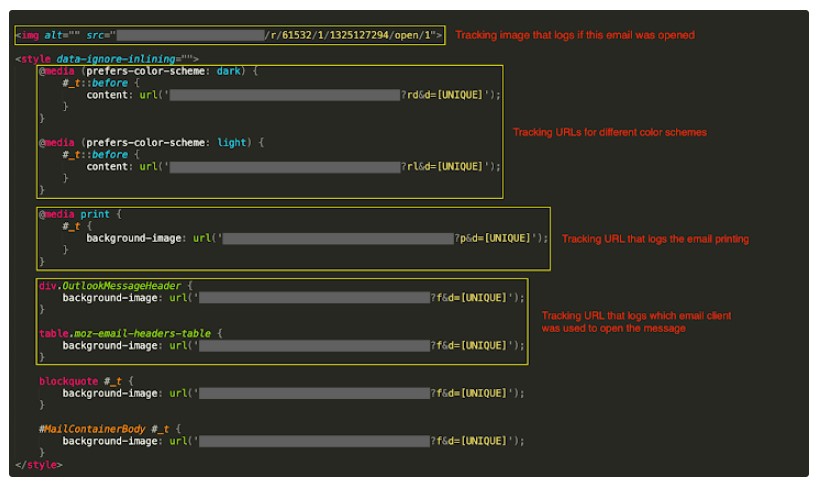
CSS exploits in emails are tracking your actions and data.
Introduction
Cybercriminals have found a new way to sneak past email filters and secretly monitor user actions by misusing basic CSS exploits. CSS, a tool normally used to add style and structure to web pages, is now being manipulated in emails to hide extra content and gather details about the recipient’s environment without their knowledge.
You might be interested in: How SSRF Exploits Can Steal Your Cloud Credentials and Sensitive Data
How the Trick Works
Typically, CSS helps set the look of a webpage by controlling elements like colors, fonts, and layout. However, attackers are now taking advantage of CSS settings such as text indentation and opacity. By tweaking these properties, they can hide extra text or links that are not visible when the email is rendered. This hidden content might include deceptive links or codes designed to bypass standard spam filters, making it easier for harmful emails to reach your inbox.
Tracking Through CSS
Beyond hiding unwanted content, CSS is being used as a tool for tracking. Attackers embed specific CSS rules—like the @media rule—to gather information about your email setup. These rules can detect details about your screen size, resolution, and even the color scheme you use. In some cases, they can monitor if you’ve opened, viewed, or printed an email. This kind of fingerprinting allows cybercriminals to build a profile of your online habits and preferences, which can be exploited for more targeted attacks.
Security and Privacy Concerns
The misuse of CSS in this way poses serious risks. When hidden content is used to bypass email security, it opens the door to phishing scams where you might be redirected to dangerous websites. This redirection can lead to further attacks, including attempts to steal personal information or install malware. Moreover, the ability to track user actions without clear consent undermines your privacy, as it gives attackers insights into how you interact with your emails and what devices or settings you use.
What You Should Know
Recent studies from cybersecurity researchers highlight that even simple CSS tricks can have a big impact on both email security and user privacy. By using everyday features of HTML and CSS, attackers can effectively trick email security systems. The fact that these techniques use standard web design methods makes them particularly tricky to detect with older security filters that are not designed to scrutinize CSS behavior.
How to Protect Yourself
To guard against these new tactics, consider the following steps:
- Upgrade Your Email Filters: Modern spam filters should be updated to recognize unusual patterns in CSS usage, such as hidden text or irregular property values.
- Use Email Privacy Tools: Consider tools like privacy proxies that can help shield your email interactions from unwanted tracking.
- Keep Software Up-to-Date: Regularly update your email client and security software to ensure you have the latest protections against emerging threats.
- Be Cautious with Unfamiliar Emails: If you receive emails from unknown senders or ones that seem off, it might be wise to avoid clicking on links or downloading attachments.
Final Thoughts
The exploitation of CSS in email scams is a clever, yet dangerous, tactic that turns a basic design tool into a means of bypassing filters and spying on users. As attackers continue to refine these techniques, it becomes ever more important for both users and security systems to adapt. By staying informed and taking simple protective measures, you can reduce the risk of falling victim to these innovative cyber threats.