New Threat Exploits Windows UI Automation to Bypass Security
How Windows UI Automation Can Be Misused for Harmful Actions
A recent security discovery highlights how attackers can take advantage of Windows’ UI Automation (UIA) framework to carry out a variety of malicious actions without triggering alarms from endpoint detection and response (EDR) tools. This threat leverages the UIA framework, originally designed to assist users with disabilities and for automated testing, but it can be weaponized to silently execute commands, steal sensitive data, or redirect users to phishing sites.
You might be interested in: QR Codes and Email Assaults: Black Basta Evolves
Tomer Peled, a security researcher at Akamai, explained that this technique only requires a user to run a malicious program that uses UIA. Once triggered, it can run harmful operations such as reading and sending messages on platforms like Slack or WhatsApp. It can even manipulate UI elements remotely through the network.
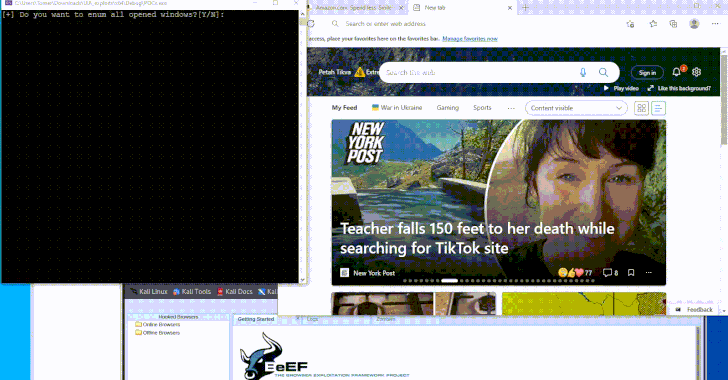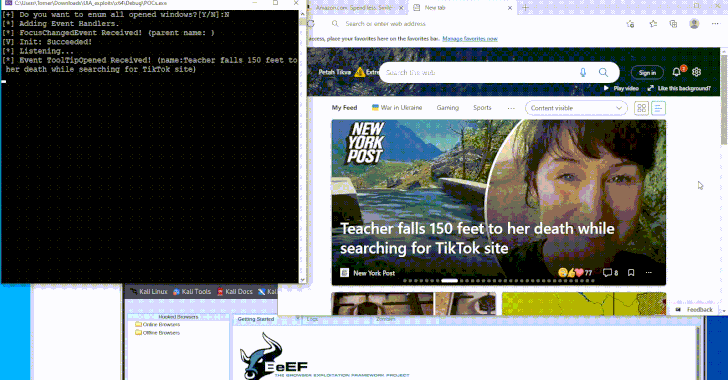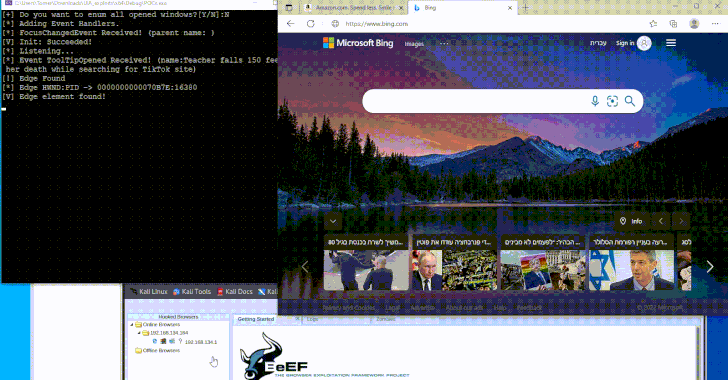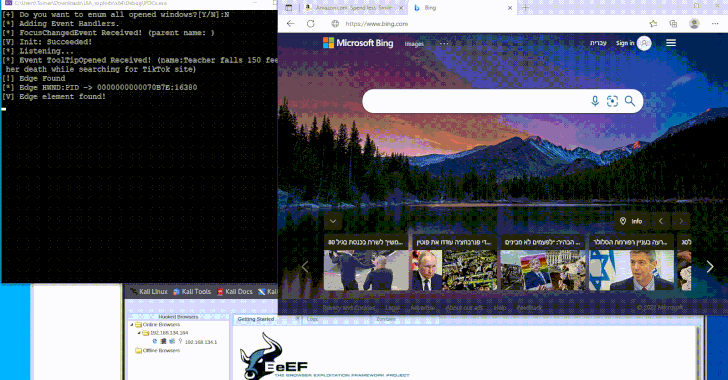
Windows UI Automation: Original Purpose and Its New Security Risks
UI Automation, first introduced in Windows XP as part of the Microsoft .NET Framework, was created to help users interact with UI elements using assistive technologies, like screen readers. It also serves to automate tasks in testing environments. However, in order to work with system UI elements or other applications running at higher privilege levels, UIA applications must be trusted by the operating system and given special access permissions.
