7 Data Breach Disasters – Lessons for Cybersecurity Awareness Month
Celebrating Cybersecurity Awareness Month!
Hi everyone, I’m Dan Duran, and since it’s Cybersecurity Awareness Month, I want to shine a light on some of the biggest hacks in history. These stories not only reveal how vulnerable we can be but also teach essential security concepts every developer and business should know to stay protected. Let’s dive in!
You might be interested in: Instagram Introduces New Safety Features for Teens
What Are Zero-Day Vulnerabilities?
Zero-day vulnerabilities are security flaws that no one has discovered yet, or haven’t been fixed in time. Hackers love these because they strike before anyone knows about the issue, giving developers zero time to react. A well-known example is the Equifax breach. Although it wasn’t technically a zero-day attack, it happened because Equifax didn’t apply a security patch in time. Hackers exploited a flaw in Apache Struts and stole the data of over 150 million people. This disaster cost Equifax over a billion dollars, all of which could’ve been avoided by simply updating their software.
Known Vulnerabilities Are Just as Dangerous
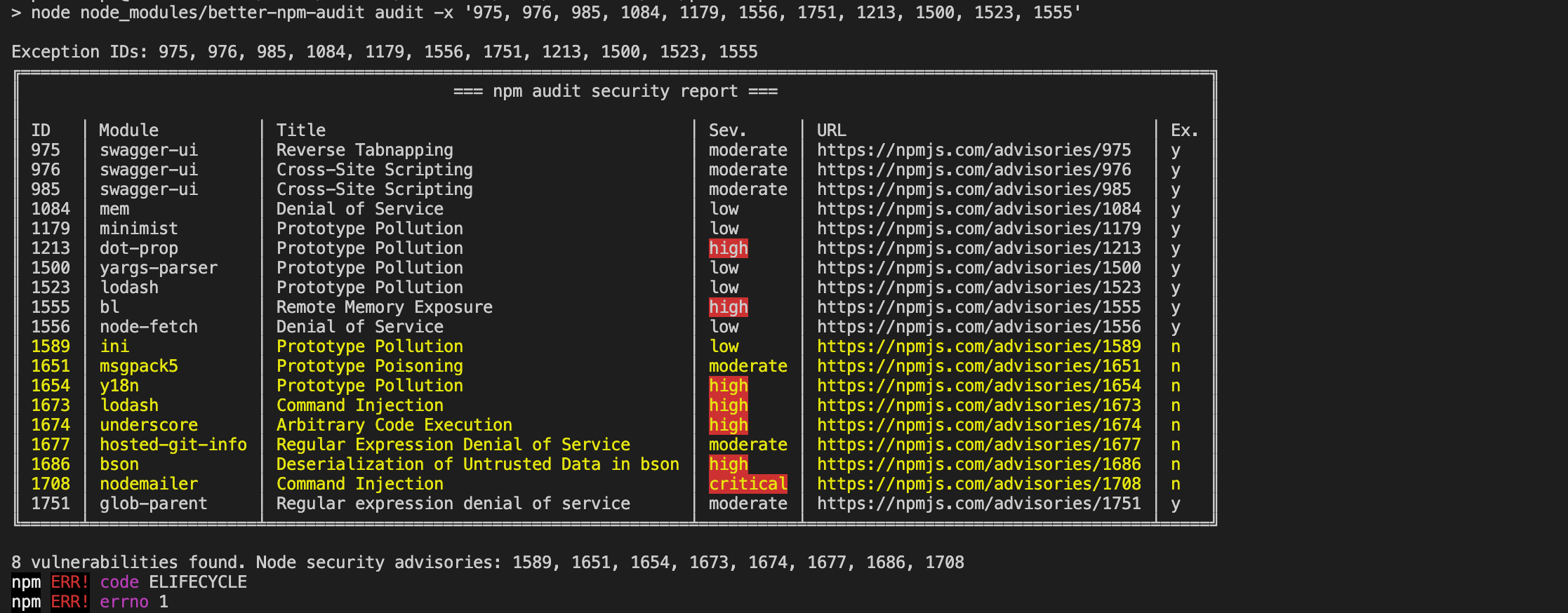
Many developers unknowingly ship code with known vulnerabilities. For example, JavaScript developers using npm audit often find several high-risk issues in their dependencies. It’s not just a JavaScript problem—this happens with any code that relies on open-source software. Regular updates are the easiest and best way to avoid these threats.
SQL Injection: A Real Threat
Another common attack is SQL injection, where hackers manipulate databases by sending malicious queries. A famous case happened in 2008 when hackers targeted Heartland Payment Systems, stealing over 100 million credit card records. This breach could have been avoided by simply validating the input data and using better tools like ORM.
The CIA Triad: Confidentiality, Integrity, and Availability
One key concept in cybersecurity is the CIA Triad, which stands for Confidentiality, Integrity, and Availability. Confidentiality means keeping data private, Integrity ensures that data isn’t changed without permission, and Availability means the data is accessible when needed. One of the biggest threats to Availability is a DDoS attack (Distributed Denial of Service). In 2018, GitHub survived the largest DDoS attack ever, which temporarily knocked the site offline. Even though they recovered quickly, smaller businesses might not have been as lucky. To protect yourself, it’s important to use cloud services that can handle large amounts of traffic, like Google Cloud Armor.
Avoiding API Key Leaks
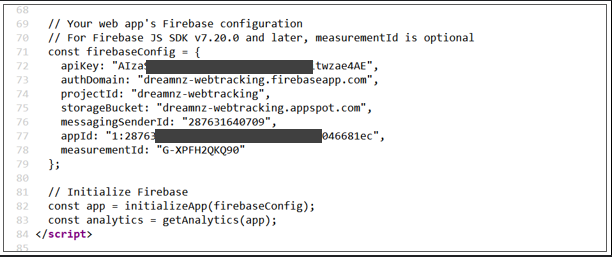
Another common issue developers face is the accidental exposure of API keys. API keys are like passwords that give access to important services like AWS. Leaking them can lead to serious consequences. A few years ago, I accidentally leaked my AWS API key in a public GitHub repository, which resulted in $5,000 worth of unauthorized charges. Thankfully, AWS refunded the costs, but it was a huge wake-up call. These days, tools can automatically detect exposed keys in public repositories, but the safest practice is to store your keys in environment variables, not directly in your code.
Principle of Least Privilege
When managing access, always follow the principle of least privilege, which means giving users, API keys, or services the minimum access they need to do their job. For example, cloud providers like AWS allow you to create specific roles and policies for each API key, limiting access to sensitive information. This way, if a breach happens, the damage is contained. A breach at Morrison’s supermarkets is a good example. A rogue employee stole data on 100,000 staff members using a USB stick. Following the least privilege rule could have reduced the damage.
Cross-Site Scripting (XSS)
Another classic hack is Cross-Site Scripting (XSS), which allows malicious JavaScript to run in another user’s browser. Back in 2005, a hacker named Sammy used XSS to change over a million MySpace profiles just by inserting a script. While the attack didn’t cause serious damage, it highlighted how vulnerable websites can be. Developers can prevent XSS by validating input data on the server side and avoiding rendering raw HTML.
The Bottom Line of Cybersecurity Awareness Month
At the end of the day, no system is 100% safe. Zero-day vulnerabilities are lurking in billions of lines of code, just waiting to be exploited. The key to building secure software is staying informed, keeping your systems updated, and following good security practices. This way, you can reduce the risk and act quickly when the next big breach hits the headlines.