exposed services, or misconfigurations on VPN/SSO.
Deliver concrete external scenarios: “From this exposed service, we obtained valid credentials and initial access to the network.”

Step 3 – Internal Penetration Testing (Assume Breach View)
Now we treat one assumption as true: At some point, an attacker will get in.
That’s what the internal penetration test is for—to measure the damage after a breach.
What Most Companies Do:
-
Ignore internal testing completely, or
-
Only rely on compliance checks (AV installed, GPO in place, etc.).
That’s not enough to manage your internal network security risk.
Systematized Internal Testing:
-
Start from a Realistic Foothold: A low-privilege domain account or a user workstation.
-
Map the Internal Environment: Active Directory structure, privileges, internal subnets, and file shares.
-
Test Lateral Movement & Privilege Escalation: Weak passwords, misconfigured services, unpatched internal systems—the paths that lead to Domain Admin.
-
Build a Realistic Attack Chain: “From a compromised user account → to a shared drive → to a service account → to Domain Admin.” This is how a real attacker moves.
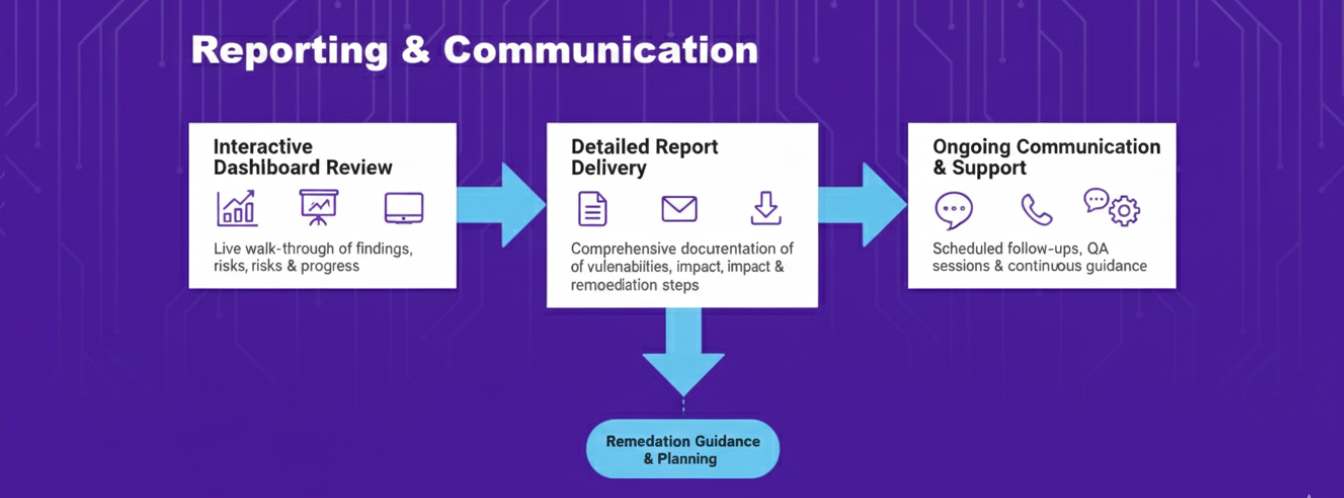
Step 4 – Reporting & Communication
This is the part that tells you if a breach would be a minor incident or a business-level event. A penetration testing report is useless if it can’t drive decisions.
Systematized Reporting: Your report has two audiences and serves both:
-
Leadership / Management:
-
1–2 page Executive Summary.
-
Clear, plain-language statements: “External attackers can / cannot gain initial access.”
-
Top 5–10 risks prioritized by business impact (revenue, operations, compliance / legal risk).
-
-
Technical Teams:
-
Prioritized list of findings grouped by business impact and exploitability.
-
Clear remediation tags: “fix in 24h / 7 days / 30 days.”
-
For each finding: what we did, what we proved, and how to fix it and verify the patch.
-
Result: Leadership understands why it matters. Engineers know exactly what to change.
Step 5 – Remediation & Retesting
This is where many companies fall apart. The risk remains because they stop here.
Systematized Remediation & Retesting:
-
Convert Findings into Work: Each critical/high finding becomes a tracked ticket with an assigned owner and due date.
-
Define Done: Done = fixed, documented, and verified by retesting.
-
Schedule Retests: Retest critical items as they’re marked complete. Don’t wait for “next year’s pen test.”
-
Set a Testing Cadence: External tests at least annually; internal tests after major changes and on a predictable schedule.
Use it as a continuous improvement loop: Test → Fix → Retest → Update baseline. Over time, your attack surface shrinks and your internal exposure decreases.
Summary: Your Internal & External Penetration Testing System
-
Step 0 – Workflow: Discovery & Scoping → External Test → Internal Test → Reporting → Remediation & Retest.
-
Step 1 – Discovery & Scoping: Build a clear scope tied to real business impact, focusing on Vulnerability Assessment before the exploit phase.
-
Step 2 – External Pen Test: Identify real entry points from the internet, going beyond just a list of scanner findings.
-
Step 3 – Internal Pen Test: Assume breach, measure lateral movement, and prove access to sensitive data on your internal network.
-
Step 4 – Reporting: Executive summary + technical details = decisions + actions.
-
Step 5 – Remediation & Retesting: Turn findings into tracked work, verify fixes, and repeat on a defined cadence for long-term cybersecurity risk management.
This is how companies that don’t bet their future on a cyberattack treat penetration testing: not as a checkbox, but as a structured, repeatable process.
If you want a deeper breakdown of a real (anonymized) attack path from an external foothold to internal compromise, let me know in the comments with: “Show me a real attack chain.”
And if you’re responsible for security in a growing company and you want a proven penetration testing firm to handle this properly for your organization:
-
Subscribe for the next videos in this series, and
-
Reach out to us at Rhyno Cybersecurity.
Use the “Contact Us” link in the description to book a conversation with our team, and we’ll help you plan and execute a tailored internal & external penetration test for your environment.
Rhyno Cybersecurity, Protect with Passion.


