Crypto Scam Exposed: Fake Seed Phrases to Steal Wallet Funds
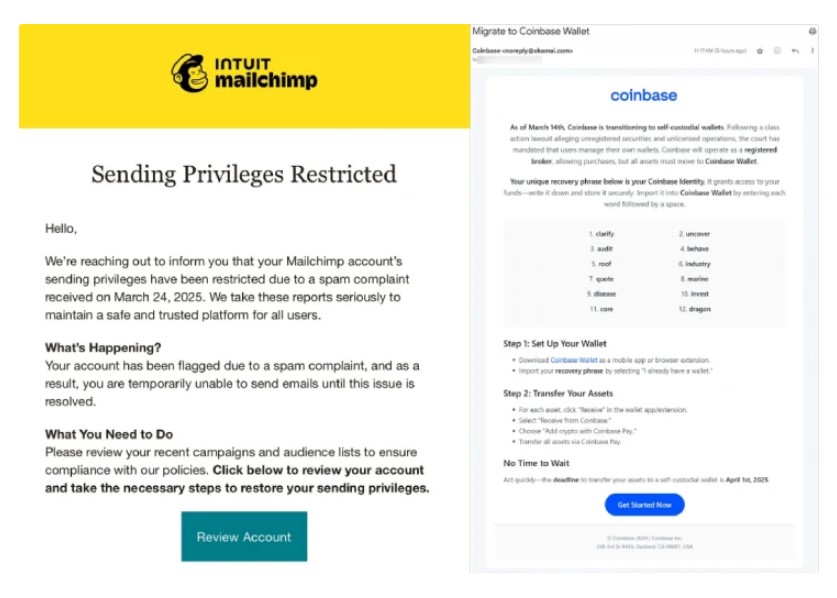
A fresh Crypto Scam is making the rounds that tricks both individuals and companies into setting up cryptocurrency wallets with bogus recovery phrases. Cybercriminals have found a way to break into customer management systems and bulk email services to send out deceptive emails. Their goal is simple: get unsuspecting victims to use a fake seed phrase that ultimately gives them full control of the wallet.
You might be interested in: Outlaw Botnet: A Growing Crypto Threat
How the Crypto Scam Works
The scam begins with the attackers compromising user credentials for popular customer relationship management tools and email marketing services. Using these stolen details, they gain access to mailing lists and then send out a flood of emails. Each email contains what appears to be a secure recovery or seed phrase for a new cryptocurrency wallet. The instructions urge the recipient to copy the seed phrase into a new wallet setup. However, as soon as the wallet is created with the provided phrase, the scammers quickly hijack it and transfer out any funds.
Here’s a step-by-step breakdown:
-
Access Gained: The attackers infiltrate CRM tools and email providers using stolen login details.
-
API Key Creation: They create API keys to keep their access even if the passwords are later changed.
-
Bulk Email Dispatch: Using the access, they extract mailing lists and send out thousands of deceptive emails.
-
Phishing for Wallets: The emails instruct users to set up new cryptocurrency wallets using the embedded recovery phrase.
-
Wallet Hijacking: Once the new wallet is activated with the fake seed phrase, the criminals seize control and drain the funds.
Who Is Being Targeted by this Crypto Scam
This scam isn’t limited to cryptocurrency enthusiasts. The attack reaches far and wide:
-
Crypto Platforms: Major names like Coinbase and Ledger are in the crosshairs.
-
Email Providers: The attackers have also targeted services such as Mailchimp, SendGrid, Hubspot, Mailgun, and Zoho.
-
Broader Audience: Enterprise organizations and individuals outside the typical crypto space are also being tricked. By compromising widely used platforms, the attackers increase their reach and improve their odds of success.
Exploiting Security Weaknesses
What makes this scam particularly dangerous is its clever use of existing digital infrastructures:
-
Lookalike Phishing Pages: The criminals set up fake login pages that mimic trusted CRM and email providers. This tactic tricks high-value targets into entering their credentials.
-
Persistent Access: Even if a password is reset, the creation of an API key allows the attackers to maintain access.
-
Automated Tools: Automated software helps extract mailing lists and send bulk emails quickly, making the attack both fast and efficient.
Additional Malware Threats in the Scene
In a related development, a separate Russian-speaking threat actor has been identified using Cloudflare’s hosting services for phishing attacks. This actor:
-
Phishing via Cloudflare: Uses Cloudflare Pages.Dev and Workers.Dev to host pages that look like official DMCA notice sites.
-
Malicious Downloads: Tricks victims into downloading files disguised as PDFs, which are in reality malicious LNK files.
-
Remote Control: Once executed, the file contacts a Telegram bot with the victim’s IP address before handing control over to a command-and-control server.
-
Legacy Malware: Previous versions of this campaign also spread a tool called StealC, designed to gather sensitive information.
Conclusion
This evolving threat shows that cybercriminals are not only refining their phishing techniques but are also broadening their targets. By leveraging compromised CRM and email accounts, they can spread deceptive messages that lead victims to create wallets with fake seed phrases. The combination of sophisticated access methods and automated tools makes this scam a formidable threat to both crypto users and broader organizations. Awareness and robust security practices, such as multifactor authentication and regular credential updates, are crucial defenses against such attacks.