Gophish Toolkit Delivers Remote Access Trojans
A new phishing campaign has emerged, primarily targeting Russian-speaking consumers. The attackers are leveraging Gophish, an open-source toolkit, to distribute DarkCrystal RAT (DCRat) and a new remote access trojan called PowerRAT.
You might be interested in: 7 Data Breach Disasters – Lessons for Cybersecurity Awareness Month
Cisco Talos researcher, Chetan Raghuprasad, recently uncovered the details of this campaign. It uses malicious documents (Maldoc) or infected HTML files to trick victims into taking action, which ultimately leads to infection.
How the Phishing Attack Works
The phishing emails are written in Russian, using familiar elements to gain trust, such as:
- Bait text designed to lure victims into opening malicious attachments.
- Links disguised as Yandex Disk (e.g., “disk-yandex[.]ru”).
- HTML pages posing as VK, a popular Russian social media platform.
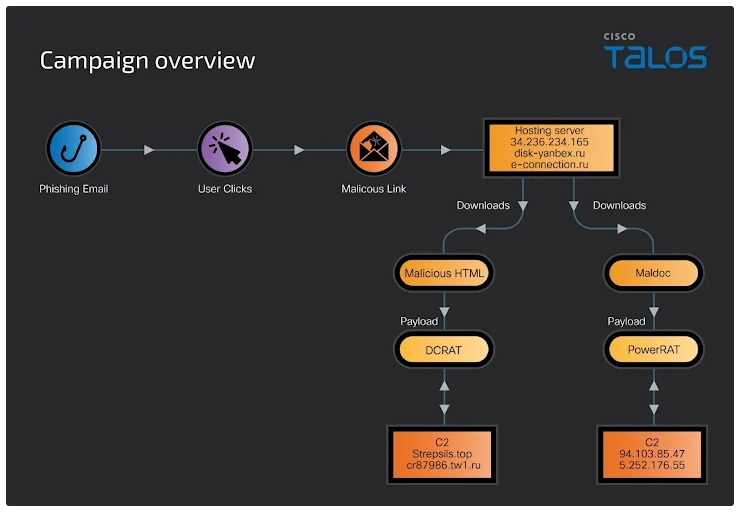
The attackers use Gophish to send out these phishing emails, which either deliver DCRat or PowerRAT depending on the initial method of attack. The infected files are typically harmful Word documents or HTML files loaded with malicious JavaScript.
Technical Breakdown of the Malware
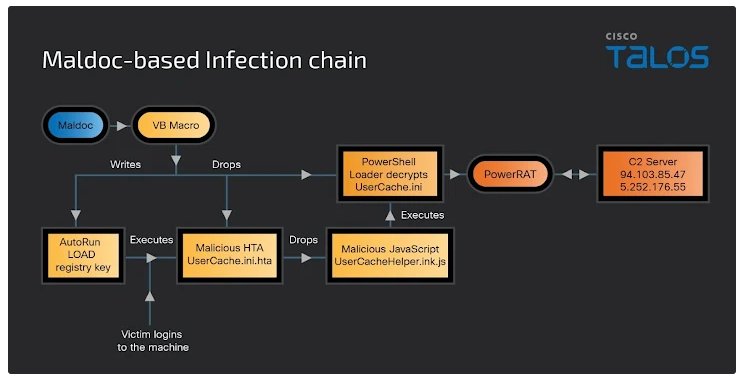
PowerRAT Infection Chain
When a victim interacts with the malicious file, here’s how PowerRAT is deployed:
- Macro Activation: If the victim opens the document and enables macros, a Visual Basic (VB) macro gets triggered.
- File Extraction: This macro extracts two files: an HTML Application (HTA) file named “UserCache.ini.hta” and a PowerShell loader called “UserCache.ini.”
- Persistence Setup: The macro configures a Windows Registry key to ensure the HTA file runs each time the system is restarted.
- Malware Execution: The HTA file runs a JavaScript file that, in turn, launches the PowerShell loader, which is disguised as an INI file. This loader contains base64-encoded data that eventually loads and runs PowerRAT in the system memory.
PowerRAT Capabilities
Once PowerRAT is active, it begins to monitor the infected system. It captures details like the serial number of the victim’s drive and communicates with a remote server located in Russia for further instructions. The malware is designed to execute additional PowerShell commands, enabling the attackers to escalate the attack by launching further infections.
If the server doesn’t respond, PowerRAT can still function by decoding and executing embedded PowerShell scripts. However, the samples analyzed so far suggest that the malware is still under active development, and new features may be added.
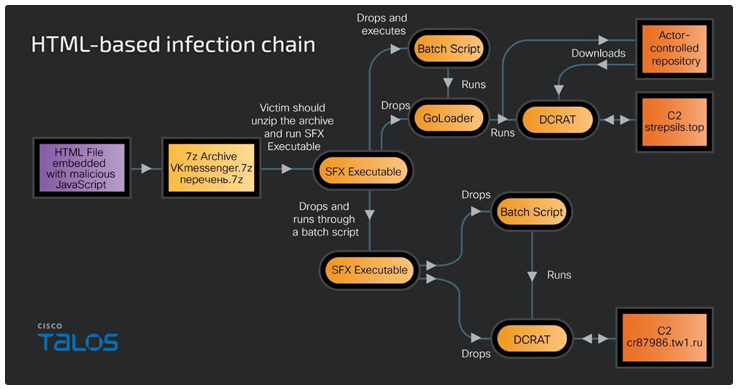
DCRat Infection Chain
The campaign also utilizes DCRat, a more modular RAT capable of advanced spying activities. The infection process for DCRat begins when a victim clicks on a malicious link in the phishing email. This action opens an HTML file loaded with JavaScript, which immediately starts executing.
The script contains a base64-encoded data blob that hides a 7-Zip archive packed with a password-protected SFX RAR file. This archive holds the RAT payload.
Once extracted, the RAT is loaded onto the victim’s machine, where it can steal data, capture screenshots, log keystrokes, and take full control of the system.
Conclusion
This phishing campaign highlights the dangers posed by open-source tools like Gophish when used by malicious actors. Russian-speaking users should be wary of unsolicited emails, especially those containing suspicious links or attachments.
Both DarkCrystal RAT and PowerRAT are designed to give attackers full control over the infected system, making these types of phishing attacks particularly dangerous. With continued development, these tools will likely evolve, increasing the threat they pose to consumers.
Stay vigilant and ensure your security measures are up to date to avoid becoming a victim of these sophisticated phishing operations.