Bootkitty: Linux’s First UEFI Bootkit
Cybersecurity experts have identified the first Unified Extensible Firmware Interface (UEFI) bootkit designed specifically for Linux-based computers. The bootkit, named Bootkitty by its creators, marks a new chapter in the evolution of cybersecurity threats.
You might be interested in: Microsoft and Meta Battle Cybercrime Networks
What Is Bootkitty?
Developed by a group known as BlackCat, Bootkitty is currently classified as a proof-of-concept (PoC) rather than a tool actively used in real-world attacks. This malware, also tracked under the name IranuKit, surfaced on VirusTotal on November 5, 2024.
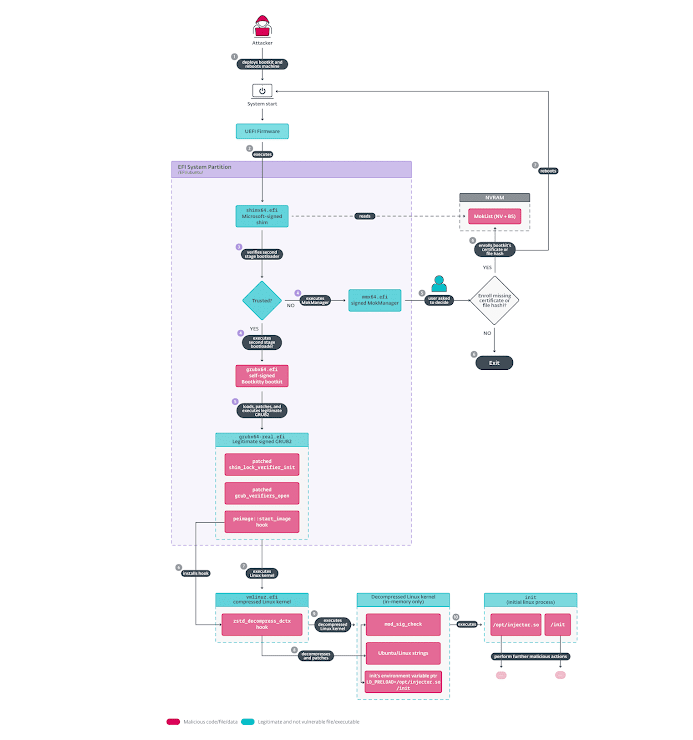
The purpose of Bootkitty is to tamper with Linux system integrity by disabling the kernel’s signature checks and preloading two unknown executable files (ELF binaries) through the Linux init process—the very first process that runs during a Linux startup.
A Significant Shift in Cyber Threats
For years, UEFI bootkits were mainly associated with attacks on Windows systems. Bootkitty’s arrival shows that cybercriminals are shifting their focus to Linux platforms, opening up new avenues for potential security threats.
Unlike traditional malware, Bootkitty requires systems to have a specific setup for it to function. It uses a self-issued certificate for its execution, meaning it cannot operate on systems with UEFI Secure Boot enabled unless attackers have already installed a malicious certificate.
How Bootkitty Works
Targeting Linux Boot Processes
Bootkitty works by modifying the Linux kernel’s response to integrity checks, even before the system reaches the GRUB bootloader stage.
- If Secure Boot is enabled, the bootkit hooks into two UEFI authentication functions to bypass these security measures.
- It alters three key functions within GRUB to sidestep additional integrity checks.
These changes allow Bootkitty to patch the Linux kernel in memory and proceed without triggering security alerts.
Rootkit Features
Further investigation into Bootkitty by Slovakian researchers uncovered a kernel module tied to the malware. This module, labeled as “BlackCat,” deploys an ELF binary known as BCDropper, which loads another unknown kernel module once the system is fully running.
This kernel module introduces advanced rootkit capabilities, including:
- Hiding files and processes.
- Creating secret communication channels for attackers.
At this stage, no direct connection has been established between Bootkitty and the ALPHV/BlackCat ransomware group.
Why It Matters
While Bootkitty is still a PoC, it serves as a wake-up call for cybersecurity professionals. Linux systems are no longer immune to the kinds of UEFI attacks previously thought to be Windows-specific.
This discovery emphasizes the need for stronger defenses against future UEFI-based threats. As the landscape of cyberattacks evolves, staying ahead of these developments is critical for system administrators and security experts.
Final Thoughts
Bootkitty represents a turning point in how we perceive UEFI vulnerabilities. It’s a reminder that no platform is entirely safe from sophisticated threats. While currently limited in scope, this bootkit could pave the way for more advanced attacks targeting Linux systems in the future.
Stay vigilant, ensure Secure Boot is properly configured, and regularly update your systems to minimize risks.