Attackers can exploit various controller flaws, putting manufacturing operations at risk and potentially causing harm to property. Unfortunately, many companies overlook the importance of patching their controllers, despite the potential consequences. This oversight is primarily driven by the high priority placed on network reliability by ICS engineers.
[FREE E-BOOK] The Definite Blueprint for Cybersecurity in Manufacturing
Organizations operating in the industrial sector are increasingly compelled to prioritize the protection of industrial control systems (ICS), with a specific focus on safeguarding industrial controllers, due to the ever-growing prevalence of cyber threats.

The industry can no longer turn a blind eye to the increasing occurrence of cyber incidents within ICS networks. However, safeguarding these networks presents unique challenges for security professionals, as they differ from conventional IT networks. In order to effectively protect ICS networks, it is imperative to have a comprehensive understanding of their operational mechanisms, the diverse technologies they employ, and their hidden functionalities.
Industrial networks are no longer protected from attacks by air gaps.
Until recently, industrial networks have traditionally relied on air gapping as a means to isolate themselves from the external world.
In theory, an air gap is considered a highly effective security measure. By disconnecting the business network and internet access, it aims to prevent intruders from gaining unauthorized access to the industrial network.
However, in today’s interconnected and converged IT and operational technology (OT) landscape, relying solely on air gapping is no longer a practical or feasible approach.
IIoT (Industrial Internet of Things) and Industry 4.0 trends encourage enterprises to enhance operational systems and optimize current procedures in order to enable more linkages between offline and online operations.
As a result of this interconnection, previously isolated operational environments are now exposed to heightened vulnerability to cyber threats.

Industrial process flaws raise the risk of cyberattack
Industrial processes face a heightened risk of cyberattacks due to various flaws in software, hardware, and inherited vulnerabilities within the original architecture of ICS networks.
Industrial controllers, such as programmable logic controllers (PLCs), remote terminal units (RTUs), and distributed control system (DCS) controllers, are specialized computers responsible for overseeing and managing industrial machinery and processes throughout their operational lifespan.
For the most part, people attempting to access and change the state of these controllers do not need to be authenticated. Furthermore, the vast majority do not permit encrypted communication. As a result, the industrial process is open to anyone with network access, including hackers, hostile insiders, and irresponsible employees. Naturally, that poses a risk to the company.
Attackers can utilize the numerous controller vulnerabilities to sabotage operations and harm systems. However, because many ICS engineers put network stability above all else, the majority of organizations don’t patch controllers. Industrial controller patches can result in disruptions or downtime, reliability concerns, and other operational challenges, which makes them challenging to apply.

Lack of control and visibility in networks for industrial control systems
The creation of ICS networks predates the existence of cyber threats, resulting in a lack of consideration for security during their development. As a result, these networks are in need of the same level of visibility and security measures that are now commonplace in corporate IT networks. However, they still lag behind in implementing such measures. Automated asset management and configuration controls are often overlooked in ICS setups, further exacerbating the issue.
How can you take the necessary precautions to secure your network’s assets without having a complete grasp of the assets’ configuration, the firmware they run, the code and logic they execute, and which ones are vulnerable?
Remember that these settings employ specialist operating technologies (OT) from suppliers like GE, Siemens, Schneider Electric, Rockwell, etc. They don’t function the same way as IT technology. They employ various hardware, software, and networking protocols. Therefore, these environments do not suit IT security solutions well.
Security of control-layer protocols is challenging.
One of the major technical difficulties we have while trying to safeguard ICS networks is the fact that these networks employ many communication protocols.
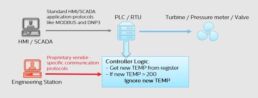
For programmable logic controllers, the IEC-61131 standard is implemented differently by each OT vendor. Because these implementations are so infrequently disclosed, keeping an eye on these crucial operations is challenging.
The attacker may attempt to alter how the process is carried out because the main objectives of most ICS hacks are to cause bodily harm or operational problems.
The controller logic plays a crucial role in specifying the process flow and its limitations. While a predefined set of process parameters can be modified through HMI/SCADA applications, altering the controller logic is the most straightforward and efficient method to implement such modifications.
Contrary to what most people think, this is not hard. An attacker can quickly download control logic to an industrial controller or modify its settings once they have gained access to the network.
There is no standardized method for observing control-layer activity since attackers carry out these operations via proprietary vendor-specific protocols. As a result, alterations made by an attacker (or even those brought on by human error) may go undetected until harm is done.
How to get around the problems with unprotected OT networks
The majority of ICS assaults do not necessitate the use of software vulnerabilities because of the design of OT networks and the absence of fundamental security measures like authentication and encryption. Once an attacker reaches the OT network, they can use a compromised machine to launch an attack on industrial processes.
Due to the lack of visibility and security measures in ICS networks, industrial processes and crucial infrastructures are in danger. Use specialized monitoring and control technology to stop unlawful process alterations and defend ICS against outside threats.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.