New Malware Campaign Uses Fake CAPTCHAs to Spread Lumma Stealer
Cybersecurity experts have discovered a new malware campaign that tricks users into installing the Lumma information stealer. The criminals behind this scheme are using fake CAPTCHA pages, which appear on compromised websites and prompt people to carry out specific steps that ultimately infect their systems.
You might be interested in: Former CIA Analyst Pleads Guilty to Leaking Classified Information
Global Impact Across Many Industries
According to researchers at Netskope Threat Labs, this attack wave has reached different parts of the world, including the United States, Argentina, Colombia, and the Philippines. A wide range of industries has been targeted, such as healthcare, banking, marketing, and especially telecommunications, where the highest number of victims has been observed.
How the Attack Works
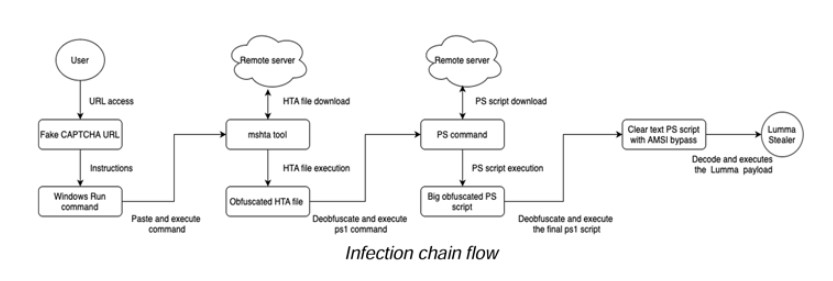
- Fake CAPTCHA: The victim visits a hacked website and encounters a phony CAPTCHA page asking them to copy and paste a command into the Windows Run box.
- Command Execution: This command uses
mshta.exe—a default Windows tool—to download and run an HTA file from a remote server. - Next-Stage Payload: Once launched, the HTA file tries to dodge Windows Antimalware Scan Interface (AMSI) and then starts a PowerShell command. This PowerShell command runs another script, which opens a second script that finally deploys the Lumma Stealer.
In earlier forms of this attack (sometimes called ClickFix), the attackers used a Base64-encoded PowerShell script to begin the infection. By making users manually copy the command, criminals avoid standard browser-based defenses.
Evasion Methods
The cybercriminals are taking steps to evade detection by using different payloads and delivery methods. Lumma, which is offered as Malware-as-a-Service (MaaS), can easily adapt to new techniques to get around security measures. Because users perform most steps themselves, it is harder for security tools to spot or block these attacks.
Fake Websites and Recent Activity
Research also shows that at least 1,000 fake sites—pretending to be services like Reddit and WeTransfer—have been used to spread Lumma. Users visiting these sites are pushed to download password-protected files. Inside, they find an AutoIT dropper called SelfAU3 Dropper, which installs the stealer. Earlier in 2023, a similar method was used with more than 1,300 domains faking AnyDesk to distribute another malware known as Vidar Stealer.
Rise of Advanced Phishing-as-a-Service
On top of that, Barracuda Networks has identified a new version of a Phishing-as-a-Service platform called Tycoon 2FA. This upgraded toolkit helps criminals send phishing emails from what look like real, possibly compromised, email accounts. It also keeps an eye out for signs of automated scanning and can block right-click menu options, making it harder for security systems to analyze or warn about the phishing pages.
Social Engineering Tactics with Gravatar
Experts have also noticed that attackers are abusing Gravatar—an online avatar service—to create fake profiles that mirror real services like AT&T, Comcast, and Proton Mail. By using these realistic-looking profiles, criminals increase their chances of fooling users into giving away their login details.
“By using Gravatar’s profile service, attackers can build fake profiles that closely copy the real services they’re pretending to be,” said Stephen Kowski, CTO of SlashNext Field. “These social engineering methods are surprisingly effective because victims see familiar logos and design, and trust them enough to enter their credentials.”
