FINALDRAFT Spyware Targets Windows and Linux Systems
Overview of the Threat
Cybersecurity experts have uncovered a new hacking campaign targeting the foreign ministry of an undisclosed South American country. The attackers are using custom-built malware FINALDRAFT Spyware designed to gain remote access to infected systems.
You might be interested in: Urgent iOS Update Patches Major Security Bug
Researchers at Elastic Security Labs linked this campaign to a hacker group they call REF7707. The attack, first detected in November 2024, has also affected a university and a telecom company in Southeast Asia.
Weaknesses in FINALDRAFT Spyware Attack Execution
Although the hackers behind REF7707 have developed a sophisticated set of tools, experts found flaws in their strategy. Security analysts Andrew Pease and Seth Goodwin noted that the group lacked consistency in covering its tracks and managing the operation effectively.
How the FINALDRAFT Spyware Attack Works
The exact way the hackers initially infiltrated the systems remains unclear. However, investigators found that the attack involved the misuse of Microsoft’s certutil tool, which was used to download additional malicious files from a server connected to the targeted foreign ministry.
One key finding is that hackers used a Remote Shell plugin (WinrsHost.exe) to execute certutil commands. These actions were carried out from an unknown system already connected to the network. This suggests the attackers had stolen valid login credentials and were moving across the network from a previously compromised machine.
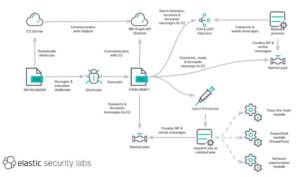
The Role of PATHLOADER and FINALDRAFT Spyware
The first malicious file executed is a program called PATHLOADER. This software runs encrypted shellcode received from an external server. The extracted shellcode is then injected into a new instance of “mspaint.exe,” which is renamed “FINALDRAFT.”
FINALDRAFT, written in C++, is a powerful remote administration tool capable of loading additional modules as needed. It also exploits the Microsoft Graph API to misuse Outlook’s email service for command-and-control (C2) operations. A similar approach was previously seen in another backdoor malware known as SIESTAGRAPH.
How FINALDRAFT Communicates
Instead of directly communicating with a command server, FINALDRAFT retrieves instructions stored in the drafts folder of a compromised mailbox. After executing commands, it saves the results as new draft emails. The malware includes 37 different command functions, allowing it to manipulate files, inject malicious processes, and act as a network proxy.
Advanced Evasion Techniques
The malware is also designed to launch new processes using stolen NTLM credentials and run PowerShell commands without using the “powershell.exe” file. Instead, it leverages PowerPick, a legitimate tool from the Empire post-exploitation framework. It also modifies key Windows APIs to bypass security monitoring tools like Event Tracing for Windows (ETW).
Linux Version of FINALDRAFT Spyware
Investigators also discovered a Linux version of FINALDRAFT after finding ELF binary files on VirusTotal, uploaded from Brazil and the United States. The Linux variant can execute shell commands and delete itself to avoid detection.
Conclusion: A Well-Organized Espionage Operation
Security researchers believe the level of sophistication in these tools indicates a well-coordinated effort. The duration of the campaign and the attack patterns suggest it is likely part of an espionage operation aimed at gathering sensitive information.
While the attackers demonstrated technical skill in developing their malware, their poor operational management left traces that helped security experts uncover the campaign. Organizations are advised to strengthen security measures to detect and prevent such attacks in the future.
