The Rise of Phishing as a Service
Over the past year, more than 140,000 phishing websites have been linked to a platform called Sniper Dz, which offers phishing as a service (PhaaS). This service allows cybercriminals to easily set up and execute phishing attacks, stealing credentials from unsuspecting users.
You might be interested in: Remote Hacks Possible with Kia License Plates
According to researchers from Palo Alto Networks Unit 42, Shehroze Farooqi, Howard Tong, and Alex Starov, Sniper Dz provides users with a web-based admin panel that includes a variety of ready-made phishing pages.
How Does Sniper Dz Work?
Phishers using Sniper Dz can either host their phishing pages directly on the platform’s servers or download the templates to use on their own. Since these services are free, they have become quite popular among fraudsters. However, it’s not just the users who benefit—Sniper Dz operators also receive the stolen credentials, leading to what Microsoft calls “double theft.”
The platform has made phishing much more accessible, even for people with limited technical knowledge, allowing them to launch large-scale phishing attacks without much effort.
Phishing Kits on Telegram
One way to obtain phishing kits is through Telegram, where specific groups and channels provide access to all aspects of the attack process. This includes everything from hosting services to delivering phishing emails. Sniper Dz is part of this ecosystem, operating a Telegram channel with over 7,000 members as of October 1, 2024. The channel was initially created in May 2020.
Following the release of the Unit 42 report, the operators of Sniper Dz activated an auto-delete feature on their Telegram channel, which erases all posts after one month. While older messages are still available, this move appears to be an attempt to cover their tracks.
Sniper Dz’s Infrastructure
Sniper Dz’s platform is easily accessible over the regular web (clearnet). Users are required to create an account to access scam tools and phishing templates. These templates are designed to mimic popular online services like Facebook, Instagram, PayPal, Netflix, and more, and are available in multiple languages.
Tutorials have even been found on platforms like YouTube, guiding users through the steps to set up fake landing pages for games like PUBG and Free Fire on legitimate platforms like Google Blogger.
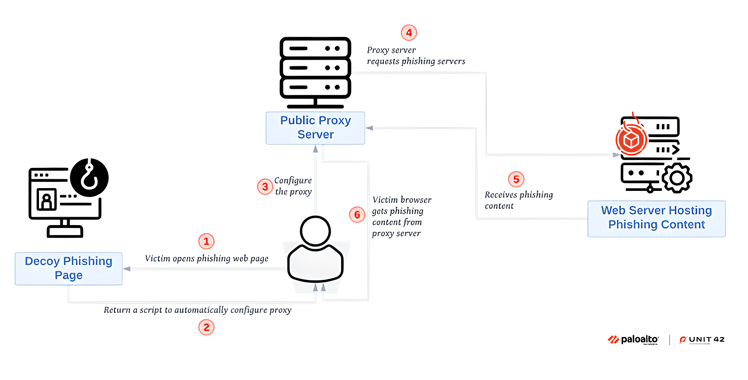
Concealing Phishing Activity
Sniper Dz offers an additional service where phishing pages are hosted on its servers. These pages are then hidden behind a legitimate proxy server, like proxymesh.com, to make them harder to detect. This proxy ensures that a victim’s browser or a security tool sees only the proxy server, not the phishing server itself.
Alternatively, users can download phishing page templates in HTML format to host on their own servers. Sniper Dz even provides tools to convert these templates for use on Blogger, making it easier to deploy phishing pages on Blogspot domains.
Rise in Phishing Attacks
Starting in July 2024, Unit 42 observed a surge in phishing activity linked to Sniper Dz, particularly targeting U.S.-based users. The stolen credentials are collected and displayed on an admin panel accessible through the clearnet, further expanding Sniper Dz’s operations.
Other Related Attacks
In addition to Sniper Dz, other cybercriminal activities are also gaining attention. Cisco Talos recently revealed how attackers are exploiting forms on websites that connect to backend SMTP servers. These forms, often lacking proper input validation, allow cybercriminals to bypass spam filters and send phishing emails.
Spammers also take advantage of web forms to insert harmful links and text into email confirmation messages. These emails, sent back to users upon registration, often contain phishing links due to inadequate sanitization of form inputs.
Fileless Malware Campaigns
Another recent threat is a phishing campaign exploiting a vulnerability (CVE-2017-0199) in Microsoft Office. This attack delivers a fileless version of Remcos RAT (Remote Access Trojan) through a malicious Excel file. When opened, the file triggers a series of commands that inject the malware into a legitimate Windows process, making it difficult to detect.
Conclusion
As phishing-as-a-service platforms like Sniper Dz become more prevalent, cybercriminals continue to find new ways to bypass security measures and steal sensitive information. These platforms lower the entry barriers for aspiring hackers, making phishing more accessible and widespread. Keeping up with these evolving threats will require continued vigilance and updated security measures to protect against these large-scale phishing campaigns.
