Fortinet Flaw Triggers CISA Alert, Patches from Cisco, Palo Alto
On Wednesday, the United States Cybersecurity and Infrastructure Security Agency (CISA) flagged a major security vulnerability affecting Fortinet devices by adding it to the Known Exploited Vulnerabilities (KEV) database. This action was taken due to confirmed instances of the vulnerability being actively used in attacks.
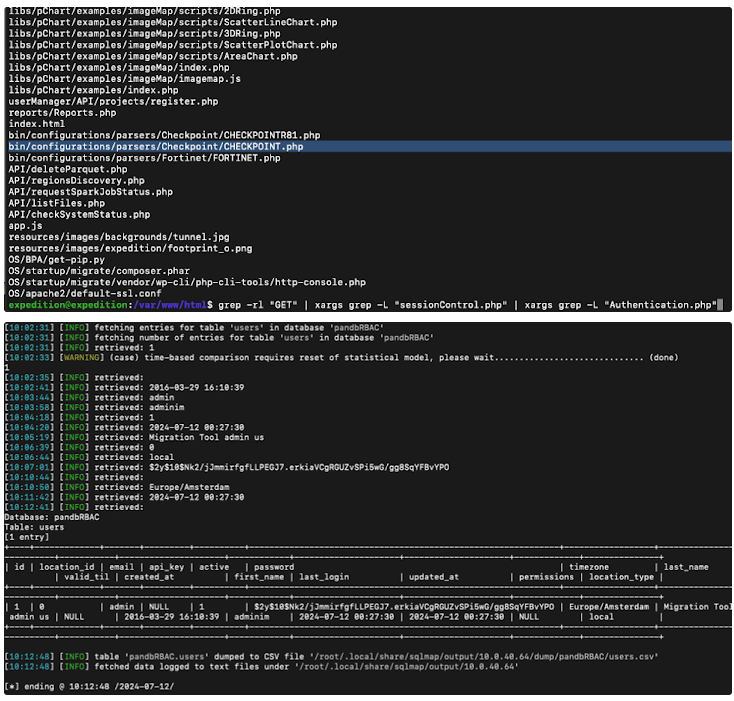
The vulnerability, designated CVE-2024-23113, carries a high severity score of 9.8 on the CVSS scale. It affects various Fortinet products, including FortiOS, FortiPAM, FortiProxy, and FortiWeb, and could lead to remote code execution.
Fortinet’s Security Advisory and Details
Back in February 2024, Fortinet issued an advisory explaining that a “use of externally-controlled format string vulnerability” in the FortiOS fgfmd daemon could allow unauthenticated attackers to execute arbitrary commands. This type of vulnerability is classified as CWE-134. Essentially, it means that a hacker can send malicious requests to the system, giving them control over the device.
Though the advisory provided general information on the issue, it did not go into detail about how the vulnerability is being exploited in real-world scenarios or who might be behind the attacks. However, the vulnerability’s severity and active exploitation make it a critical threat.
Mandatory Mitigations for Federal Agencies
Federal Civilian Executive Branch (FCEB) agencies have been instructed to apply the patches and mitigations provided by Fortinet by October 30, 2024, to protect their systems from ongoing attacks.
Palo Alto Networks Highlights Security Flaws in Expedition
Command Injection and Other Vulnerabilities
In addition to the Fortinet alert, Palo Alto Networks identified significant security flaws in their Expedition tool. These vulnerabilities could potentially allow attackers to access sensitive information, like usernames, passwords, and device configurations, or even execute commands as the system’s root user.
Here’s a breakdown of the most serious vulnerabilities:
- CVE-2024-9463: Rated 9.9 on the CVSS scale, this flaw allows unauthorized users to execute commands as root.
- CVE-2024-9464: This vulnerability, rated 9.3, enables authenticated users to execute system commands as root.
- CVE-2024-9465: Rated 9.2, this SQL injection vulnerability can be exploited by an unauthenticated attacker to access the Expedition database.
- CVE-2024-9466: A cleartext storage issue, rated 8.2, could lead to the exposure of sensitive information such as passwords and API keys.
- CVE-2024-9467: This vulnerability, rated 7.0, is a reflected cross-site scripting (XSS) issue that could allow phishing attacks and session hijacking for authenticated users.
Identifying and Addressing the Issues
These vulnerabilities were discovered and reported by Zach Hanley from Horizon3.ai and Enrique Castillo from Palo Alto Networks. Although the methods to exploit these vulnerabilities have been published online, there is currently no evidence of widespread exploitation.
To mitigate these risks, Palo Alto Networks advises restricting Expedition access to authorized users, hosts, and networks. Additionally, they recommend shutting down the system when it is not in use.
Cisco Fixes Critical Command Injection Bug
Nexus Dashboard Fabric Controller Vulnerability
Last week, Cisco released a patch to fix a serious vulnerability in its Nexus Dashboard Fabric Controller (NDFC). This vulnerability, tracked as CVE-2024-20432 and carrying a CVSS score of 9.9, could allow a remote, authenticated attacker with low privileges to execute malicious commands on affected systems.
This issue, caused by improper validation of command parameters and user authorization, has been resolved in NDFC version 12.2.2. It’s important to note that earlier versions, like 11.5, are not affected.
According to Cisco, attackers could exploit this vulnerability by sending specially crafted commands to the system via the REST API or web UI. If successful, the attacker could gain control over a device managed by Cisco NDFC and execute arbitrary commands with elevated network-admin privileges.
What To Do Next?
For both Fortinet and Cisco users, applying patches immediately is crucial to avoid falling victim to these active and potentially devastating vulnerabilities. Keeping systems updated is the best defense against these types of exploits.