ZuoRAT Malware attacks Small office/home office (SOHO) routers, a previously unknown remote access trojan as part of a sophisticated operation aimed at North American and European networks.
ZuoRat Malware: According to Lumen Black Lotus Labs experts, this malware allows the actor to pivot into the local network and access more LAN devices by hijacking network communications to retain an undetected presence.
The covert operation targeted ASUS, Cisco, DrayTek, and NETGEAR routers and is said to have started in the early months of the COVID-19 outbreak in 2020. As a result, it went unnoticed for more than two years.
Consumers and remote employees commonly use SOHO routers. Still, they are rarely monitored or patched, making them one of the weakest points of a network’s perimeter.
The malware has been identified as a significantly altered form of the Mirai botnet, whose source first surfaced in October 2016 and enables traffic collection, network communication hijacking, and comprehensive target network surveillance.
The malware has been described as a substantially modified variant of the Mirai botnet, whose source emerged in October 2016 and allows for extensive surveillance of target networks, traffic collecting, and network communication hijacking.
See article on Managed Detection and Response.
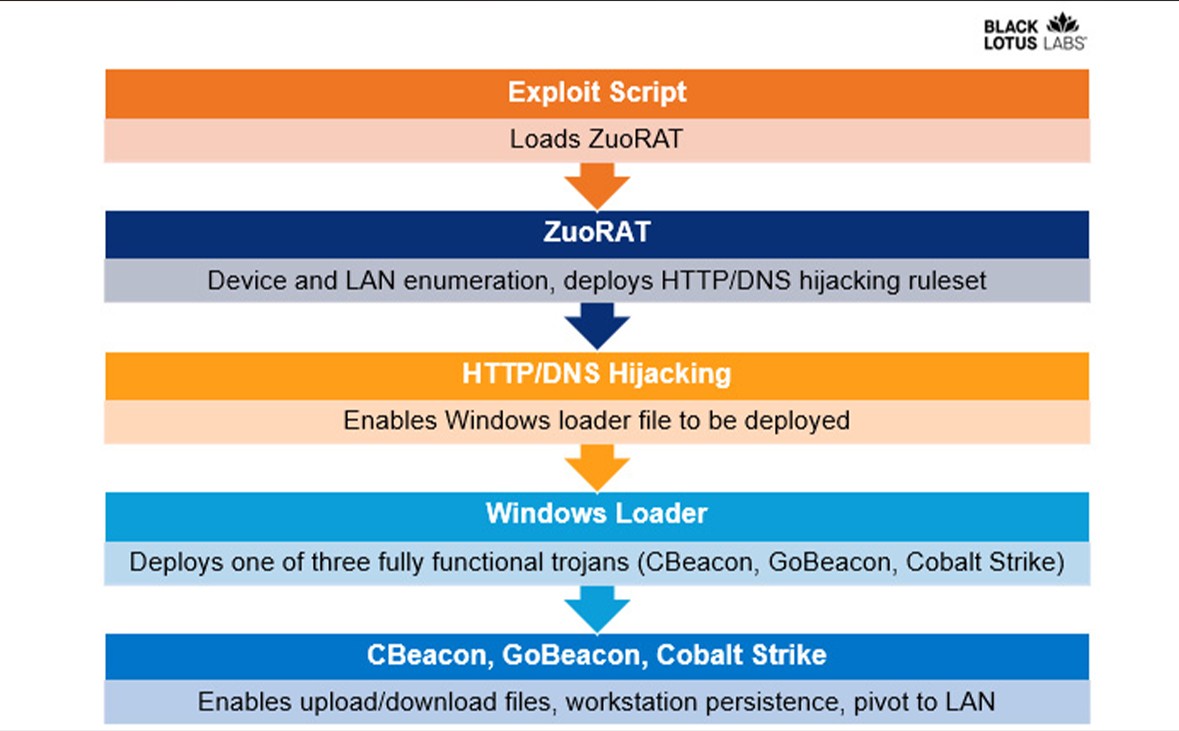
ZuoRAT Malware, according to researchers, is a man-in-the-middle attack tool that can perform DNS and HTTPS hijacking attacks based on predetermined rules, enumerate hosts and internal LANs, and collect packets being sent via compromised devices.
The adversary may be able to monitor user internet behaviour by using a function to harvest TCP connections through the FTP and web browsing ports of 21 and 8443, respectively, which are also included in the compromised router.
With the assistance of ZuoRAT’s additional features, attackers can keep an eye on DNS and HTTPS traffic with the intention of hijacking requests and rerouting victims to malicious domains using pre-made rules generated and stored in temporary directories to evade forensic analysis.
The hackers also used a virtual private server to drop the original RAT vulnerability and infected routers as proxy C2 servers, so these are not the only steps they used to hide their activity. In addition, the attacks rely on a complex, multistage C2 architecture.
The staging server has been seen displaying seemingly innocent information to further evade discovery, including one occasion when it imitated the website “muhsinlar.net,” a propaganda platform created for the Turkestan Islamic Party (TIP), an Islamist Uyghur group with Chinese roots.
Additionally, the threat actor can go from the compromised router to additional workstations in the network using the hijacking functionality to install the loader payload that starts the custom-made trojans.
Although an investigation of the artifacts showed potential allusions to the Chinese region of Xiancheng and the employment of Alibaba’s Yuque and Tencent for command-and-control, the name of the antagonistic collective behind the effort is still unknown (C2).
The ZuoRAT Malware has become a new cybersecurity threat
According to Black Lotus Labs, the operation’s complex and evasive character, as well as the strategies used in the attacks to remain undetected, indicate possible nation-state action.
The researchers came to the conclusion that the ZuoRAT campaign’s demonstrated capabilities—gaining access to SOHO devices of various makes and models, gathering host and LAN data to inform targeting, sampling and hijacking network communications to potentially gain persistent access to in-land devices, and purposefully stealth C2 infrastructure using a multistage siloed router to router communications—point to a highly sophisticated actor.
Link to Lumen article: https://blog.lumen.com/zuorat-hijacks-soho-routers-to-silently-stalk-networks/
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.