You are considering performing a penetration test and want to know which type of assessment is best for you. You’ve heard of black-box, grey-box, and white-box testing. Still, you aren’t sure what the differences are or which test would provide you with the highest level of security from cyber security attacks.
Penetration Testing | Some of the most frequently asked questions regarding security testing include:
- Why is it recommended to provide and utilize client credentials when testing an application?
- Is it necessary to whitelist the organization doing the penetration testing during the engagement?
- Shouldn’t the testing engagement be focused on simulating an external hacker attempting to breach our defences in order to assess our installed security properly?
- Isn’t getting insider information about the organization’s network or program before the test considered cheating?
To answer these questions, consider the benefits and drawbacks of the three forms of penetration testing: black-box, grey-box, and white-box.
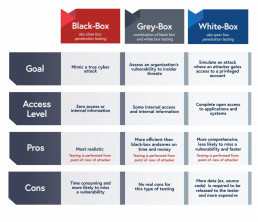
Black-Box Penetration Testing
The tester has no access to the applications or networks in a black-box engagement. Instead, to proceed, the tester must do reconnaissance to collect the sensitive information required.
This is the most accurate simulation of a cyber attack. However, it is time-consuming and carries the highest risk of overlooking a vulnerability that may occur within a network or application’s core components. A real-world attacker typically has no time limits and can spend months developing an attack plan while waiting for the right opportunity.
In addition, various defence technologies are available within networks to prevent existing vulnerabilities from being exploited. For example, some web browsers now have options that allow them to prevent an attack even if the vulnerability still exists. As a result, a change in settings or a connection from a different browser version may be all that is necessary to exploit the vulnerability.
Just because a configuration prevents a vulnerability from being discovered or exploited does not mean that it does not exist or that it is being mitigated.
Instead, it simply indicates that an external force is acting as a buffer, which can lead to a false sense of security. Someone with more time can subsequently exploit this to investigate the attack surface thoroughly.
Gray-Box Penetration Testing
Gray-box testing allows the tester to gain internal access and information. This can take the form of lower-level credentials, application logic flow charts, or network infrastructure maps, which can be used to imitate an attacker that has already breached the perimeter and gained restricted interior network access.
Starting with basic background knowledge and entry-level qualifications allows for a more efficient and streamlined approach. This reduces the time during the reconnaissance phase and allows consultants to focus their efforts on exploiting potential vulnerabilities in higher-risk systems rather than attempting to locate those systems.
Also, specific vulnerabilities can only be found by examining the source code or configuration settings. Therefore, a tester without prior information is unlikely to encounter these less common vulnerabilities.
White-Box Penetration Testing
White-box testing provides the tester with full access to all apps and systems. In addition, the tester is provided with high-level network access and the ability to see source code.
White-box testing aims to uncover potential vulnerabilities in multiple areas, including logical vulnerabilities, potential security vulnerabilities, poorly written development code, security misconfigurations, and a lack of protective mechanisms. In addition, this form of evaluation is more thorough since both internal and external vulnerabilities are reviewed from a ‘behind the scenes’ perspective that normal attackers do not have access to.
Because it takes a long time to analyze all system components properly, white-box testing is often reserved for high-risk systems or those that handle sensitive data.
A Comparison of the Black-Box, Grey-Box, and White-Box
Which Approach Is Best For Your Company?
A penetration test aims to detect possible weaknesses in your systems before an attacker does. But, of course, the tester’s level of access and proficiency will impact how thorough and reliable the test results are.
Defining the problems you want to address is critical to developing a tailored approach. Doing so can help you fulfill the necessary security standards while providing the best value for your investment in penetration testing.
Rhyno Cybersecurity’s team of highly skilled and OSCP-certified ethical hackers customize each engagement to guarantee the most comprehensive penetration testing possible. We understand that not all architectures or applications fit into a predefined box. Developing a solution that works best for your business requires an adaptive testing technique.
Only 5% of our testing is automated. The remaining 95 percent consists of manually simulated real-life assaults. So whether you need a black box, gray box or white box assessment, Rhyno Cybersecurity has the knowledge and skillset to help you protect your system and prevent costly data breaches.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.