North Korean IT Workers Extort Western Firms
North Korean IT Workers, who have been known to secure jobs in Western companies under false identities, are stepping up their tactics. Previously focused on stealing intellectual property, they are now extorting their employers by demanding ransoms to prevent the release of stolen data. This new development highlights a shift towards financially motivated attacks.
You might be interested in: Hackers Exploit EDRSilencer to Evade Security
According to an analysis by Secureworks Counter Threat Unit (CTU), there have been several cases where fraudulent workers requested ransom payments from employers after gaining insider access. “This is a significant change from past schemes,” the report said. For instance, one case involved a contractor who stole proprietary data shortly after starting their job in mid-2024.
Connections to Known Threat Groups or North Korean IT Workers
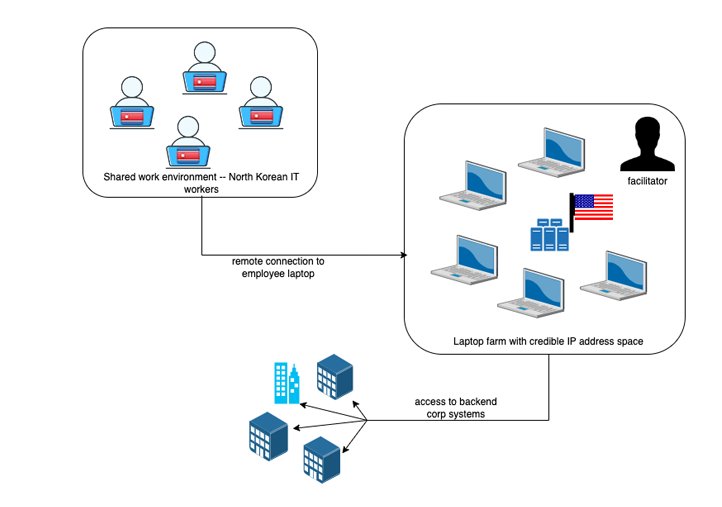
The CTU has linked this behavior to a group it tracks as Nickel Tapestry, also known as Famous Chollima or UNC5267. This group has been previously associated with North Korean cyber activities, but the addition of ransom demands marks a notable shift in their approach.
The fake IT worker operation appears to be part of a larger strategy to generate revenue for North Korea, a country facing heavy international sanctions. Many of these workers operate from countries like China and Russia, where they pose as independent contractors seeking work opportunities. In some cases, they even use stolen identities of U.S. citizens to secure these positions.
Strategies to Avoid Detection
To avoid suspicion, these fraudulent workers often request changes to the delivery addresses of company-issued laptops, rerouting them to intermediaries. These middlemen, often based in other countries, install software that allows North Korean IT Workers to remotely control the devices. There have been instances where workers have asked to use their own personal computers, bypassing the need for corporate laptops and making it harder to trace their activities.
“This tactic aligns with Nickel Tapestry’s method of avoiding corporate laptops, which reduces the need for local facilitators and limits access to forensic evidence,” Secureworks noted. By using personal laptops, the contractors can remotely access the company network without drawing attention.
Extortion Tactics on the Rise
In one reported case, a company fired a contractor for poor performance, only to receive extortion emails shortly afterward. The emails included ZIP files containing proof of stolen data, signaling a more aggressive and evolved approach from these threat actors.
Rafe Pilling, Director of Threat Intelligence at Secureworks CTU, stated, “This shift is a game-changer. They are no longer just looking for regular paychecks; they are going after bigger payouts by stealing data and using extortion tactics from within the company.”
How Companies Can Protect Themselves
To combat this rising threat, companies need to be extra cautious during the hiring process. Steps like thorough identity checks, in-person or video interviews, and verifying delivery addresses for company equipment are essential. Businesses should also monitor attempts to use unauthorized remote access tools to connect to their networks.
“This escalation shows how carefully planned these schemes are,” added Secureworks CTU. The group has observed workers trying to avoid enabling video during interviews and exhibiting unusual financial behavior, as highlighted in an FBI alert.
Conclusion: A Dangerous Evolution in Cyber Tactics
The rise of ransom demands from North Korean IT workers marks a significant change from their previous strategies. While their methods of securing employment under fake identities remain consistent, the shift towards extortion demonstrates a more aggressive and financially driven approach. Organizations must remain vigilant, taking proactive steps to identify and prevent these threats before they can cause harm.
