WordPress Plugin Gives Attackers Full Control
Fake Plugin Gives Attackers Full Control of Infected Websites
Security experts have uncovered a dangerous new malware campaign targeting WordPress plugins. Hackers are tricking site owners by hiding malicious code inside what appears to be a security plugin.
How the Fake Plugin Works
The malware, which first appeared in early 2025, pretends to be a helpful security tool with names like:
-
WP-antymalwary-bot.php
-
wp-performance-booster.php
-
addons.php
Once installed, this fake plugin:
-
Gives hackers admin access to the website
-
Hides itself from the WordPress dashboard
-
Can run harmful code remotely
-
Spreads infection to other website files
-
Shows unwanted ads by injecting malicious JavaScript
How Hackers Keep the Malware Active
Even if website owners remove the plugin, hackers have added a sneaky backup plan. A corrupted wp-cron.php file automatically reinstalls the malware the next time someone visits the site.
Security analysts found Russian-language notes in the code, suggesting the hackers may be Russian-speaking. However, it’s still unclear exactly how websites are getting infected in the first place.
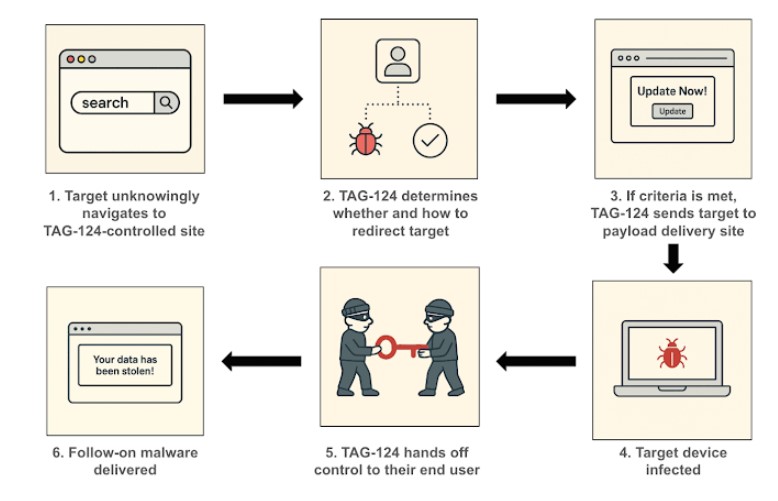
Other Recent Website Threats
Fake Payment Forms Steal Credit Card Info
A separate scam uses a fake fonts website (italicfonts[.]org) to show fake payment pages during checkout. When users enter their details, the information gets sent directly to hackers.
Clever Credit Card Scam Targeting Online Stores
Another attack focuses on Magento online stores. Hackers use what looks like a GIF image file (but is actually harmful PHP code) to:
-
Steal credit card numbers
-
Capture login details
-
Take browser cookies
-
Collect other private information
Hackers Hijack Websites to Show Their Own Ads
At least 17 WordPress sites were found running unauthorized Google AdSense ads. Hackers insert their own ad code to:
-
Make money from clicks and views
-
Potentially steal ad revenue from legitimate site owners
Fake CAPTCHA Tests Install Spyware
Some hacked websites show fake security checks (CAPTCHAs) that actually install hidden spyware. This malware can:
-
Gather system information
-
Give hackers remote access
-
Route malicious traffic through proxy servers
How to Protect Your Website
Website owners should:
-
Only install plugins from trusted sources
-
Regularly update WordPress and all plugins
-
Use strong security plugins
-
Monitor for suspicious activity
-
Check for unexpected ads or changes to files
Security experts warn that these attacks are becoming more sophisticated, making regular security checks essential for all website owners.
