Remote Code Execution Vulnerability Discovered in Commvault Command Center
Unauthenticated Attackers Can Run Malicious Code
A serious security issue has been found in Commvault Command Center, allowing hackers to take control of affected systems without needing a password. Tracked as CVE-2025-34028, this flaw has been rated 9.0 out of 10 in severity.
You might be interested in: Google Cloud and Microsoft Azure Vulnerabilities Patched
Commvault warned users in an April 17, 2025, advisory that attackers could exploit this flaw to run any code they want, potentially giving them full access to the system.
Which Versions Are Affected?
The bug impacts Commvault Command Center 11.38 Innovation Release, specifically versions 11.38.0 through 11.38.19. The company has fixed the issue in these updated versions:
-
11.38.20
-
11.38.25
How the Attack Works
Security researcher Sonny Macdonald from watchTowr Labs discovered the flaw on April 7, 2025. The problem lies in a feature called “deployWebpackage.do,” which doesn’t properly check where it gets files from. This lets hackers trick the system into downloading a malicious ZIP file from an external server.
Here’s how the attack happens step by step:
-
The attacker sends a request to /commandcenter/deployWebpackage.do, forcing the system to download a harmful ZIP file.
-
The system unpacks the ZIP file into a temporary folder.
-
The attacker then moves the malicious file into a critical server directory.
-
Finally, they run the harmful code by accessing the file through the server.
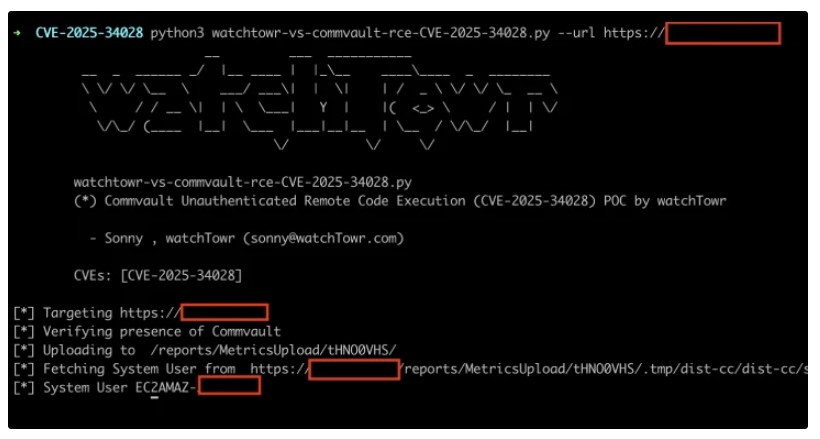
How to Check if You’re at Risk
watchTowr Labs has released a free tool to help organizations check if their systems are vulnerable. Since similar flaws in backup software (like Veeam and NAKIVO) have been actively exploited, users should update immediately to avoid attacks.
If you’re using an affected version, upgrade to the latest release as soon as possible to stay protected.