Tunneling Protocols Found to Have Security Flaws
Recent research has uncovered significant security weaknesses in various tunneling protocols, which could open the door for attackers to execute a range of dangerous cyberattacks. The study, conducted by Top10VPN and Professor Mathy Vanhoef from KU Leuven, highlights a serious issue: internet hosts that accept tunneling packets without verifying the sender’s identity are at risk of being hijacked for malicious activities.
You might be interested in: Fake Google Ads Campaign Steals Account Credentials
This vulnerability affects over 4.2 million devices globally, including VPN servers, CDN nodes, home routers, mobile network gateways, and core internet routers. Countries most impacted by these flaws include the United States, Brazil, France, Japan, and China.
If attackers exploit these vulnerabilities, they could launch denial-of-service (DoS) attacks or misuse the affected systems as one-way proxies, making the problem even more dangerous. CERT/CC has issued a warning, stressing that attackers can spoof source IP addresses, gain unauthorized access to private networks, or use vulnerable systems in distributed denial-of-service (DDoS) attacks.
The Root Cause: Lack of Security in Tunneling Protocols
Many popular tunneling protocols, such as GRE, GRE6, and various IPv6-in-IPv4/IPv4-in-IPv6 formats, lack proper authentication and encryption features. Without secure protocols like IPsec in place, these systems are left exposed to malicious actors.
This security gap allows attackers to inject harmful traffic into the network, bypassing security measures and causing significant harm. This is a variant of a vulnerability that was initially discovered in 2020 (CVE-2020-10136).
The specific CVEs related to the affected tunneling protocols are as follows:
- GRE and GRE6: CVE-2024-7595, CVE-2024-7596
- IPv4-in-IPv6: CVE-2025-23018
- IPv6-in-IPv4: CVE-2025-23019
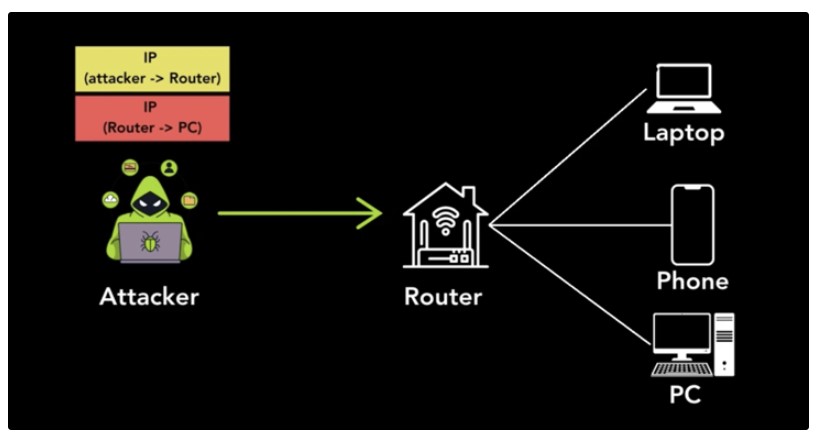
As Simon Migliano from Top10VPN explains, an attacker only needs to send a packet using one of these vulnerable protocols, with two IP headers—one outer and one inner. When this packet reaches the vulnerable host, the system strips the outer header, leaving the attacker’s malicious packet to reach its intended target without raising alarms.
Because the source IP in the inner header matches the vulnerable system’s IP, network filters may overlook the packet, allowing the attack to succeed undetected.
How to Protect Against These Attacks
To defend against these types of attacks, experts recommend using stronger security protocols such as IPsec or WireGuard for encryption and authentication. It’s also crucial to only accept tunneling packets from trusted sources.
Additional protective measures include:
- Implementing traffic filtering on routers and middleboxes
- Using Deep Packet Inspection (DPI) to identify malicious traffic
- Blocking all unencrypted tunneling packets at the network level
By taking these precautions, network administrators can reduce the risk of attacks and better protect their systems from exploitation.
The potential damage from these types of attacks can include network congestion, service outages, and even device crashes due to overload. Attackers may also gain access to private data or intercept communications, leading to further security risks like man-in-the-middle attacks.
Conclusion
The vulnerabilities found in tunneling protocols pose a serious threat to internet infrastructure and users worldwide. By adopting stronger security measures, such as IPsec and WireGuard, and employing robust traffic filtering techniques, organizations can protect their networks from exploitation and minimize the impact of these attacks.
