VSCode Malware and Fake Developer Tools
Harmful VSCode Extensions Spread Early-Stage Ransomware
Researchers recently discovered two dangerous extensions in the VSCode Marketplace. Named “ahban.shiba” and “ahban.cychelloworld,” these add-ons were designed to launch a piece of ransomware that is still in its testing phase. The marketplace team has already removed these extensions. According to ReversingLabs, both add-ons use code that triggers a PowerShell command to download and run a script from a remote server.
You might be interested in: CSS exploits in emails are tracking your actions and data.
At this early stage, the ransomware only encrypts files in a folder called “testShiba” on the victim’s Windows desktop. Once the files are locked, a message appears asking for 1 ShibaCoin to be sent to a ShibaWallet to unlock them. However, no additional payment details are provided, suggesting that the malware is still under development.
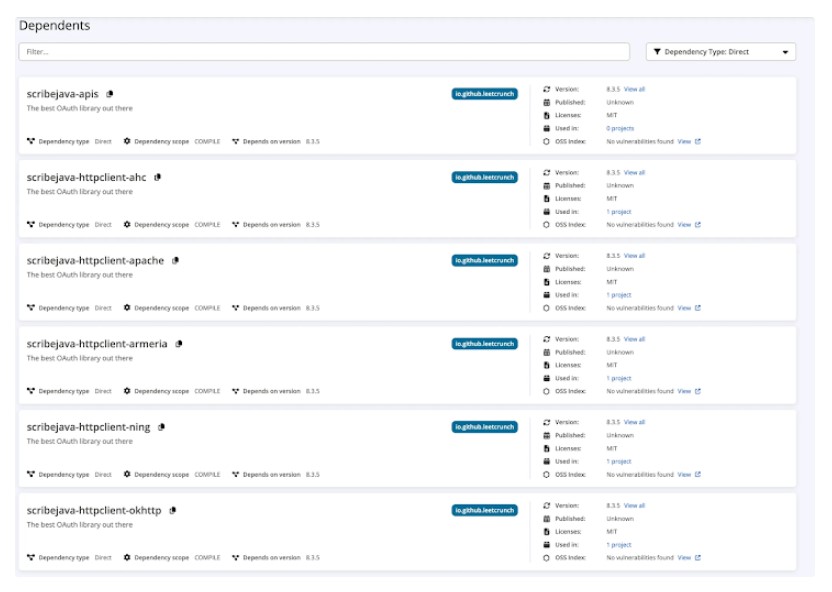
Fake Maven Package Tricks Developers with Typosquatting
In another case, a report from Socket uncovered a fraudulent Maven package that pretends to be the scribejava-core OAuth library. Uploaded to Maven Central on January 25, 2024, this package secretly steals OAuth credentials every month on the fifteenth day. The attackers used typosquatting—choosing a name very similar to the real library—to fool developers into adding it to their projects. Security researcher Kush Pandya pointed out that this fake package is linked to six other packages. All of these mimic genuine packages by using a misleading groupId (io.github.leetcrunch) instead of the correct one (com.github.scribejava), a tactic meant to boost their credibility and increase the chance of adoption by unsuspecting developers.