New Security Risk Found in NVIDIA Container Toolkit Patch
A Serious Bug That Was Supposed to Be Fixed… Wasn’t
Cybersecurity experts have found that a recent fix for a major flaw in the NVIDIA Container Toolkit didn’t fully solve the problem. This bug, originally labeled CVE-2024-0132 and rated 9.0 on the CVSS scale, is a Time-of-Check to Time-of-Use (TOCTOU) issue. In short, it can allow attackers to break out of a container and access the host system—something containers are supposed to prevent.
You might be Interested in: Fortinet Pushes Urgent FortiSwitch Update
NVIDIA released a patch for this vulnerability back in September 2024, but new research from Trend Micro shows that the fix was incomplete. Even worse, they also uncovered a related problem that can cause performance issues and even shut down Docker services on Linux.
What the Bug Can Actually Do
The main issue here lies in how the NVIDIA toolkit handles mounting files when a container starts up. There’s a function called mount_files that doesn’t properly lock certain operations, leaving a small window where an attacker could interfere.
If an attacker already has access to a container, they could use this vulnerability to run commands on the host machine as root, the highest level of access. This could let them steal data, mess with files, or take over the system entirely.
This new weakness has been assigned a new ID: CVE-2025-23359, and it’s also rated 9.0. It’s basically a workaround for the original CVE-2024-0132 flaw, meaning the earlier patch didn’t go far enough. NVIDIA has addressed this new issue in version 1.17.4, but only if the feature allow-cuda-compat-libs-from-container is turned off.
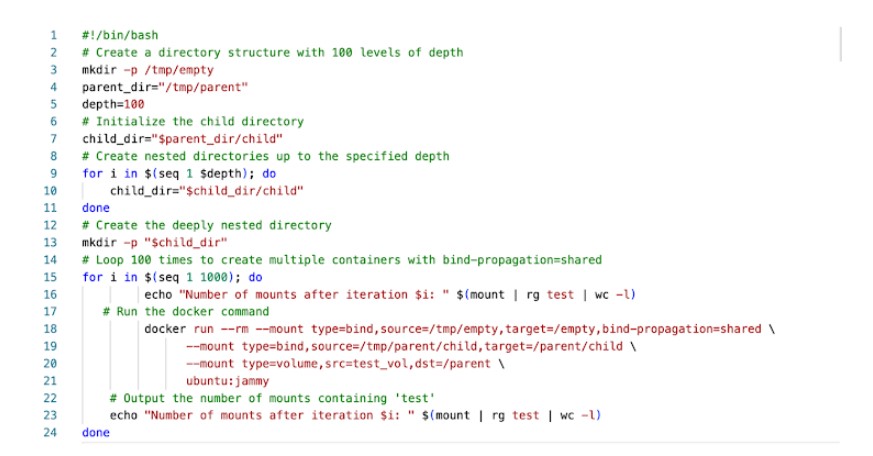
A Separate Issue That Slows Everything Down
During their research, Trend Micro also found something else: a performance glitch in Docker that could lead to a denial-of-service (DoS) problem.
Here’s what happens: if a container is created with lots of mounts (especially when using bind-propagation=shared), it builds up a long list of connections in the Linux mount table. When that container stops, the system doesn’t clean up those entries. Over time, this leads to the mount table getting too big and using up all the file descriptors on the system.
When that happens, Docker can’t start any new containers. Worse still, people might not even be able to connect to the server (even over SSH), causing big disruptions.
How to Stay Safe
To reduce the risk from both the security and performance problems, here are some tips:
-
Upgrade to version 1.17.4 of the NVIDIA Container Toolkit
-
Monitor the mount table for unexpected growth
-
Restrict who can access and use the Docker API
-
Review and tighten permissions on volume mounts and socket access
-
Audit your containers regularly to spot risky setups
