In the ‘Computer Security Incident Handling Guide,’ also known as SP 800-61 Rev. 2, the National Institute of Standards and Technology, generally known as NIST, provides its Cybersecurity Incident Management and Response guidelines.
NIST Incident Response Plan: The book explains how to create a cybersecurity incident response strategy and what steps a disaster recovery plan should include.
In this article, we will explore these ideas in more detail and provide an example of a strong template for a cybersecurity incident response plan.
Downloads
- Incident Response Template: https://resources.rhyno.io/free-security-incident-response-plan-template/
- NIST 800-61 Rev. 2 Guide: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
NIST Cyber Security Incident Response Strategy
With the increasing complexity and frequency of cyberattacks, ransomware attacks, and data breaches worldwide, computer security incident response has become a critical corporate activity. As a result, it is now essential to approach cybersecurity from the standpoint of response and recovery rather than prevention.
The NIST’s Cybersecurity Incident Handling Guide aims to help organizations improve their security posture and incident response capabilities via proper planning, cybersecurity training, and resource allocation.
It also emphasizes post-incident activities and data analysis in order to improve lessons learned and provide the opportunity for better detection and response next time.
In a nutshell, the guide’s overwhelming message is that every business will be attacked at some point in its existence. Therefore, the best method to strengthen your security and resilience posture is to ensure that your security staff are well-trained, that your management understands cybersecurity and incident response, and that all key stakeholders understand their roles and responsibilities.
Creating an “Incident Response Policy and Strategy” is one of the first needs outlined in the guide to developing an incident response capability. To assist you, our security specialists have created a free Security Incident Response Plan Template that you can start using right away. Try it and let us know what you think.
What exactly is a Cyber Security Incident Response Plan (CSIRP)?
A Cyber Incident Response Plan is a road map for security professionals to follow when dealing with an incident. It provides the Incident Response Team with basic guidance on what to do immediately after a cybersecurity occurrence.
This strategy should be tailored to the organization’s nature, scope, size and goals. However, some of the major criteria of this strategy are consistent across sectors and regions.
Our Security Incident Response Plan Template, based on NIST guidelines, may be used by firms wishing to develop long-term formal incident response capabilities. It includes all the necessary elements for a cybersecurity emergency response plan. It also explains how to utilize the template to get the best results.
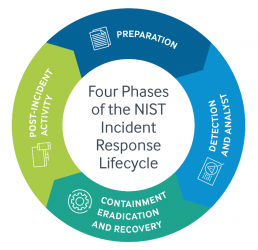
Steps in the NIST Cybersecurity Incident Response Plan.
Different Cyber Incident Response Plan Templates often specify effective incident response phases or procedures in various ways.
For additional information, see our thorough posts on the 6 Phases of Incident Response and the 7 Phases of Incident Response. However, in this article, we will stick to the four phases of the Incident Response Lifecycle as outlined by NIST.
According to NIST, the primary steps of the Cybersecurity Incident Response Process are as follows:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
We can now go through each of these phases or processes in the Incident Response Lifecycle in further detail.
1) Incident Response Preparation
As the name implies, this phase focuses on preparing the organization for a cyber-attack. It entails forming and training a security incident response team, as well as deploying technologies and resources that might prevent security problems from occurring in the first place. Although the incident response team is not responsible for procuring resources, prevention of events falls under the heading of preparation.
In the Preparation stage, NIST suggests that individuals work as advocates for good cybersecurity procedures and behaviour. Obviously, limiting the number of incidents is critical to the effectiveness of any Cybersecurity Incident Response effort.
In the Preparation Phase of the Lifecycle, the NIST Computer Security Incident Handling Guide also explains several methods that can help analyze risks and protect networks, applications, and systems.
2) Detection and analysis
While no organization can be prepared for every possible future attack, having a strategy in place to respond to the most common attack vectors is crucial.
Another factor contributing to the detection stage’s importance is that many firms cannot determine whether or not they have been attacked in reality. Because timely detection is critical, the security incident response team should be able to confirm an event promptly and then analyze its extent – what was the attack approach and what assets were impacted.
Accurately communicating the fact that the organization has been attacked to the appropriate stakeholders is also an important aspect of this step in the Incident Response Lifecycle.
3) Containment, eradication, and recovery
It is crucial to contain an event before it spreads and depletes resources. NIST emphasizes that competent decision-making is an important aspect of Containment.
Obviously, containment becomes easier and more successful when established tactics are implemented to manage and contain the event effectively. – Emphasizing the need for strong cybersecurity policies and training on how to respond to incidents in the UK and abroad.
Once the issue has been contained, eradication may be required to remediate all impacted hosts. Eradication often entails procedures such as removing malware or deactivating compromised accounts.
After eradication, the next logical step is recovery. It includes repairing hacked systems, resetting passwords, tightening the network, and replacing compromised systems and information.
4) Post-Incident Activity
This phase focuses on the lessons learned from the cyber incident. After a major event, the NIST guideline proposes conducting a “Lessons Learned” conference with key stakeholders so that the organization can collectively improve to better handle these types of situations in the future.
Proper post-event activities can shed light on crucial questions surrounding an incident, such as what occurred and how successfully the employees handled the situation. These sessions can also be used to discuss the organization’s incident response plan and its efficacy.
Meetings to discuss “Lessons Learned” should ideally be followed up by official reports that outline everything addressed in the discussion. These reports can help identify gaps within the existing rules and processes and also train new employees who will eventually join the IT security team.
NIST has highlighted several essential incident response processes above. Including these crucial elements in your Cyber Security Incident Response Plan is one of the most significant measures you can take today to transform your organization into a cyber-resilient one.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.