New ‘Magic Packet’ Rootkit Hijacks Linux Servers
Security researchers have uncovered a highly sophisticated new malware for Linux servers, dubbed LinkPro, that can remain almost completely invisible until activated by a secret signal. This rootkit, discovered during an investigation of a compromised Amazon Web Services (AWS) environment, uses advanced modern Linux features to hide its presence and give attackers a secret backdoor into infected systems.
The attack is particularly sneaky because the malware lies dormant, showing no signs of activity until the hackers send a specific, specially crafted network request known as a “magic packet.” This technique makes detection incredibly difficult, allowing attackers to maintain long-term, hidden access to critical cloud infrastructure.
How the Attack Begins
The chain of infection, as detailed by cybersecurity firm Synacktiv, started with a common but critical security oversight: an exposed and outdated Jenkins server. The attackers exploited a known vulnerability to gain their initial foothold. From there, they deployed a malicious container from Docker Hub, a public repository for software images. This container, disguised as a legitimate application, was the Trojan horse that carried the malware onto the company’s servers.
Inside this malicious container were several tools designed to give the attackers full control. This included a program to set up a secret VPN and proxy connection, allowing the hacker to access the server from anywhere on the internet. It also contained a downloader that fetched the final malicious programs, including the LinkPro rootkit itself, from a remote storage location.
The Rootkit’s ‘Magic Trick’
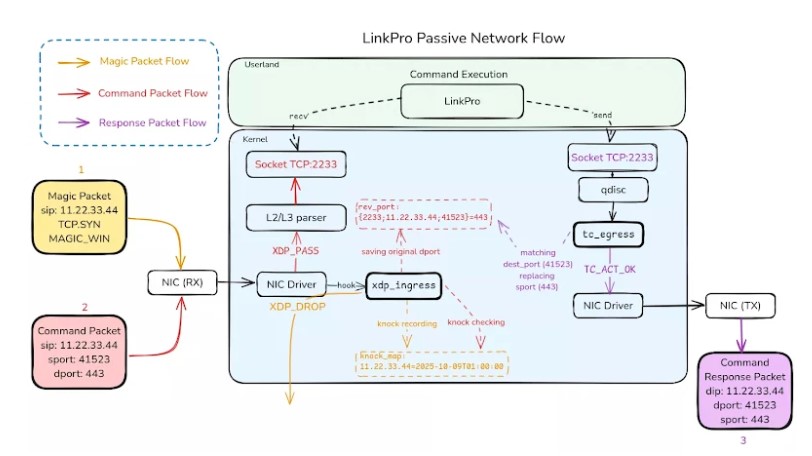
What makes LinkPro stand out is its clever use of a “magic packet.” The rootkit doesn’t constantly try to communicate with the attacker’s server, a behavior that security tools often look for. Instead, it operates in a passive mode, silently listening to all the network traffic hitting the server. It’s waiting for one very specific thing: a TCP packet with a window size set to the exact number 54321.
When this “magic packet” arrives, the rootkit springs to life. It registers the sender’s IP address and opens a secret one-hour window for the attacker to connect and issue commands. This method is incredibly effective for evading firewalls. The attacker can send the magic packet to any open port on the server. The rootkit then cleverly intercepts the follow-up traffic from the attacker and redirects it to its own hidden listening port, making it appear as if the communication is legitimate. This makes it extremely challenging for security teams to trace the malicious activity in their network logs.
A Master of Disguise
LinkPro is designed from the ground up to be invisible. Its primary method for hiding involves using a powerful, modern kernel technology called eBPF (extended Berkeley Packet Filter). By installing special eBPF programs directly into the core of the Linux operating system, the rootkit can intercept system calls. This allows it to lie to other programs; for example, if an administrator lists all running processes, LinkPro filters the results to remove any mention of itself. It also hides its own files and network connections, effectively cloaking itself from view.
The creators of LinkPro were thorough and even built in a backup plan. If the server’s configuration doesn’t allow for the eBPF hiding technique, the rootkit falls back to a more traditional method. It modifies a critical system file (/etc/ld.so.preload) to force all other programs to load a malicious library first. This library then hijacks basic functions, so when a tool like ls is used to list files, the library intercepts the request and scrubs any evidence of the rootkit before showing the results to the user. To complete its vanishing act, LinkPro cleans up after itself by removing the eBPF modules and restoring any modified files when it is shut down.
What the Hackers Can Do
Once the attackers use their magic packet to gain access, they have complete control over the compromised server. The rootkit allows them to execute any command, browse the entire file system, upload or download files, and even create a SOCKS5 proxy. This last capability is especially dangerous, as it allows the hackers to use the infected server as a jumping-off point to attack other machines within the same network, all while hiding their true location.
While the identity of the group behind LinkPro is still unknown, the nature of the attack suggests they are financially motivated. This new rootkit demonstrates a significant evolution in malware, showcasing how attackers are now weaponizing advanced system features like eBPF to build stealthier and more resilient backdoors.
