Cicada3301 Ransomware: Inside the Affiliate Scheme
Cybersecurity experts have recently accessed the affiliate panel of Cicada3301, a new ransomware-as-a-service (RaaS) operation. This access has allowed them to gain more information about the platform, which is still in its early development phase.
You might be interested in: 7 Data Breach Disasters – Lessons for Cybersecurity Awareness Month
Group-IB, a cybersecurity firm based in Singapore, reported that they successfully contacted the operator behind Cicada3301 through the Tox messaging service on the RAMP cybercrime forum. The threat actor had previously posted an ad looking to recruit affiliates for their program.
Researchers Nikolay Kichatov and Sharmine Low published a detailed analysis, revealing the structure of the affiliate panel. It includes sections such as a dashboard, news updates, a company management tool, communication channels, account settings, and a FAQ section.
Cicada3301’s Connection to BlackCat and Early Activity
Cicada3301 first appeared on the radar in June 2024, when researchers noticed similarities between its source code and the now-defunct BlackCat ransomware gang. Since then, it has been linked to at least 30 attacks on organizations across key sectors, particularly in the United States and the United Kingdom.
The ransomware, built using the Rust programming language, is highly versatile and can target various operating systems, including Windows, Ubuntu, Debian, CentOS, and many others. Affiliates can use it to attack systems running on PowerPC, NAS, ESXi, and even network-attached storage devices.
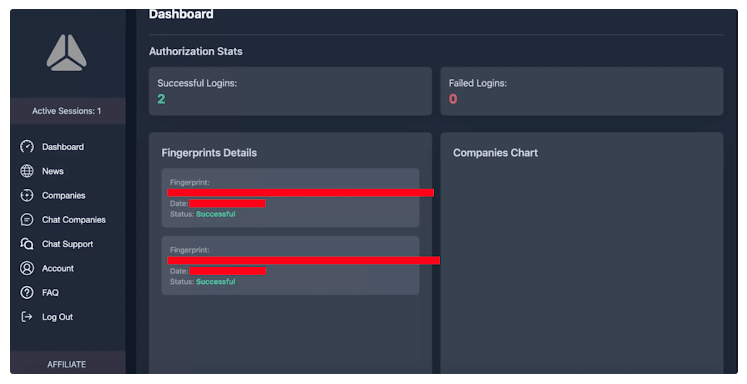
How Cicada3301 Operates
Similar to other ransomware strains, Cicada3301 encrypts data either fully or partially. This is done after virtual machines are shut down, system recovery is blocked, and critical services and processes are stopped. The ransomware can also encrypt network shares, maximizing its impact.
Affiliate Program and Tools
The affiliate program offered by Cicada3301 targets penetration testers (pentesters) and access brokers. Participants can earn a 20% commission, and they are provided with a web-based dashboard packed with features to assist with their operations.
Key Sections of the Affiliate Panel:
- Dashboard: Offers a quick overview of the number of organizations attacked, along with affiliate login history (successful or unsuccessful).
- News: Contains updates on the Cicada3301 platform, including product enhancements and news relevant to affiliates.
- Companies: Allows affiliates to input victim information, such as company names, ransom amounts, and expiration dates for discounts, and to generate Cicada3301 ransomware builds.
- Chat Companies: Provides a communication channel for victims to negotiate ransom payments.
- Chat Support: Affiliates can use this section to contact the Cicada3301 team for help with any issues.
- Account Management: Contains settings for managing affiliate accounts, including password resets.
- FAQ: Offers guidelines on how to add victims, configure ransomware builds, and execute the malware on different operating systems.
By infiltrating the affiliate panel, cybersecurity researchers now have a clearer understanding of Cicada3301’s structure and how the group recruits and manages affiliates. While the RaaS platform is still developing, the threat it poses is growing, particularly with its ability to target such a wide range of systems.
