This Black Basta Ransomware Locks Your Files and Steals Millions
A massive leak of internal chat logs from the notorious ransomware group Black Basta has exposed their operations, internal conflicts, and tactics. The logs, spanning over a year, were published online, offering a rare glimpse into the workings of one of the most dangerous cybercriminal groups.
You might be interested in: RansomHub Leads Ransomware Attacks in 2024
The Leak and Its Origins
The leaked chats, written in Russian, took place on the Matrix messaging platform between September 2023 and September 2024. On February 11, 2025, a user named ExploitWhispers released the data, claiming they did so because Black Basta had been targeting Russian banks. The identity of the leaker remains unknown.
Black Basta first gained attention in April 2022, using QakBot (also known as QBot) to deliver ransomware. By May 2024, the U.S. government reported that the group had attacked over 500 organizations, including critical infrastructure, across North America, Europe, and Australia.
Profits and Internal Struggles
According to cybersecurity firms Elliptic and Corvus Insurance, Black Basta made at least $107 million in Bitcoin ransom payments from more than 90 victims by the end of 2023. However, the group has faced significant internal conflicts.
Swiss cybersecurity company PRODAFT revealed that Black Basta, also tracked as Vengeful Mantis, has been largely inactive since early 2025 due to infighting. Some members reportedly scammed victims by taking ransom payments without providing decryption tools.
Key members of the group have reportedly left to join other ransomware operations, such as CACTUS (also known as Nurturing Mantis) and Akira.
Key Figures in the Leaked Chats
The leaked chats, which include nearly 200,000 messages, highlight several important figures within Black Basta:
- Lapa: A main administrator handling group tasks.
- Cortes: Linked to the QakBot group, which tried to distance itself after Black Basta targeted Russian banks.
- YY: Another administrator focused on support tasks.
- Trump: An alias for Oleg Nefedov, the group’s leader, who also goes by GG and AA.
- Bio: A former associate of Trump in the now-defunct Conti ransomware group.
Shockingly, one of Black Basta’s affiliates is believed to be just 17 years old.
Tactics and Techniques
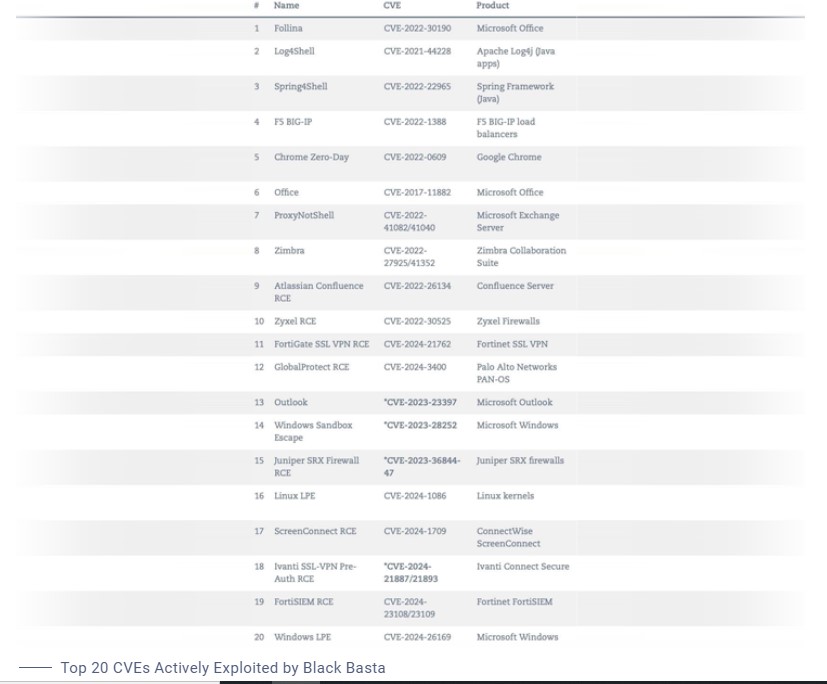
Black Basta has recently started using social engineering in their attacks, inspired by the success of another group, Scattered Spider. They exploit known vulnerabilities, weak security settings, and misconfigurations to gain access to target networks. Common targets include poorly secured SMB setups, exposed RDP servers, and systems with weak passwords.
The group frequently changes their ransomware payloads, file extensions, and ransom notes, leading to them being identified under multiple names, such as Cring, Crypt3r, Phantom, and Strike.
Connections to Other Threats
The leaked chats also mention ties to another group known as Ghost, which has been active since early 2021. Ghost targets outdated software and firmware in internet-facing systems, exploiting vulnerabilities in Adobe ColdFusion, Fortinet FortiOS, and Microsoft Exchange Server.
After gaining access, Ghost deploys web shells to install tools like Cobalt Strike, Mimikatz, and BadPotato for stealing credentials and escalating privileges. If their attempts to move laterally within a network fail, they often abandon the attack.
Conclusion
The leaked Black Basta chats provide an unprecedented look into the inner workings of a major ransomware group. From internal conflicts to evolving tactics, the revelations highlight the challenges of combating cybercrime. As these groups continue to adapt, cybersecurity efforts must remain vigilant to stay ahead of the threats.
