Fake Google Ads Campaign Steals Account Credentials
Overview of the Threat
Cybersecurity researchers have discovered a new scheme targeting individuals and businesses using Google Ads. This campaign tricks users into handing over their account credentials by presenting fake Google Ads that lead to phishing sites. According to Jérôme Segura, senior director of threat intelligence at Malwarebytes, these bad actors are impersonating Google Ads and redirecting victims to counterfeit login pages in order to steal their login information.
You might be interested in: Exploitation of Vulnerability in Aviatrix Controller
How the Scam Works
The attackers’ main goal is to collect as many Google Ads account credentials as possible. After obtaining these credentials, they use the compromised accounts to run their own ads or sell the account information on underground forums. Reports from Reddit, Bluesky, and Google’s support pages suggest this activity has been going on since at least mid-November 2024.
This campaign is similar to previous attacks that used malware to take over Facebook business accounts. Once these accounts were compromised, they were used to launch further malicious advertising efforts, spreading the scam even more widely.
Tactics Used by Attackers
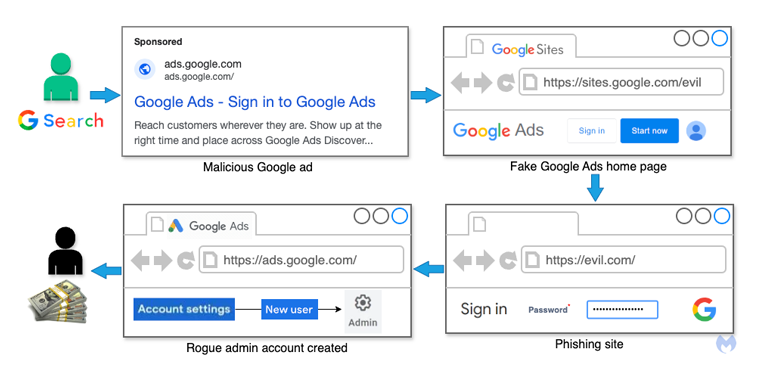
The scam targets users searching for Google Ads through Google’s own search engine. When users click on fake Google Ads links, they’re redirected to deceptive pages hosted on Google Sites. These pages then guide visitors to phishing sites where they’re asked to enter their credentials and two-factor authentication codes. The stolen data is immediately sent to the attacker’s server.
Some of these fake ads come from compromised accounts belonging to legitimate organizations, including businesses and even a regional airport. Many of these accounts had already been running hundreds of valid ads before they were hijacked.
Exploiting Google Ads’ Rules
The attackers exploit the fact that Google Ads doesn’t require the final URL—the page users reach after clicking an ad—to match the display URL exactly, as long as the domains are the same. This allows them to create misleading ads that appear to be from Google Ads (ads.google[.]com) but actually redirect to malicious landing pages hosted on sites.google[.]com.
In addition, the attackers use advanced techniques to hide their activities. These include fingerprinting, detecting bot traffic, adding CAPTCHA-style verification steps, and using cloaking and code obfuscation. These measures make it harder for automated systems to identify and block their malicious sites.
What Happens to Stolen Credentials?
After stealing a victim’s credentials, the attackers log into the compromised account, add a new admin user, and use the account’s budget to run their own fake ads. The funds from these ads help them capture even more accounts, creating a cycle that perpetuates the scam.
Researchers believe several groups are involved in these attacks, many of them Portuguese speakers operating out of Brazil. The phishing infrastructure often relies on .pt domains, which are associated with Portugal.
This campaign highlights a loophole in Google Ads’ policies: attackers can display deceptive URLs in their ads without being flagged. Until Google takes stronger action to secure these accounts, the attacks are likely to continue.
Broader Trends in Malware Distribution
Beyond Google Ads, similar methods have been observed elsewhere. Trend Micro recently revealed that attackers are distributing malware through platforms like YouTube and SoundCloud by linking to fake installers for popular software. These fake downloads often lead to malware such as Amadey, Lumma Stealer, Mars Stealer, Penguish, PrivateLoader, and Vidar Stealer. The attackers frequently use well-known file hosting services (e.g., Mediafire, Mega.nz) to mask their operations and make detection harder. Many of the malicious files are password-protected or encoded to evade detection by security tools.
