Protect with Passion®
From mitigating the risk of cyber-attacks to achieving compliance with industry regulations,
we assess, implement, and manage cybersecurity for the growing enterprise.
Trusted allies for your cyber security
Here at Rhyno, we secure your business operations, protect your critical data, and empower your team with cybersecurity awareness. We believe in forging long-lasting partnerships based on trust, transparency, and growth.
Services and Solutions
Guarding Today, Safeguarding Tomorrow: Your Future-Proof Security Ally
Managed Detection & Response
24/7 protection to defend against cyber threats. Leveraging cutting-edge technology and around-the-clock monitoring, we provide relentless security to keep your operations safe at all times.
Learn MoreSecure Enterprise Cloud Hosting
Fully-managed, secure hosting solutions. Our enterprise cloud services are designed to give you peace of mind, knowing your digital assets are in safe hands.
Learn MoreCybersecurity Awareness Training
We empower your team to build a strong security culture. Our comprehensive cybersecurity training ensures your employees become your first line of defense.
Learn MoreSecurity Audits & Penetration Testing
Understand your cybersecurity posture and vulnerabilities. Our thorough security audits and penetration testing services expose potential weak points before they can be exploited.
Learn MoreRisk Management & GRC
Benefit from top-tier consulting and independent advice. Our experts guide you through Governance, Risk Management, and Compliance (GRC) processes to bolster your cybersecurity.
Learn MoreEmergency Response & Forensics
We specialize in emergency response, digital forensics, and ransom negotiation ensuring thorough coverage for cyber breach scenarios.
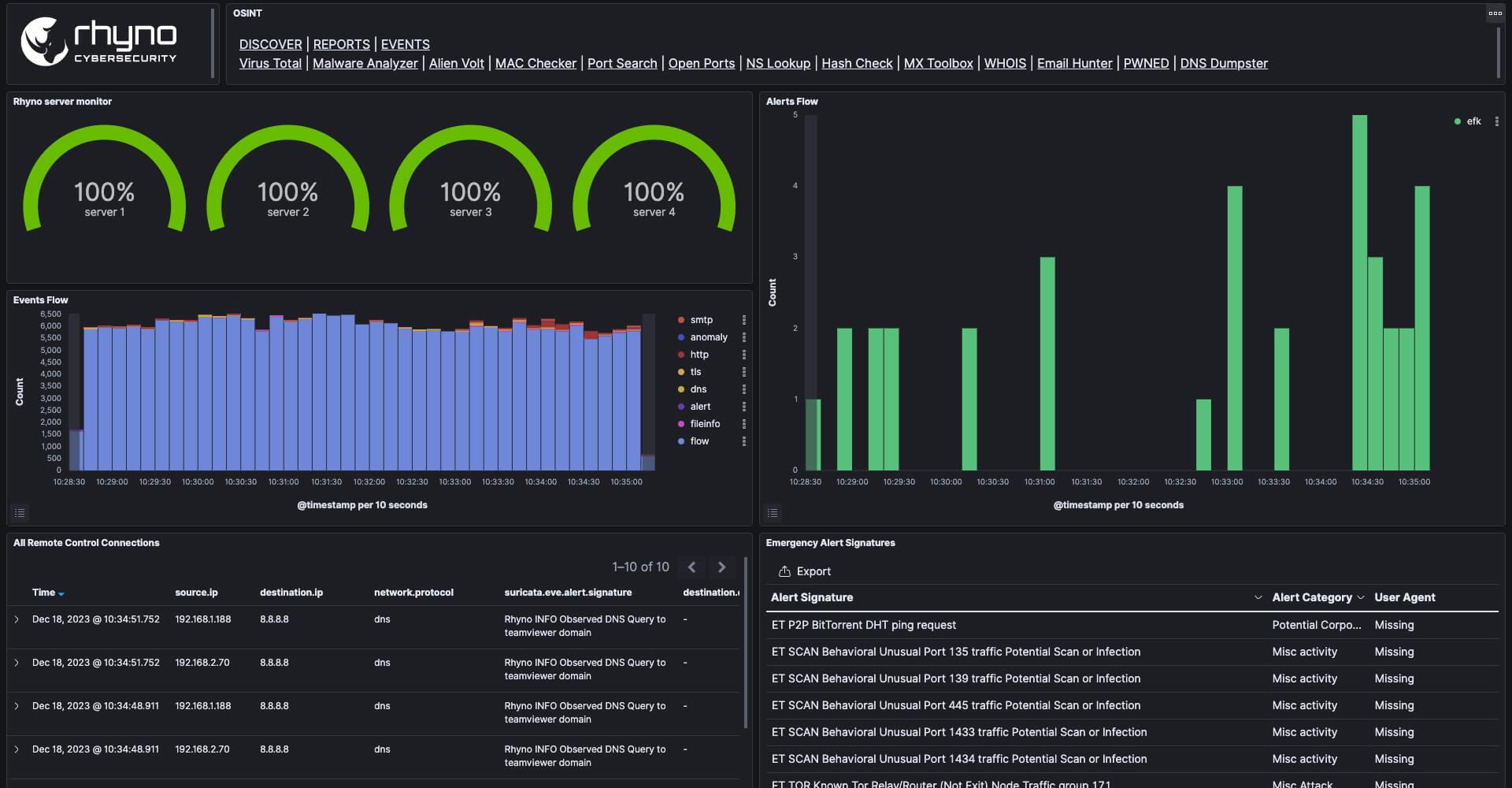
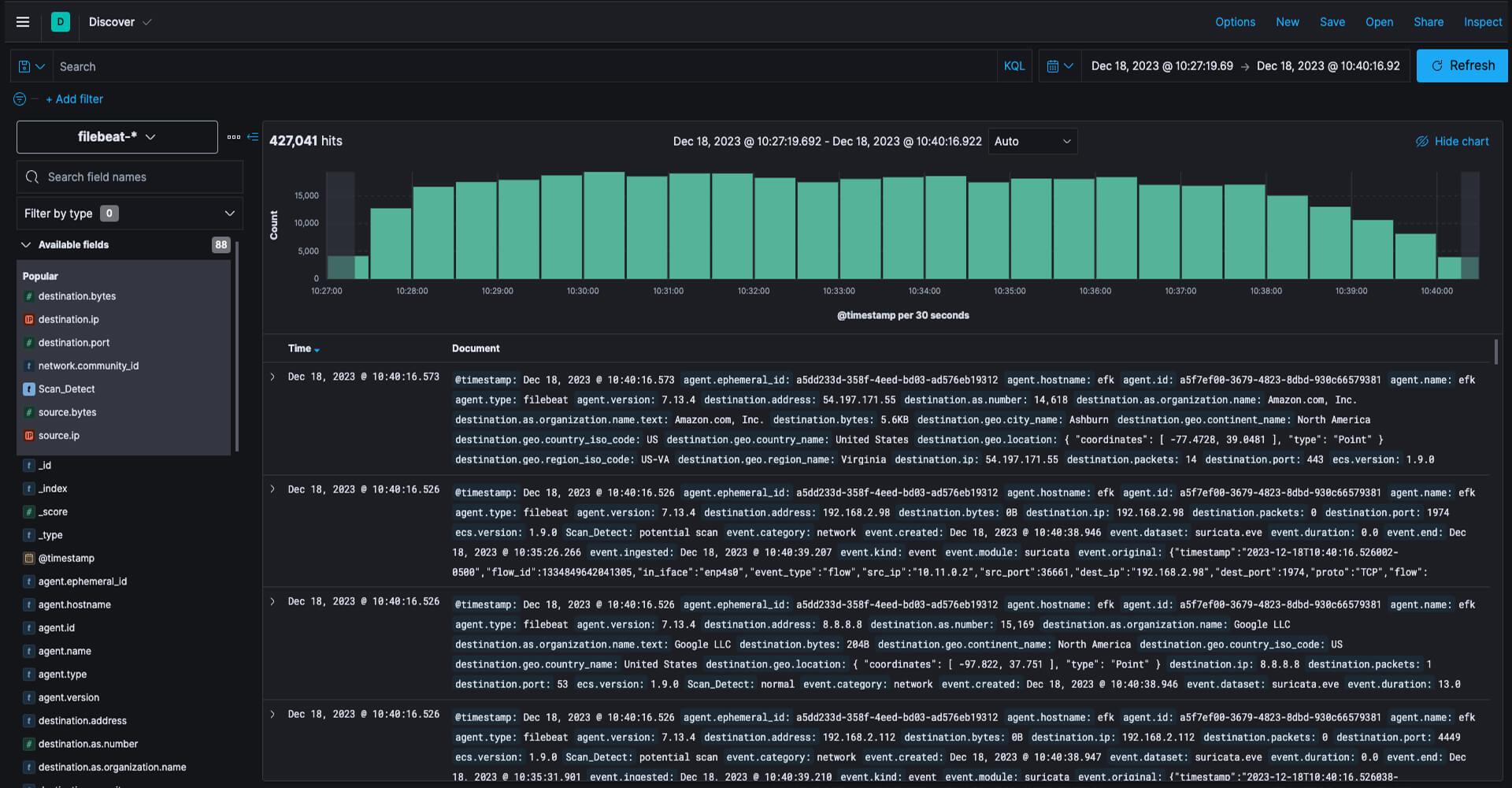
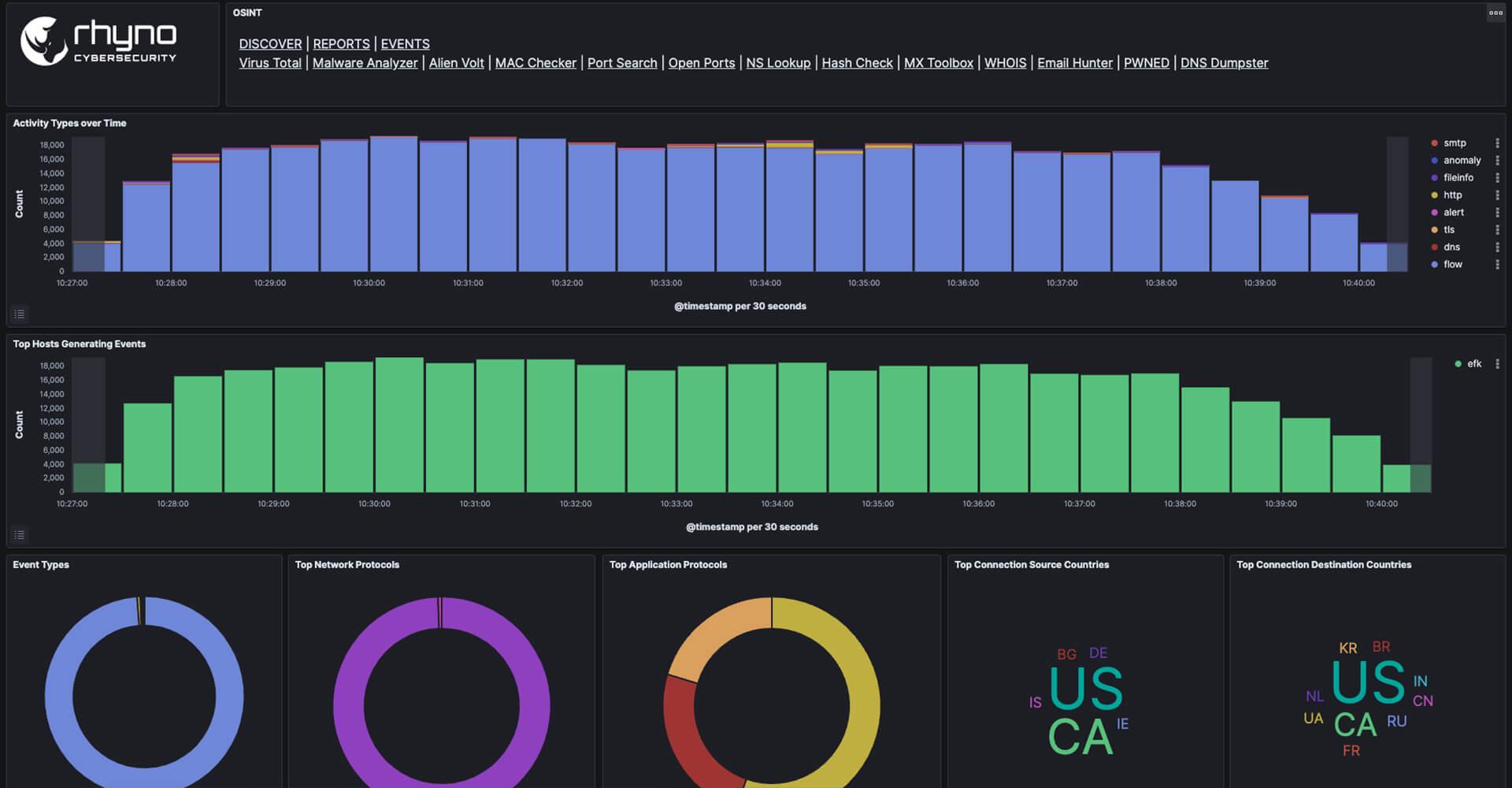
Learn More24/7 Threat Detection & Response Across the Enterprise
Expand your defenses using a single managed platform that addresses threats across various attack surfaces.
