Hackers Are Using Blockchain to Steal Your Passwords
A financially-driven hacking group, identified as UNC5142, has pioneered a disturbing new method for spreading data-stealing malware. By embedding malicious code within blockchain smart contracts, these criminals are infecting both Windows and macOS computers with dangerous stealers like Atomic, Lumma, and Vidar. This innovative technique makes their attacks incredibly resilient and difficult to track.
According to Google’s Threat Intelligence Group (GTIG), the hackers are compromising thousands of WordPress websites and using a method they call “EtherHiding.” This involves hiding their malicious instructions on a public blockchain, specifically the BNB Smart Chain, which is normally used for cryptocurrency transactions. This allows them to blend in with legitimate web traffic, making their activities much harder to detect and shut down.
A New Twist on Hacking Websites
The attack begins when UNC5142 hacks into poorly secured WordPress websites. They inject a piece of malicious JavaScript code into the site’s files or database. As of June 2025, Google had found this code on roughly 14,000 different web pages, showing how widespread their operation is.
This initial code, known as CLEARSHORT, doesn’t contain the virus itself. Instead, it acts as a downloader. Its sole purpose is to reach out to the BNB Smart Chain and interact with a malicious smart contract created by the hackers. This two-step process is what makes the attack so clever. Even if the initial code on the website is discovered, the core of the attack infrastructure remains hidden and active on the blockchain.
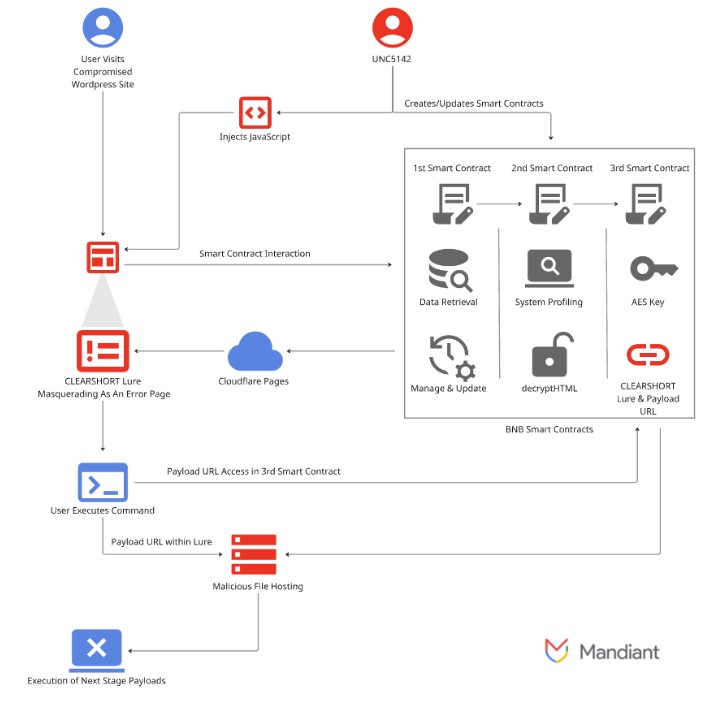
Using Smart Contracts as a Secret Weapon
The use of the blockchain is the key to UNC5142’s success. A smart contract is essentially a program that runs on a blockchain. While the program’s code itself cannot be changed once deployed, the data it points to can be updated. The hackers exploit this feature perfectly.
The smart contract holds the web address (URL) of a landing page that continues the infection. By simply paying a tiny network fee—sometimes as little as $0.25—the hackers can update the smart contract to point to a new malicious server. This means they don’t have to re-hack thousands of websites every time one of their servers gets taken down. They just update the “address” stored on the blockchain, and all the infected websites will automatically start directing victims to the new location. This makes their campaign incredibly agile and resistant to traditional takedown efforts.
The Final Trap: How They Trick You
Once the smart contract provides the address, the victim’s browser is directed to a malicious landing page. Here, the hackers use social engineering tactics to trick the user into infecting their own computer. They display fake pop-ups, such as a phony browser update warning, that instruct the user to copy a command and paste it into their system’s command line tool—the Run dialog on Windows or the Terminal app on macOS.
- For Windows users, the command downloads a special file that then runs a PowerShell script. This script downloads the final password-stealing malware directly into the computer’s memory. By avoiding writing the virus to the hard drive, this “fileless” attack is much more likely to evade detection by antivirus software.
- For macOS users, the command downloaded and ran a script that would pull the Atomic Stealer malware from a remote server, infecting the Apple device.
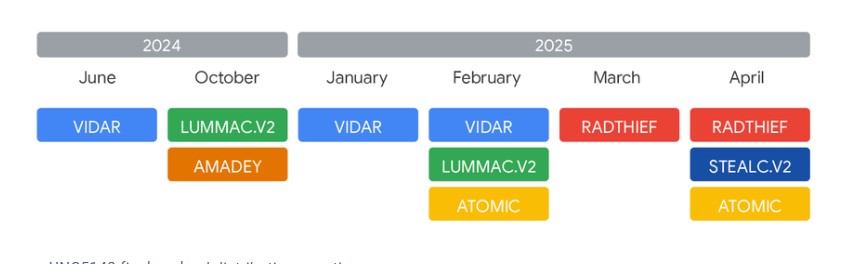
A Constantly Evolving Attack
Google’s research shows that UNC5142’s tactics have become more sophisticated over time. In late 2024, they upgraded from a single smart contract to a more complex three-contract system. This setup works like a highly organized system: one contract acts as the permanent public address, a second “logic” contract holds the current attack instructions (like the malicious URL), and a third “storage” contract holds the data. This allows them to make rapid changes to their campaign with minimal effort.
The group even operates two separate sets of blockchain infrastructures, a “Main” and a “Secondary” one, likely to test new strategies or to ensure their operations can continue even if one is disrupted. Although Google noted a pause in their activity after July 23, 2025, the group’s consistent operations and continuous evolution suggest they have been highly successful. Their break could simply be a temporary pause before they return with even more advanced techniques.
