Mitel MiCollab Vulnerability Discovered
Introduction to the Vulnerability
Security researchers have discovered a dangerous flaw in Mitel MiCollab that can allow attackers to access sensitive files from vulnerable systems. This issue stems from a critical vulnerability, identified as CVE-2024-41713, which affects the NuPoint Unified Messaging (NPM) component of MiCollab. This bug, given a CVSS score of 9.8, allows for a path traversal attack due to improper input validation, making it possible for an attacker to read files on the server without proper authentication.
You might be interested in: Cyber Security Analyst: What They Do?
MiCollab is a communication platform that integrates various messaging tools like chat, voice, video, and SMS with Microsoft Teams and other apps. It also includes NPM, a voicemail system that allows users to listen to their messages remotely, including through Microsoft Outlook.
How the Vulnerability Works
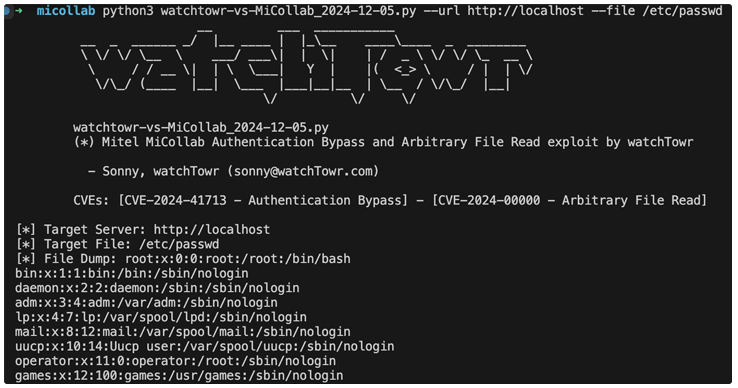
The vulnerability in question arises when an attacker sends malicious input in an HTTP request to the ReconcileWizard component. By using a specially crafted input like “..;/”, the attacker can navigate to the root directory of the server, potentially gaining access to sensitive files such as the system’s password file (e.g., /etc/passwd) without needing to log in.
This flaw can be combined with another yet-to-be-patched issue, an arbitrary file read bug that allows attackers to access sensitive information after logging into the system. If exploited together, these vulnerabilities could provide an attacker with unauthorized access to critical data.
Security Impact and Possible Consequences
If successfully exploited, this vulnerability could lead to unauthorized access to provisioning information and allow attackers to perform administrative actions on the MiCollab server. This can significantly compromise the system’s confidentiality, integrity, and availability.
Mitel acknowledged that the issue could be severe, with potential risks that affect the overall security of the MiCollab platform.
The Exploit Discovery
WatchTowr Labs, in their research, found CVE-2024-41713 while investigating another vulnerability, CVE-2024-35286, which was also related to the NPM component. The latter, a critical SQL injection flaw, was patched in MiCollab version 9.8 SP1 (9.8.1.5) released in May 2024.
Security researcher Sonny Macdonald, who was part of this investigation, emphasized that this case shows how sometimes full access to the source code isn’t necessary to find vulnerabilities. By leveraging detailed CVE descriptions and good research skills, vulnerabilities can still be uncovered.
How to Protect Against This Flaw
The CVE-2024-41713 vulnerability was fixed in MiCollab version 9.8 SP2 (9.8.2.12), which was released on October 9, 2024. This version also addresses another critical issue in the Audio, Web, and Video Conferencing (AWV) component, CVE-2024-47223, which was also identified as a severe vulnerability with a CVSS score of 9.4.
It’s recommended that all MiCollab users update to the latest version (9.8 SP2 or later) to avoid falling victim to these vulnerabilities.
Conclusion
The discovery of CVE-2024-41713 highlights the ongoing need for security vigilance and the importance of regular software updates. As attackers continue to target vulnerabilities, it’s crucial for organizations using Mitel MiCollab to patch these flaws promptly to protect sensitive data and maintain system integrity.
