Malware Campaign Deploys DarkVision RAT via PureCrypter
Cybersecurity researchers have recently identified a new malware campaign that is actively spreading a remote access trojan (RAT) known as DarkVision RAT. The malicious actors behind this campaign are utilizing a malware loader called PureCrypter to deliver the RAT to unsuspecting victims. This discovery highlights the ongoing efforts by cybercriminals to develop sophisticated tools for infiltrating systems and stealing sensitive information.
You might be interested in: The Rise of Phishing as a Service
Multi-Step Process Deploys Malicious Payload
In July 2024, analysts at Zscaler ThreatLabz observed that this campaign employs a complex, multi-stage process to install the DarkVision RAT on targeted systems. The attackers use several layers of loaders and scripts to bypass security measures and ensure the malware remains undetected during the installation process. This intricate method demonstrates the lengths to which cybercriminals will go to achieve their objectives.
How DarkVision RAT Communicates and Its Capabilities
According to security researcher Muhammed Irfan V A, DarkVision RAT communicates with its command-and-control (C2) server using a custom network protocol over sockets. This means it doesn’t rely on standard protocols, making its traffic harder to detect by conventional network monitoring tools.
The RAT is equipped with a wide range of features that allow attackers to:
- Keylogging: Record every keystroke made by the user, potentially capturing passwords, credit card numbers, and personal messages.
- Remote System Access: Gain full control over the victim’s computer, allowing them to execute commands, manage files, and install additional malware.
- Password Theft: Extract saved passwords from web browsers and other applications.
- Audio Recording: Activate the system’s microphone to record conversations.
- Screen Captures: Take screenshots of the user’s activities to gather more information.
These capabilities make DarkVision RAT a potent tool for cyber espionage, financial theft, and data exfiltration.
Understanding PureCrypter Malware Loader
First unveiled in 2022, PureCrypter is a commercial malware loader available on a subscription basis. It enables cybercriminals to distribute various types of malware, including ransomware, information stealers, and remote access trojans. PureCrypter is popular due to its effectiveness in evading detection and its user-friendly interface, which lowers the barrier to entry for less technically skilled attackers.
Unclear Entry Point but Complex Deployment Method
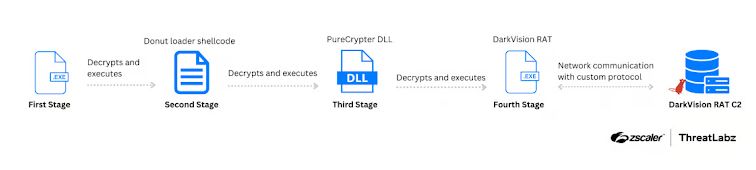
While the exact method used to initially deploy PureCrypter and DarkVision RAT remains unclear, researchers have detailed the subsequent stages of the attack:
- Decryption and Launching of Donut Loader: The process begins with a .NET program that decrypts and executes an open-source tool known as the Donut loader.
- Execution of PureCrypter: The Donut loader then runs PureCrypter, which is responsible for unpacking the DarkVision RAT.
- Deployment of DarkVision RAT: PureCrypter installs the RAT onto the system, ensuring it is ready to carry out malicious activities.
- Establishing Persistence: PureCrypter sets up mechanisms to keep the RAT active on the system, even after reboots, and modifies security settings to prevent detection.
By using multiple layers and tools, the attackers increase their chances of successfully infecting the system without raising alarms.
How the Malware Stays on Infected Systems
To maintain a foothold on the compromised system, the malware employs several persistence techniques:
- Batch Script Creation: It generates a batch script that includes commands to execute the RAT’s executable file.
- Startup Folder Shortcut: A shortcut to this batch script is placed in the Windows startup folder, causing it to run automatically when the user logs in.
- ITaskService COM Interface: The malware uses the ITaskService Component Object Model (COM) interface to interact with the Windows Task Scheduler, allowing it to schedule tasks that run the malware.
- Autorun Registry Keys: It modifies registry keys responsible for running programs at startup, ensuring the RAT launches with the system.
- Scheduled Tasks Creation: By creating scheduled tasks, the malware can execute at specified times or system events, further embedding itself into the system’s operations.
Additionally, PureCrypter adds the RAT’s file paths and process names to the exclusion list of Microsoft Defender Antivirus, preventing the security software from scanning or blocking the malicious files.
DarkVision RAT: An Affordable and Powerful Tool for Attackers
Emerging in 2020, DarkVision RAT is sold openly on a public website for as little as $60 for a one-time purchase. This low cost and ease of access make it an attractive option for cybercriminals, including those with minimal technical expertise looking to launch their own attacks.
