Your Router Might Be Infected by Ballista Botnet
Overview
A new botnet, known as Ballista, is now attacking TP-Link Archer routers that haven’t been updated. According to researchers at Cato CTRL, the botnet takes advantage of a serious flaw (CVE-2023-1389) in these devices. This weakness lets hackers send commands to the router remotely, putting it at risk of full takeover.
You might be interested in: This LightSpy Malware Steals Your Social Media Info
How the Attack Works
The security gap was first seen in action back in April 2023. Early attacks used the flaw to load Mirai malware, and later, other malware types like Condi and AndroxGh0st followed. The Cato CTRL team spotted Ballista on January 10, 2025, and the latest attempt was logged on February 17.
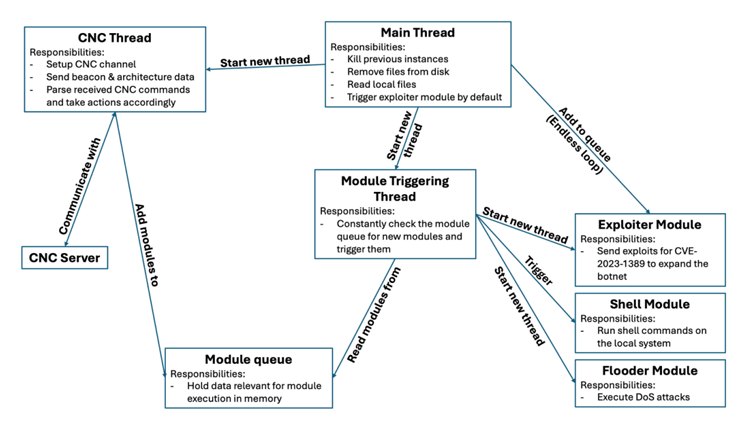
The attack begins with a small script named dropbpb.sh. This script downloads and runs the main program on different systems (including mips, mipsel, armv5l, armv7l, and x86_64). Once it’s active, the malware opens a secure channel on port 82. This channel lets the attackers run shell commands that can take over the device, launch denial-of-service attacks, or even read sensitive files.
Attack Capabilities
The infected routers can understand several commands:
- flooder: Triggers a flood attack.
- exploiter: Uses the vulnerability (CVE-2023-1389).
- start: Activates the exploiter module.
- close: Stops the module.
- shell: Runs Linux commands on the router.
- killall: Stops the running service.
The malware can also end any older copies of itself and erase traces of its activity. It uses the flaw to try and infect other routers automatically.
Indicators and Spread
The command channel was set up with an IP address (2.237.57[.]70) that, along with some Italian language clues in the code, hints at an Italian source. However, this IP address is no longer active, and a newer version of the dropper now uses TOR network domains.
A search on the Censys platform found more than 6,000 devices infected by Ballista. Most of these devices are located in Brazil, Poland, the United Kingdom, Bulgaria, and Turkey. The botnet has also been seen attacking organizations in manufacturing, healthcare, services, and technology sectors in the United States, Australia, China, and Mexico.
Conclusion
Although Ballista shares some traits with other botnets, it is distinct from well-known ones like Mirai and Mozi. Its evolving methods and wide spread make it a serious concern for anyone using vulnerable TP-Link Archer routers.