700K DrayTek Routers Vulnerable to Hacks
Recent investigations have uncovered over a dozen vulnerabilities in household and enterprise routers made by DrayTek. These flaws could be exploited by attackers to take control of vulnerable routers and gain access to enterprise networks.
You might be interested in: MediaTek Wi-Fi Chips Hacked – CVE-2024-20017 Threat Alert
In a report shared with The Hacker News, Forescout Vedere Labs explained that these security gaps could allow hackers to inject harmful code into the routers. This would give them control over the device, enabling them to use it as a backdoor into larger networks.
Breakdown of Vulnerabilities
A total of 14 security flaws were identified:
- 2 critical vulnerabilities
- 9 high-risk vulnerabilities
- 3 less severe vulnerabilities
The most severe vulnerability, with a CVSS score of 10.0, is a buffer overflow issue in the “GetCGI()” function. This problem could lead to denial-of-service (DoS) attacks or allow for remote code execution (RCE) when certain parameters are processed by the Web user interface.
Another major issue is an operating system (OS) command injection vulnerability in the “recvCmd” binary, which allows attackers to execute commands between the host and guest operating systems.
List of Remaining Flaws
- Shared admin credentials across the system, compromising the entire network (CVSS score: 7.5).
- Cross-site scripting (XSS) flaw in the web interface (CVSS score: 7.5).
- Stored XSS vulnerability in the web interface’s personalized greeting message (CVSS score: 4.9).
- Stored XSS vulnerability when setting a custom router name (CVSS score: 4.9).
- Reflected XSS vulnerability in the login page (CVSS score: 4.9).
- Buffer overflow vulnerabilities on certain CGI pages, leading to DoS or RCE (CVSS score: 7.2).
- Stack buffer overflow vulnerability on the “/cgi-bin/ipfedr.cgi” page, potentially causing DoS or RCE (CVSS score: 7.2).
- Multiple vulnerabilities in the Web UI causing DoS or RCE (CVSS score: 7.2).
- Heap-based buffer overflow vulnerability in the ft_payloads_dns() function, causing DoS (CVSS score: 7.2).
- Out-of-bounds write vulnerability in the Web UI, causing DoS or RCE (CVSS score: 7.2).
- Information disclosure flaw in the web server backend, potentially leading to adversary-in-the-middle attacks (CVSS score: 7.6).
The Global Impact
Forescout estimates that over 704,000 DrayTek routers have their Web user interface (UI) exposed to the internet. The largest number of exposed routers is found in the United States, followed by Vietnam, the Netherlands, Taiwan, and Australia.
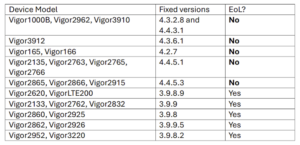
DrayTek’s Response and Patches
DrayTek has released patches for all identified vulnerabilities, including the highest-rated ones, covering even 11 end-of-life (EoL) models. These updates came after a responsible disclosure process.
Protecting Your Device
Forescout advises users to apply patches immediately. For those who do not need remote access, it’s recommended to disable that feature. Additionally, using an access control list (ACL) and two-factor authentication (2FA) can further secure devices.
Recommendations for Critical Infrastructure
To help organizations manage these risks, cybersecurity authorities from the United States, United Kingdom, Australia, Canada, Germany, Japan, the Netherlands, New Zealand, and South Korea have issued joint guidelines for securing operational technology (OT).
The key principles for OT security include:
- Prioritize safety.
- Understand the business environment.
- Protect OT data as valuable assets.
- Keep OT separate from other networks.
- Safeguard the supply chain.
- People are key to OT security.
These principles emphasize the importance of quickly identifying security decisions that affect OT environments. By doing so, organizations can make informed choices that enhance safety, security, and business continuity.
