Medusa Ransomware on the Rise in 2025 according to the CIA and FBI
Overview
The FBI and CISA have recently warned about a growing threat from the Medusa ransomware group. Recent intelligence shows that attacks by this group are happening almost every day this year, with a nearly 45% increase compared to 2024. This surge has prompted government agencies to issue an urgent advisory.
You might be interested in: The Definite Blueprint for Cybersecurity in Manufacturing
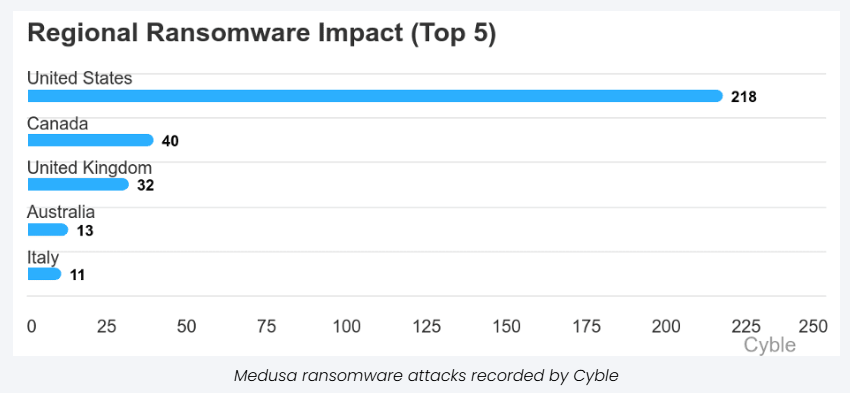
According to data from Cyble, there were 60 Medusa-related incidents in just the first 72 days of 2025. If this trend continues, the total number of attacks could exceed 300 for the year, compared to 211 in 2024. February, in particular, saw a record high with 33 attacks in that 28-day period. More than half of the 414 recorded incidents over the years have targeted organizations in the United States.
Medusa has shown a clear focus on critical sectors. Over 300 victims come from industries such as healthcare, education, law, insurance, technology, and manufacturing. This focus on essential services makes their attacks especially dangerous, as they can disrupt key infrastructure.
How Medusa Operates
The group follows a Ransomware-as-a-Service (RaaS) model, paying out to affiliates who help gain initial access to target networks. They often use phishing emails to steal login details and buy access from brokers on cybercrime forums for fees ranging from $100 to $1 million. Once inside a network, the attackers scan for open ports like FTP (21), SSH (22), and RDP (3389), among others, to gather information.
Commonly scanned ports include:
- 21 (FTP)
- 22 (SSH)
- 23 (Telnet)
- 80 (HTTP)
- 115 (SFTP)
- 443 (HTTPS)
- 1433 (SQL database)
- 3050 (Firebird database)
- 3128 (HTTP web proxy)
- 3306 (MySQL database)
- 3389 (RDP)
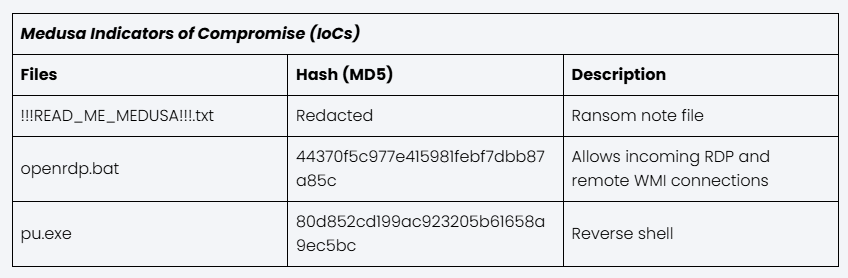
Medusa uses everyday tools such as PowerShell, the Windows command prompt, and system scanners (like Advanced IP Scanner and SoftPerfect Network Scanner) to explore and map out the victim’s network. They also rely on remote access software (such as AnyDesk, ConnectWise, and others) to move laterally through the system and select files to exfiltrate and encrypt.
Staying Safe Against Attacks
The advisory stresses the importance of solid cybersecurity practices to reduce the risk of such attacks. Key steps include:
- Patching Vulnerabilities: Regularly update and secure web-facing systems.
- Employee Training: Teach staff to spot phishing emails and other suspicious activities.
- Zero Trust & Segmentation: Implement strict network controls and segment sensitive data.
- Secure Backups: Maintain backups that are resistant to ransomware attacks.
These basic measures can help organizations build resilience and limit the damage if an attack occurs.
Medusa’s ongoing activity is a clear reminder that constant vigilance and proactive security measures are essential in today’s digital landscape.