Critical ICS Vulnerabilities This Week Demand Immediate Attention
Critical ICS Vulnerabilities
This week’s Cyble ICS vulnerability report uncovers severe security flaws in systems from Schneider Electric, mySCADA, and Automated Logic and Critical ICS Vulnerabilities. Vulnerabilities like CVE-2024-10575, CVE-2024-47407, and CVE-2024-8525 pose significant risks and require immediate fixes.
You might be interested in: 145,000 Industrial Control Systems Vulnerable Across 175 Countries
CRIL’s Analysis Highlights Growing Concerns
Between November 19 and 25, 2024, Cyble Research and Intelligence Labs (CRIL) analyzed the latest vulnerabilities reported by the Cybersecurity and Infrastructure Security Agency (CISA) affecting Industrial Control Systems (ICS). These issues raise serious security concerns across vital sectors like manufacturing, energy, and communications.
Most Critical ICS Vulnerabilities This Week
Schneider Electric’s CVE-2024-10575
- Product: EcoStruxure IT Gateway
- Severity: High
- Issue: Missing Authorization
- Impact: Allows unauthorized access to critical systems, increasing the risk of data breaches and operational disruptions.
- Patch Link
mySCADA’s CVE-2024-47407
- Product: myPRO Manager/Runtime
- Severity: Critical
- Issue: Operating System Command Injection
- Impact: Enables remote execution of arbitrary commands, compromising SCADA and HMI systems.
- Patch Link
Automated Logic’s CVE-2024-8525
- Product: WebCTRL Server v7.0
- Severity: High
- Issue: Unrestricted File Upload
- Impact: Allows uploading of malicious files to building automation systems.
- Patch Link
Schneider Electric’s CVE-2024-8933
- Product: Modicon M340, MC80, Momentum
- Severity: High
- Issue: Message Integrity Bypass
- Impact: Potential manipulation of system communications.
- Patch Link
mySCADA’s CVE-2024-50054
- Product: myPRO Manager/Runtime
- Severity: High
- Issue: Path Traversal
- Impact: Unauthorized access to files, leading to data compromise.
- Patch Link
For a full list of vulnerabilities and solutions, consider subscribing to Cyble’s AI-powered threat intelligence suite.
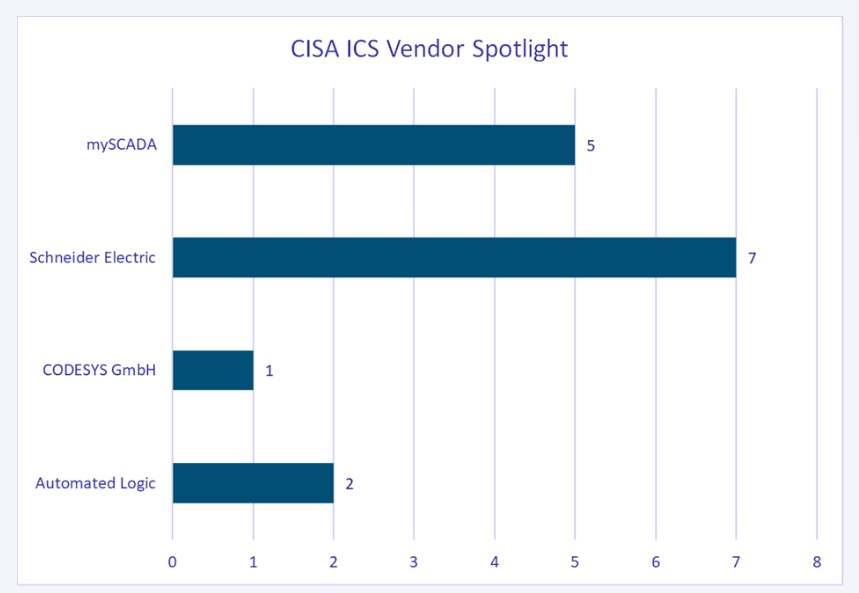
Vendor Spotlight
- Schneider Electric: Reported 50% of the vulnerabilities, affecting energy management and industrial automation systems.
- mySCADA: Accounted for 33% of the vulnerabilities, highlighting issues in SCADA and HMI systems.
- Automated Logic and CODESYS GmbH: Made up 17% of the vulnerabilities, impacting building automation and PLC software.
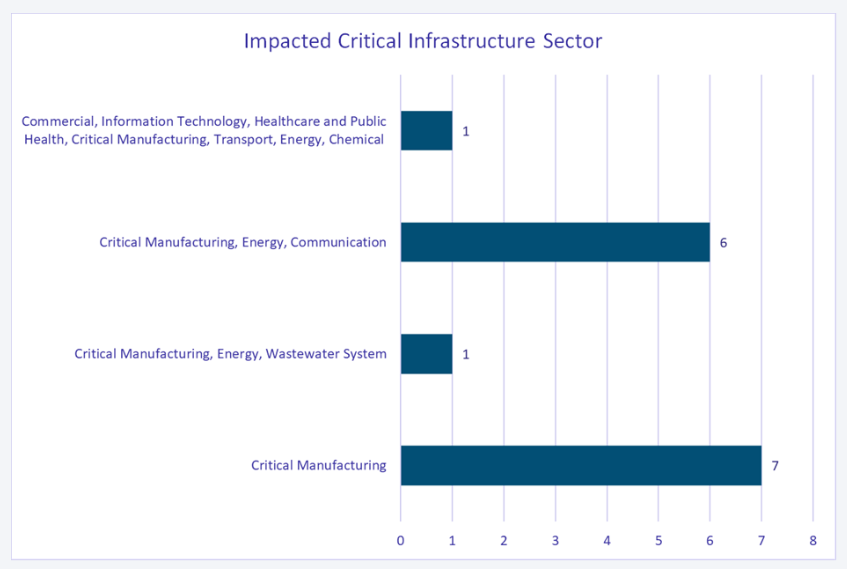
Impacted Critical Infrastructure Sectors
- Critical Manufacturing: Most affected sector, with 50% of the vulnerabilities.
- Manufacturing, Energy, and Communications: Together accounted for 43% of the vulnerabilities, emphasizing the interconnectedness of these industries.
Recommendations
To address these vulnerabilities and minimize risks, CRIL advises:
- Stay Informed: Regularly review security advisories from vendors and agencies like CISA.
- Implement Zero Trust: Limit access to critical systems using risk-based access controls.
- Network Segmentation: Isolate vulnerable ICS components to prevent lateral movement by attackers.
- Effective Patch Management: Develop a strategy to inventory, assess, test, and deploy patches promptly.
- Regular Security Assessments: Conduct vulnerability scans, penetration tests, and audits to identify weaknesses.
- Enhance Access Security: Restrict access to ICS devices and enforce strong authentication methods.
- Develop Incident Response Plans: Establish and routinely test procedures for detecting and responding to cyber incidents.
- Employee Training: Educate staff to recognize phishing attempts and adhere to security policies.
Conclusion
This week’s ICS vulnerability report highlights the persistent threats facing critical infrastructure. The discovery of vulnerabilities in products from Schneider Electric, mySCADA, and Automated Logic underscores the need to prioritize cybersecurity to safeguard essential systems.
Immediate patching of critical vulnerabilities, enhanced monitoring, and overall strengthening of cybersecurity measures are crucial. Proactive steps are necessary to mitigate risks and ensure the uninterrupted operation of vital services.
