North Korean Hackers “the Lazarus Group” Attack Nuclear Engineers
Overview
In January 2024, security experts observed that the Lazarus Group, a well-known hacking collective linked to North Korea, targeted at least two employees of a nuclear-related organization over the span of a month. This effort stood out due to a “complex infection chain” that was used to break into their systems.
You might be interested in: Apple Updates iOS and macOS to Patch Flaw
Operation Dream Job and NukeSped
This latest intrusion was attributed to the long-running cyber espionage campaign known as Operation Dream Job. The security company Kaspersky also refers to it as NukeSped. The operation has been active since at least 2020, first recognized by ClearSky. It has continued to evolve, using different methods to plant malware and gather intelligence.
Targets of The Lazarus Group
Over time, Lazarus Group has often focused on developers and staff in sectors like defense, aerospace, and cryptocurrency, as well as other global industries. They commonly lure these targets with attractive job offers. When victims take the bait, they unknowingly download and run malicious software on their machines.
Methods of Infection
According to Kaspersky’s analysis, Lazarus Group tries several approaches to achieve their goals. Two of these methods are:
- Sending a malicious document or a tampered PDF reader that shows fake job descriptions.
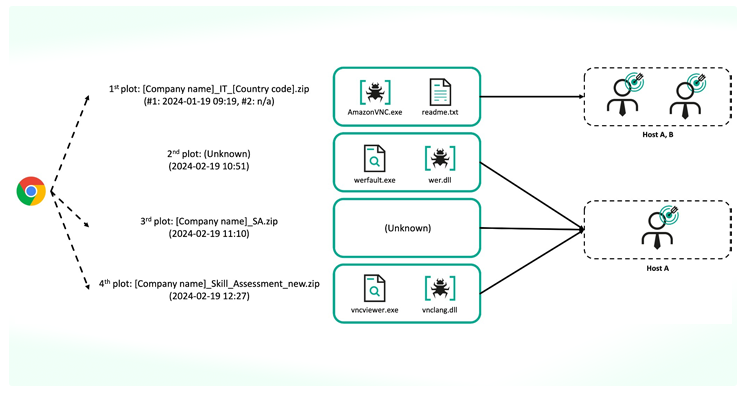
- Sharing a compromised remote access tool—often VNC or PuTTY—to trick the victim into connecting to a certain server for a so-called “skills test.”
The most recent attacks focus on the second method. The attackers provided a modified VNC tool to the targets under the pretense of evaluating their technical abilities for high-level jobs at notable aerospace and defense firms.
New Modular Malware: CookiePlus
In Kaspersky’s investigation, they found that the attackers used a newly introduced modular backdoor called CookiePlus. This tool is designed to evade detection and expand the hacker group’s influence once it’s on a targeted system.
Nuclear-Related Attack Details
In one instance, Lazarus Group sent the first malicious archive file to two different employees at the same nuclear-related organization, calling them “Host A” and “Host B.” About a month later, the attackers intensified their focus on Host A. The initial files likely arrived as ISO images or ZIP archives containing trojanized VNC applications known as “AmazonVNC.exe.” In some cases, a genuine UltraVNC file was paired with a harmful DLL to trigger a hidden backdoor called MISTPEN.
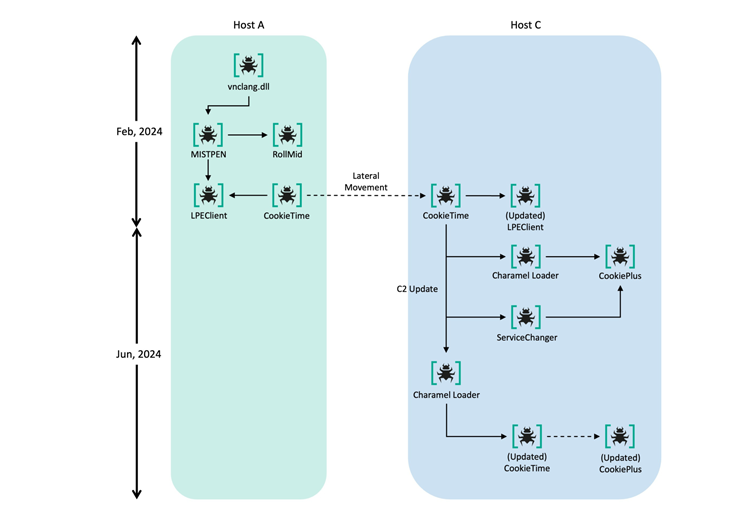
Lateral Movement and Additional Payloads
Further analysis showed that the attackers later moved from Host A to a different machine, referred to as “Host C.” There, between February and June 2024, they installed CookieTime once again and dropped various malicious tools, including:
- LPEClient: A tool to gather system details.
- CookiePlus: A new modular plugin-based malware.
- ServiceChanger: Malware that halts a legitimate service and then loads a fake DLL through side-loading.
- Charamel Loader: A loader that decrypts internal resources, including CookieTime, CookiePlus, and another tool named ForestTiger.
While both ServiceChanger and Charamel Loader can load CookiePlus, they do it differently. The first embeds the command-and-control (C2) details inside the DLL’s resources, while the second fetches them from an external file. CookiePlus got its name because, at first, it imitated a Notepad++ plugin called ComparePlus. Later studies linked it to another open-source project named DirectX-Wrappers.
Links to Past Campaigns
CookiePlus appears related to MISTPEN, as both once posed as Notepad++ plugins. Because of this, security experts think that CookiePlus might be an updated version or successor of MISTPEN. Throughout its history, Lazarus Group has built and used only a few modular malware frameworks, such as Mata and Gopuram Loader. The introduction of CookiePlus shows they continue to develop new malware to stay ahead of security measures.
Escalation in DPRK Crypto Theft
These findings come at a time when blockchain analysis company Chainalysis revealed that North Korean-linked hackers stole around $1.34 billion in cryptocurrency during 47 separate incidents in 2024. This is a sharp rise compared to $660.50 million in 2023. One example is the May 2024 breach at Japanese crypto exchange DMM Bitcoin, resulting in a $305 million loss. According to Chainalysis, it seems that North Korea’s crypto raids are becoming more frequent, with larger heists happening more often than before.