A massive phishing simulation has revealed that roughly 70 per cent of global users working in the public sector are likely to enter password credentials after clicking on a malicious email.
The tournament, organized by Quebec-based Terranova Security, revealed that approximately 20 per cent of global employees are still quick to click on phishing email links, a significant increase from the 11 per cent figure posted after the inaugural tournament in 2019. It’s an alarming sign since most of the tournament participants already had a phishing simulation program in place, says Theo Zafirakos, CISO at Terranova Security.
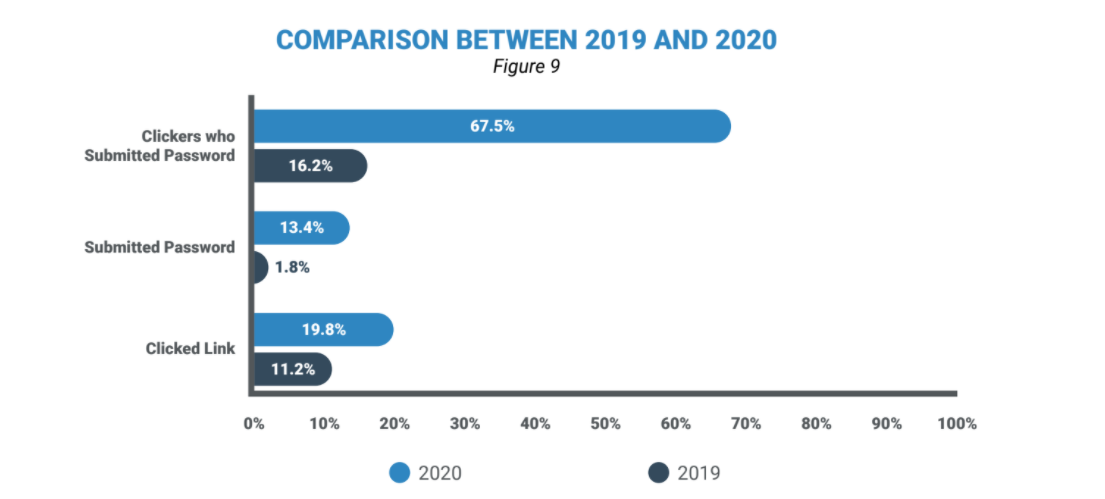
Not even October’s Cybersecurity Awareness Month had enough sway to reduce the numbers. In Canada, nearly 25 per cent of employees participating in the second annual Gone Phishing Tournament clicked on fishy email links, sending them further down a slippery slope of self-harm. The world is in the grips of a second COVID-19 wave, and the remote work era has not been an easy road to travel, which is exactly why it was the perfect backdrop to the simulation, Zafirakos explained.
Also:
Nearly 70% of fraud phishing attacks are directed at Canada: RSA report [Full story]
“We used a sophisticated template this time for the tournament,” Zafirakos told IT World Canada after the tournament’s results were released. “A real attacker will take advantage of the remote work situation.”
The templates were supplied by Microsoft and reflected the remote work era that still looms over the working world. Their difficulty also got bumped up compared to last year’s simulation, Zafirakos noted. Terranova Security rated the simulation medium-high for complexity.

North America struggled the most with the simulation, posting a 25.5 per cent click rate and an 18 per cent overall credential submission rate. In Canada, those numbers were very similar at 24 and 17 per cent respectively. Thanks to a generally stronger approach to security and privacy among enterprises, Europe’s workers posted much lower click and submission rates at 17 and 11 per cent, respectively.
Joining the public sector at the top with a click-to-submission ratio of over 70 per cent was the transport sector. Only two industries globally posted a click rate lower than 15 per cent: Finance and insurance and education. The two sectors also performed better than other organizations in terms of credential submission, scoring well below the tournament average at 8.7 per cent and nearly 8 per cent, respectively. The phishing simulations only targeted staff and other faculty in the education space, not students, Zafirakos confirmed.
Firms struggling to keep click rates down need to revisit their training and education policies, he noted. Consider continuous awareness training, he suggested – it doesn’t even have to be mandatory (although some companies have opted to make them so). And perhaps more important than anything, make those discussions and exercises engaging. Nothing hurts awareness training more than a lifeless exercise.
Despite some of the alarmingly high click rates, Zafirakos says he was pleased to see some organizations flex their incident response muscles upon discovering a malicious email deployed through the tournament.
“Some users and organizations reacted very quickly and even blocked the test,” he said, hinting at Terranova’s future ambitions to stress test organizations’ incident response policies. “That is one of the things we want to [one day] test specifically, but it was great to see that when something suspicious gets reported to someone, the organization reacts, and it contributes to the overall protection of the organization and the people themselves.”