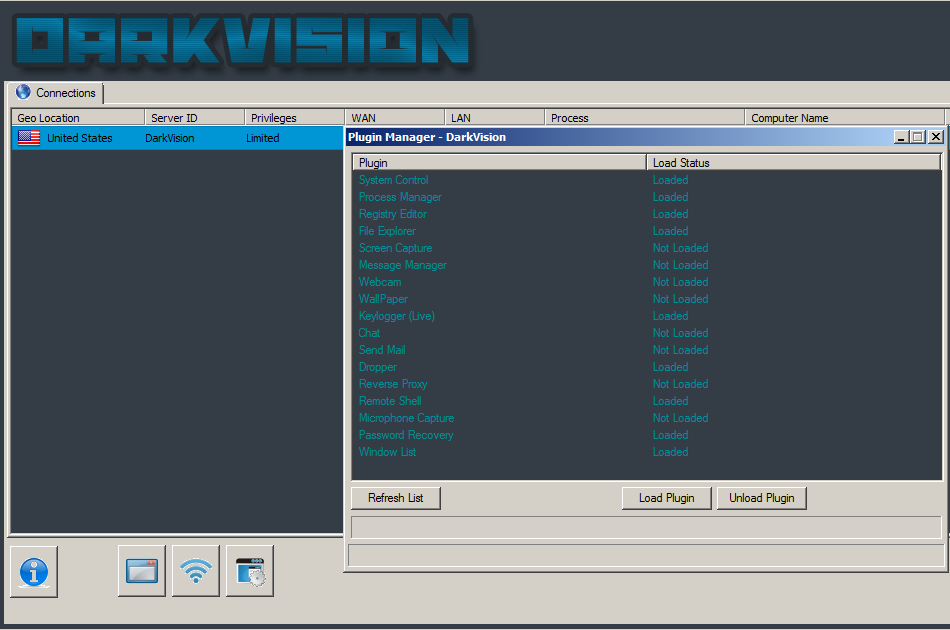
Developed in C++ and assembly language for optimal performance, DarkVision RAT offers a comprehensive suite of features:
- Process Injection: Embedding malicious code into legitimate processes to evade detection.
- Remote Shell Access: Providing attackers with command-line access to the victim’s system, allowing for direct manipulation.
- Reverse Proxy: Using the infected system to route network traffic, masking the attacker’s location and activities.
- Clipboard Control: Accessing and manipulating clipboard contents, potentially capturing copied passwords and other sensitive data.
- Keylogging: Monitoring and recording all keystrokes made by the user.
- Screenshot Capture: Taking images of the user’s screen to monitor activities and gather information.
- Cookie and Password Retrieval: Extracting cookies and saved passwords from web browsers to access online accounts.
Moreover, the RAT is designed to collect detailed system information and can receive additional plugins from its C2 server. This extensibility allows attackers to enhance the malware’s functionality and tailor it to specific targets or objectives.
Growing Popularity Among Cybercriminals
According to Zscaler, “DarkVision RAT is a powerful and flexible tool for cybercriminals, offering a wide range of harmful features from keylogging and screen capture to password theft and remote command execution. Its versatility, combined with low cost and availability on hacking forums and its own website, has led to its growing popularity among attackers.”
The accessibility of such advanced tools lowers the barrier for entry into cybercrime, enabling even novice hackers to carry out sophisticated attacks. This trend is concerning for cybersecurity professionals, as it increases the volume and complexity of threats that organizations and individuals must defend against.
Protecting Against This Threat
Given the advanced techniques employed by this malware campaign, it’s crucial to adopt robust security measures:
- Update Software Regularly: Keep operating systems and applications up to date to patch vulnerabilities that malware could exploit.
- Use Reputable Security Solutions: Install and maintain reliable antivirus and anti-malware programs that can detect and block threats like PureCrypter and DarkVision RAT.
- Educate Users: Provide training on recognizing phishing emails and suspicious downloads, which are common vectors for malware distribution.
- Implement Network Monitoring: Use network security tools to monitor for unusual activity that could indicate a malware infection.
- Restrict Administrative Privileges: Limit user permissions to reduce the potential impact of malware that requires administrative rights.
- Regular Backups: Maintain regular backups of critical data to minimize damage in case of an infection.
Conclusion
The discovery of this new malware campaign underscores the ever-evolving nature of cyber threats. Attackers are continuously developing new tools and methods to bypass security measures and compromise systems. The combination of PureCrypter and DarkVision RAT represents a significant risk due to its sophisticated deployment techniques and the extensive capabilities of the RAT.
Organizations and individuals must remain vigilant and proactive in their cybersecurity efforts. By understanding the threats and implementing comprehensive security strategies, it’s possible to mitigate the risks posed by such malware campaigns.