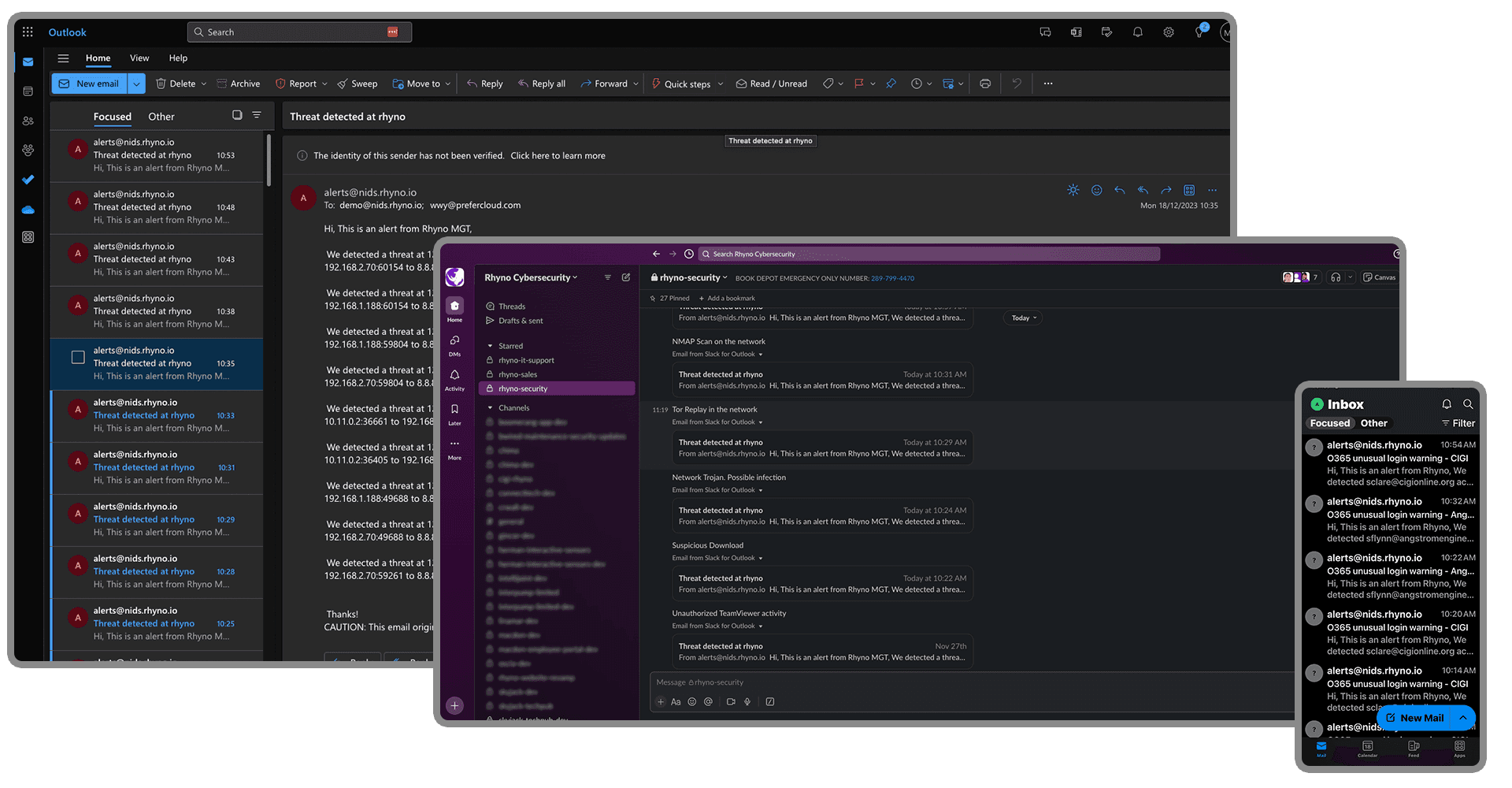
Prioritized Alert Management
For efficient cyber threat response
24/7 Continuous Threat Hunting
Constant monitoring and analysis of data
Network Security Optimization
Secure, operational and accessible
Tools and integrations
For complete 360 visibility
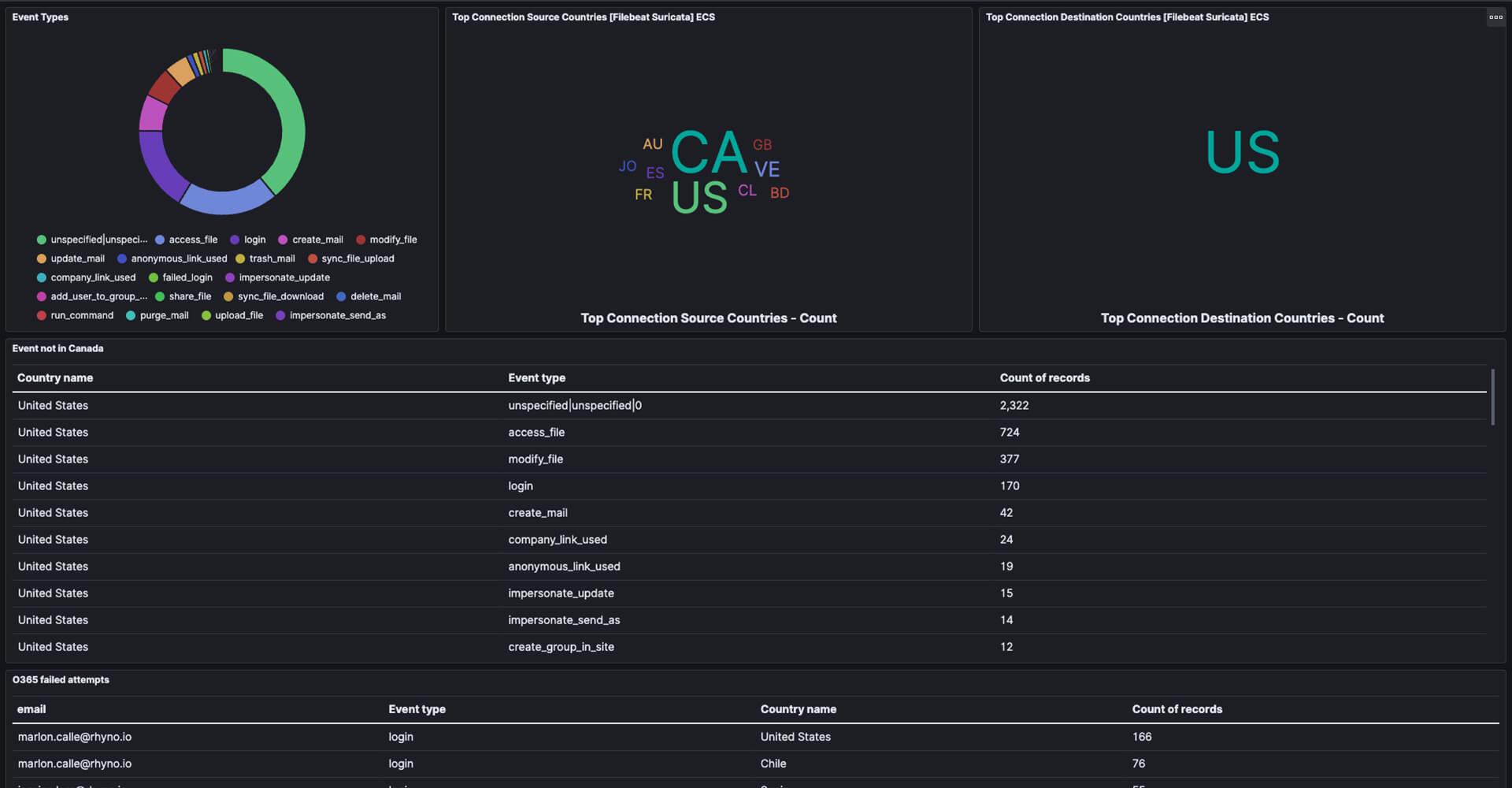
Alert Management Integrations
Get alerts where you need them
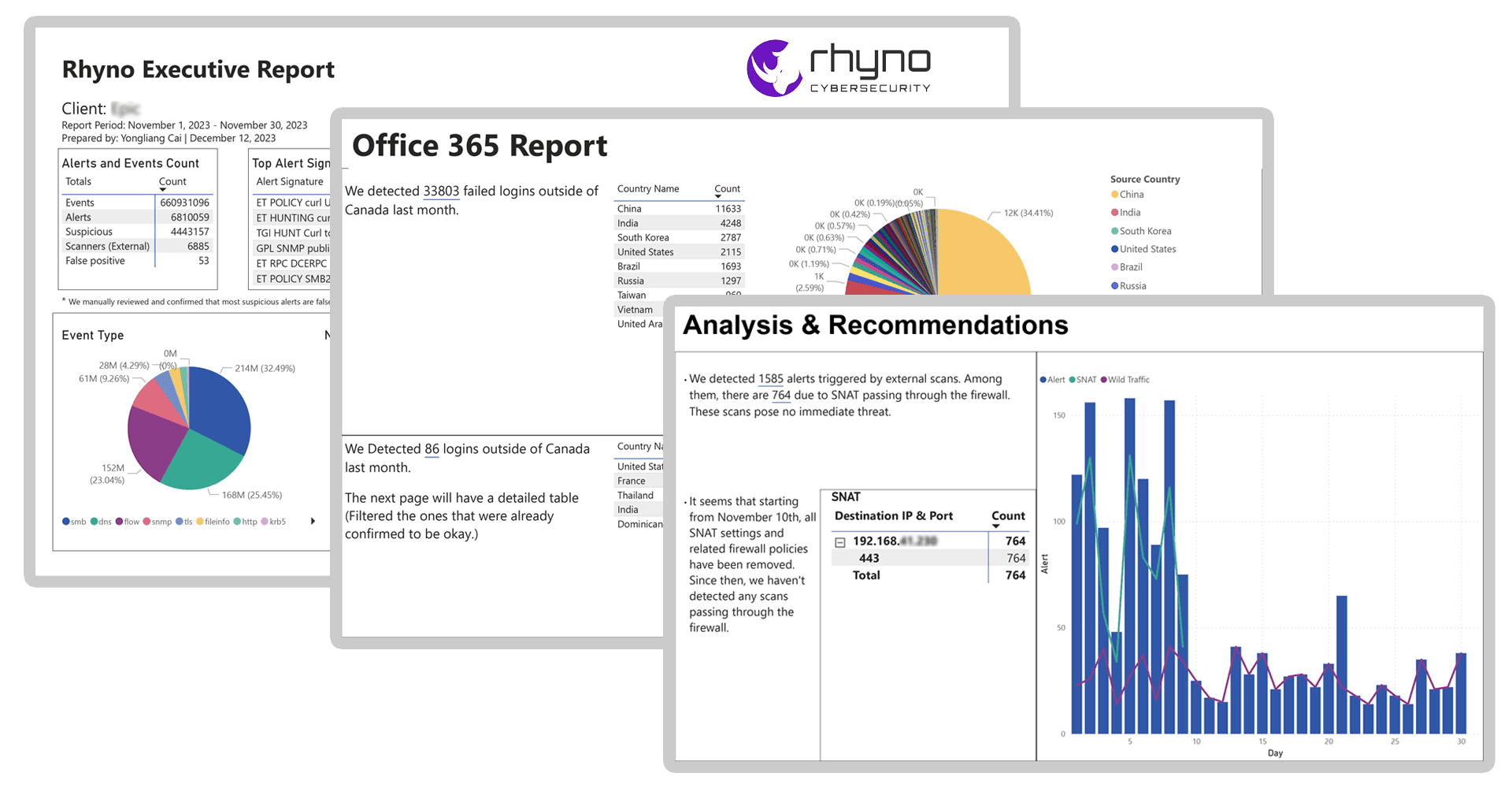
Customized Reporting
Technical details and recommendations
Why Rhyno?
Proven Expertise
We bring to the table a seasoned team with years of experience in specialized cybersecurity services. Trust us to know the best solutions for your unique needs.
Comprehensive
We don't just fix problems, we strategize. Our end-to-end cybersecurity solutions are tailored to secure your digital landscape, fostering a proactive security culture.
Client-Centric
Your business is unique and so are our services. We listen, understand, and deliver solutions that are uniquely suited to your cybersecurity needs, ensuring smooth business continuity.
Value for Investment
We believe in providing high-quality, cost-effective services. With us, you'll be investing in solutions that protect your data, enhance your reputation, and foster growth.