Chinese Hackers APT41 Attack Gambling Companies
Chinese state-backed hacking group APT41, also known as Brass Typhoon, Earth Baku, Wicked Panda, or Winnti, carried out a sophisticated cyber attack targeting the gambling and gaming sector. According to Ido Naor, co-founder and CEO of Security Joes, the hackers managed to infiltrate a company’s network for over six months, stealing sensitive data such as network configurations, user passwords, and secrets from the LSASS process.
You migh be interested in: Hackers Exploit EDRSilencer to Evade Security
How the Attack Unfolded
Over the course of nine months, APT41 conducted a multi-stage attack that coincided with a separate operation identified by Sophos called Operation Crimson Palace. Throughout the attack, the group used various strategies to avoid detection. By monitoring the actions of the company’s security team, they were able to adapt their tools and techniques, ensuring they could maintain their access.
The hackers used a specialized toolkit to bypass security systems, extract critical data, and create hidden pathways for continuous remote access. Security Joes described APT41 as a highly skilled and methodical group known for carrying out espionage, supply chain poisoning, and financially-motivated attacks, including ransomware and cryptocurrency mining.
Initial Access and Techniques Used
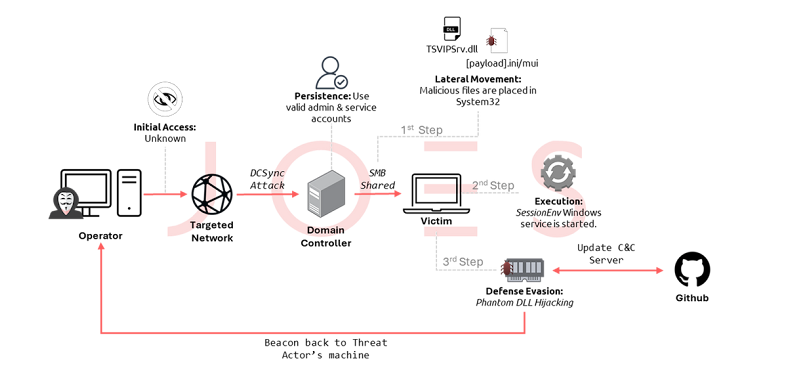
The attackers likely gained initial access through spear-phishing emails, as there were no vulnerabilities found in external-facing web applications or signs of a supply chain compromise. Once inside the network, they carried out a DCSync attack to extract password hashes from service and admin accounts. This allowed them to deepen their access, particularly targeting administrative and developer accounts.
Some of the tactics observed included Phantom DLL Hijacking, misuse of the legitimate tool wmic.exe, and exploitation of service accounts with admin privileges. At one point, they used a malicious DLL file named “TSVIPSrv.dll,” delivered over SMB, which communicated with a command-and-control (C2) server.
Persistent Monitoring and Adaptation
APT41’s strategy involved silently monitoring the network for weeks at a time, then reappearing with new tactics. After the initial attack was discovered, they returned using extensively obfuscated JavaScript code embedded in a modified XSL file (“texttable.xsl”), once again utilizing the wmic.exe tool to launch their payload.
The hackers set up their JavaScript to download additional malware, which would gather information about the infected machine and send it to a secondary C2 server. Security Joes reported that the server’s address was linked to “time.qnapntp[.]com,” with specific criteria to ensure that only target devices would be affected.
Targeting Specific Devices
The attackers showed particular interest in devices within VPN subnets. They configured their malware to filter out machines that didn’t meet specific IP patterns, focusing only on those with addresses containing “10.20.22.” Security Joes concluded that this filtering method was a deliberate attempt to limit the scope of the attack to specific devices that were of value to APT41.
Conclusion
This cyber attack by APT41 demonstrates the ongoing threat posed by state-backed actors targeting specific industries for both espionage and financial gain. By continuously adapting their techniques and carefully planning their operations, they managed to maintain a presence on the compromised network for several months, making detection and response even more challenging for security teams.
