Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motivations, targets, and attack patterns. In the fight against threat actors, threat intelligence helps us to make quicker, more informed, data-backed security choices and shift our behaviour from reactive to proactive.
Advanced persistent threats (APTs) and defenders constantly strive to outmaneuver each other in cyber security. Therefore, data about a threat actor’s next step is critical for proactive defence tuning and preventing subsequent assaults.
Organizations are rapidly understanding the benefits of threat intelligence, with 72 percent expecting to boost expenditure on threat intelligence in the coming quarters.
However, there is a distinction to be made between perceiving and receiving value. Most businesses today concentrate on the most basic use cases, such as integrating threat data feeds with existing networks, IPS, firewalls, and SIEMs – without fully using the insights that intelligence can provide.
Companies that limit their threat intelligence to this basic level are missing out on substantial benefits that might significantly boost their security postures.
The following are the reasons why threat intelligence is essential:
Illuminates the unknown, allowing security professionals to make better judgments
Enables stakeholders in cyber security by disclosing attacker motivations as well as their strategies, approaches, and processes (TTPs).
Assists security professionals in better understanding the decision-making process of the threat actor.
Enables business stakeholders such as executive boards, CISOs, CIOs, and CTOs to spend intelligently, reduce risk, become more efficient, and make faster choices

Who Stands to Gain from Threat Intelligence?
Threat intelligence helps companies of all sizes evaluate threat data in order to understand their adversaries better, respond to crises faster, and anticipate a threat actor’s next move. This data enables SMBs to achieve levels of protection that would otherwise be unattainable. On the other hand, enterprises with huge security teams may decrease costs and necessary skills by using external threat intelligence and making their analysts more effective.
Threat intelligence provides distinct benefits to every member of a security team, including:
Executive Management. Sec/IT Analyst. SOC. CSIRT. Intel Analyst.
Lifecycle of Threat Intelligence
The intelligence lifecycle is the process of transforming raw data into final intelligence that can be used for decision-making and action. You may come across several slightly different variations of the intelligence cycle. Still, the purpose remains the same: to guide a cyber security team through the conception and implementation of a successful threat intelligence program.
Threat intelligence is challenging to manage since threats are continually developing, requiring firms to react swiftly and take decisive action. However, the intelligence cycle provides a structure for teams to maximize their resources and respond effectively to today’s threat scenario. This cycle has six parts that culminate in a feedback loop to stimulate ongoing improvement:
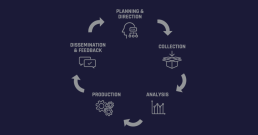
Let’s go over the six stages below:
1. Prerequisites
The requirements stage is critical in the threat intelligence lifecycle because it establishes the roadmap for a particular threat intelligence operation. The team will agree on the goals and approach of their intelligence program at this planning stage, depending on the stakeholders’ demands. The group could set out to discover the following:
Who the assailants are, and what motivates them
What is the attack surface, and what steps should be taken to reinforce defences against future attacks?
2. Gathering
After defining the criteria, the team gathers the information needed to meet those objectives. Depending on the aims, the team would often search out traffic logs, publicly available data sources, relevant forums, social media, and industry or subject matter experts.
3. Preparation
After gathering the raw data, it must be converted into a format appropriate for analysis. This usually requires arranging data points into spreadsheets, decrypting files, translating information from foreign sources, and analyzing the data for relevance and dependability.
4. Evaluation
After the dataset has been processed, the team must do a comprehensive analysis to discover answers to the requirements phase questions. During the analysis phase, the team also works to translate the dataset into action items and valuable suggestions for stakeholders.
5. Publication
The threat intelligence team must transform their findings into a consumable style and deliver the results to the stakeholders during the dissemination phase. The audience determines the manner in which the analysis is provided. Most suggestions should be given briefly, without confusing technical jargon, in a one-page report or a brief slide deck.
6. Comments
The last stage of the threat intelligence lifecycle entails gathering input on the delivered report to assess whether any changes are required for future threat intelligence activities. Stakeholders’ priorities, the frequency with which they want to receive intelligence reports, and how data should be shared or presented may all vary.
Threat Intelligence Comes in Three Forms
In the last section, we covered how threat intelligence may provide us with information about present or possible threats. The data might be as simple as a rogue domain name or as complicated as an in-depth profile of a recognized threat actor. Keep in mind that there is a maturity curve for intelligence, which is represented by the three levels stated below. The background and analysis of CTI get deeper and more complex with each level, catering to diverse audiences and becoming more expensive.
- Tactical awareness
- Intelligence operational
- Intelligence on strategy
Tactical Danger Intelligence Challenge: Organizations frequently concentrate on a single threat.
Objective: Gain a more comprehensive understanding of dangers in order to fight the underlying issue.
Tactical intelligence deals with the near future. It’s technological in nature and finds basic signs of vulnerability (IOC). Bad IP addresses, URLs, file hashes, and domain names are examples of IOCs. It can be machine-readable, meaning security solutions can use it via feeds or API integration.
Tactical intelligence is the simplest to create and is virtually usually automated. As a result, it may be discovered using open-source and free data feeds. Still, it often has a very short lifespan since IOCs such as malicious IP addresses or domain names might become obsolete in days or even hours.
It is crucial to realize that just subscribing to intelligence feeds might result in a large amount of data but provides no means of digesting and strategically analyzing the dangers that are relevant to you. Furthermore, false positives can also arise when the source is not timely or accurate.
Questions to consider:
- Do you have a feed from the IOC?
- Are International Olympic Committees (IOCs) timely and relevant?
- Is malware analysis done automatically?
Objective: Conduct campaign monitoring and actor profiling to better understand the attackers.
Cyber security specialists study their enemies in the same manner that poker players study each other’s peculiarities to predict their opponent’s next move.
Every attack has a “who,” a “why,” and a “how.” The “who” is referred to as attribution. The “why” is referred to as the motive or aim. The “how” is made up of the threat actor’s TTPs. These characteristics, when considered together, create context, and context provides insight into how adversaries organize, execute, and maintain campaigns and significant operations. This understanding is referred to as operational intelligence.
Machines cannot generate operational threat intelligence on their own. Instead, human analysis is required to turn data into a format that customers may easily use. While operational intelligence necessitates more resources than tactical intelligence, it has a longer useful life since adversaries cannot readily alter their TTPs as they may change their tools, such as a specific type of malware or infrastructure.
Operational intelligence is precious for cyber security experts that operate in a SOC (security operations center) and are in charge of day-to-day operations. Cyber security disciplines, including vulnerability management, incident response, and threat monitoring, consume the most operational intelligence since it helps them become more skilled and successful at their responsibilities.
Sharing is Caring!
You are welcome to put this blog article on your website, provided you also append an active link to our website “Source: https://resources.rhyno.io”
For media enquiries, contact us at [email protected].
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.