North Korean Hackers Using Fake Job Offers to Spread Malware
North Korean Hackers: How the Scam Works
A hacking group linked to North Korean Hackers, known as Lazarus, is running a new scam that uses fake job offers on LinkedIn. They’re targeting people in the cryptocurrency and travel industries, spreading malware that can infect computers running Windows, macOS, or Linux.
Cybersecurity experts at Bitdefender say the scam starts with a message on LinkedIn or other professional networks. The message offers a tempting job opportunity with perks like remote work, flexible hours, and a high salary.
Once someone shows interest, the scammers ask for a resume or even a link to their personal GitHub account. These requests might seem normal, but they’re actually used to gather personal information and make the scam seem more believable.
The Malware Attack
After getting the victim’s information, the scammers send a link to a GitHub or Bitbucket repository. The repository contains a fake project, often described as a decentralized exchange (DEX). The victim is asked to review the project and share their thoughts.
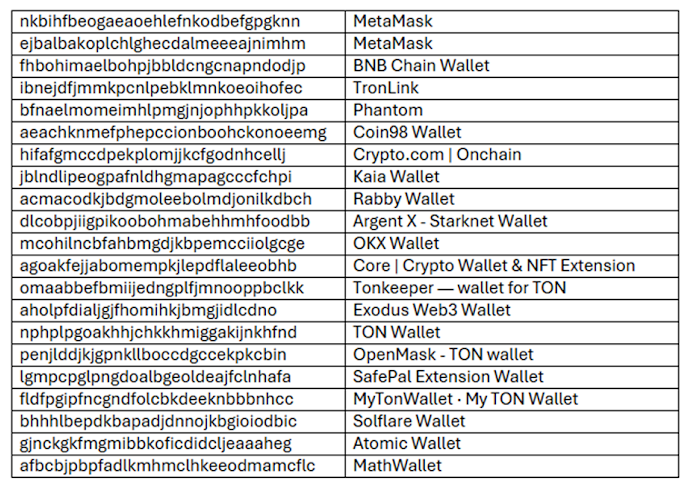
Hidden in the code is a malicious script that downloads a second-stage payload from a remote server. This payload is a JavaScript-based information stealer designed to steal data from cryptocurrency wallet extensions installed in the victim’s browser.
The malware also acts as a loader, downloading a Python-based backdoor. This backdoor can monitor clipboard activity, maintain remote access to the infected system, and install additional malware.
Connections to Known North Korean Hackers Attacks
Bitdefender notes that this scam shares similarities with a known hacking campaign called Contagious Interview (also called DeceptiveDevelopment or DEV#POPPER). This campaign is known for using a JavaScript stealer called BeaverTail and a Python implant called InvisibleFerret.
You might be interested in: DeepSeek’s Database Leak Raises Security Concerns
The Python malware is a .NET binary that can set up a TOR proxy to communicate with a command-and-control (C2) server. It also collects system information, logs keystrokes, and can even install a cryptocurrency miner on the victim’s computer.
A Complex Infection Chain
The attack is highly sophisticated, using multiple programming languages and technologies. For example:
- Multi-layered Python scripts that decode and execute themselves.
- A JavaScript stealer that collects browser data before downloading more malware.
- .NET-based tools that disable security software, set up TOR proxies, and launch crypto miners.
How North Korean Hackers Widespread Is This Scam?
Reports on LinkedIn and Reddit suggest this scam is affecting many people. The attackers sometimes change their methods slightly. For example, some victims are asked to clone a Web3 repository and run it locally as part of a fake interview process. Others are told to fix bugs intentionally added to the code.
One of the Bitbucket repositories used in the scam was named “miketoken_v2,” but it has since been removed from the platform.
Recent Developments
This news comes just after cybersecurity firm SentinelOne revealed that the Contagious Interview campaign is also being used to deliver another malware called FlexibleFerret.
Stay Safe Online
If you’re job hunting, especially in tech or cryptocurrency, be cautious about unsolicited job offers. Always verify the legitimacy of the recruiter and avoid downloading or running code from untrusted sources.
By staying alert, you can protect yourself from falling victim to these sophisticated scams.