For example, an application using UIA must set a specific flag in its manifest and be launched by an administrator. This gives it the ability to interact with other programs and system elements in ways that could be abused.
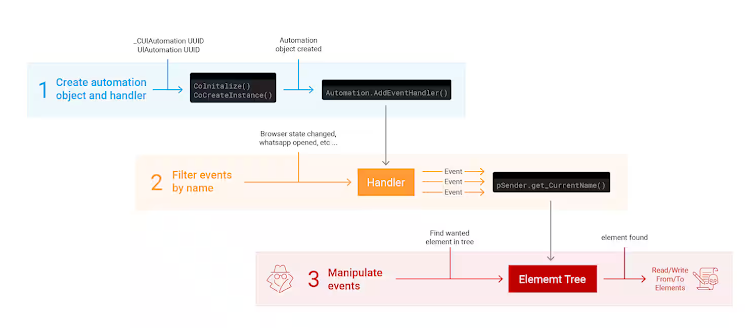
By using COM (Component Object Model) for inter-process communication, UIA allows programs to interact with the UI elements of other applications. Malicious actors can exploit this capability to monitor and modify what appears on the screen, even if the changes aren’t visible to the user.
Potential for Abuse in Everyday Applications
Akamai’s research reveals that attackers can exploit this UIA feature to read data entered on websites, such as payment details, and even control the browser by redirecting it to malicious sites. They can also send messages on messaging platforms like Slack or WhatsApp without the user being aware.
Peled explained that UIA can interact with not only the elements currently visible on the screen but also those that are cached in the background. This means attackers could potentially access hidden messages, change text boxes, or send messages, all without triggering any visible changes.
These vulnerabilities aren’t flaws in the system but rather features of UI Automation that were designed for legitimate purposes. Just as Android’s accessibility API has been abused by malware, UIA’s privileges can be misused by attackers to circumvent security tools, including Windows Defender, which might fail to detect these actions as malicious.
A New Lateral Movement Attack Vector: DCOM Exploits
Alongside the UIA threat, researchers have also uncovered a separate vulnerability involving the Distributed COM (DCOM) protocol. DCOM allows software components to communicate over a network, but attackers can exploit it to remotely write malicious payloads onto a target machine and create a backdoor.
Deep Instinct’s security team revealed how DCOM can be abused by writing custom Dynamic Link Libraries (DLLs) to a target machine, loading them into a service, and executing them remotely. This technique relies on the IMsiServer COM interface, which can be exploited to carry out lateral movement attacks.
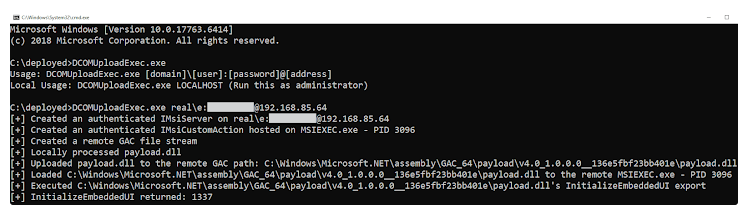
While this method is more noticeable and easier to detect, it highlights the need for better security practices. For instance, both the attacker and the victim’s devices must be on the same network domain for the attack to succeed.
Security experts stress the importance of updating defenses to counter these new attack vectors. These discoveries show that many unexpected DCOM objects could be exploited, and additional precautions are necessary to secure systems against lateral movement attacks.
